
Corporate Threat Watchbots
Advanced AI-driven Cyber-Surveillance Platform
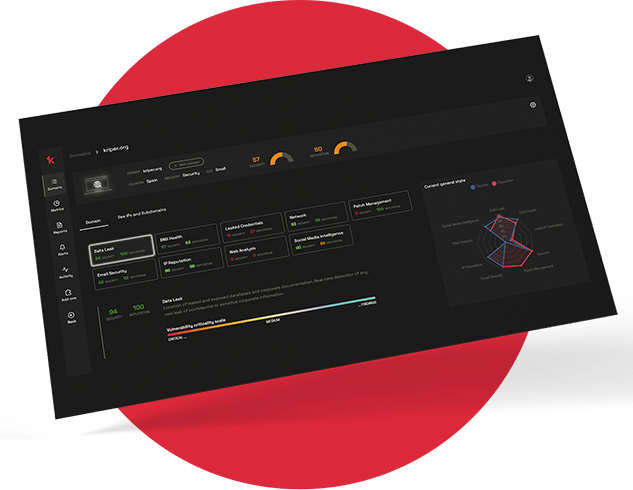

If a cybercriminal can see it,so can we.

Kartos is an automated monitoring tool, independent of third-party applications, non-intrusive and continuous, that provides data and alerts on open and exposed vulnerabilities in real time by simply entering the domain of the company to be monitored.

Corporate Threat Watchbots
Kartos is an automated monitoring tool, independent of third-party applications, non-intrusive and continuous, that provides data and alerts on open and exposed vulnerabilities in real time by simply entering the domain of the company to be monitored.
False positives are now history
Kartos’ unique AI-based contextual tags to completely eliminate false positives in search results.
- Ciber-intelligence: Locate your organisation's open and exposed information and vulnerabilities on the Internet, the Deep web, the Dark web and Social Networking sites.
- Cybersecurity: Extends the cyber security strategy beyond the corporate IT perimeter.
- Scoring: Corporate cybersecurity score based on objective data taken in real time.
- Compliance: Corporate compliance based on real-time objective data.
- More protection against phishing and ransomwareDetection of phishing, fraud and scam campaigns on social networks
- Do you need Brand Protection?Detection of brand impersonation and fraudulent use of intellectual and industrial property.
- Have your credentials been leaked?
- Do you comply with the regulations?
- Third Party Risk
- External Attack Surface (EASM)

Detection of phishing, fraud and scam campaigns on social networks
- DNS Health: Squatting, Social Networking, domains and subdomains.
- AI analysis of the phishing, fraud and scam campaign and all its infrastructures in different countries.
- Transfer of IPs, domains and URLs information necessary to deactivate the campaign.
- Control and monitoring of the entire campaign and all its infrastructures.
- Takedown service


Detection of brand impersonation and fraudulent use of intellectual and industrial property.
- Social Media Intelligence: Telegram, Facebook, X, LinkedIn, Instagram, Youtube and Spotify.
- Tracking of social networks for accounts containing cloned or similar corporate identity elements.
- Analysis of the profiles detected.
- Issuance of real-time alerts.
- Continuous monitoring until deactivation.
- Takedown service

Credential Leak
- Location of leaked and exposed corporate credentials.
- Location of compromised corporate email accounts.
- Detection of the security breaches causing the leakage


Regulatory compliance
- Data protection
- Certifications and standards: ENS, ISO 27001, PCI…
- Assessment of compliance with all external and certain internal attack surface controls.
- Assistance in the implementation or renewal of certifications.
- Compliance testing based on objective data taken in real time for third parties and legal claims.

Third party risk and value chain control
- Real-time value chain risk control
- Non-intrusive, no third party permission needed
- Objective data obtained in real time
- Complement to traditional valuation tests such as pentesting or due diligence for mergers or acquisitions
- Third party cybersecurity scoring
- Third party compliance


External Attack Surface Management (EASM)
- Threat Hunting
- Net
- CVEs
- Localization of filtered and exposed databases
- Locating leaked and exposed corporate information
- Patch management
- IP Reputation
- Web security
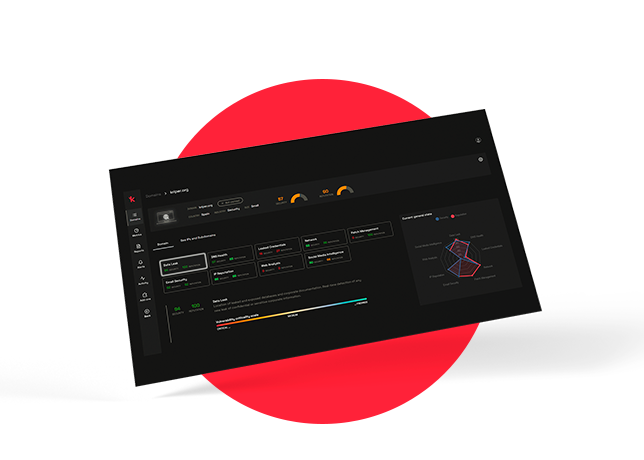
Features kartos●
100% AINo HumInt
The use of Kartos’ artificial intelligence automates the management of information, guaranteeing confidentiality and allowing the continuous detection of incidents and alerts in real time, without human intervention.
100% AINon Intrusive
The search is done outside the company perimeter, on the Internet, Deep and Dark web, forums, social networks and open sources. It locates information that cybercriminals could find, and delivers it to companies for their protection, without carrying out attacks.
Informationin real time
Speed in detecting and defending against vulnerabilities is critical. The longer it remains open, the easier it is for a cybercriminal to exploit. Automation makes it possible to detect and deliver information in near real time.
Customization offeatures
A flexible licensing model allows for an intelligence platform that is almost tailor-made for each company, combining licenses for in-house protection and risk detection in third parties according to their access to critical information.
Simplicity in theinterpretation and use
Artificial Intelligence automatically configures the platform according to the company’s domain. No sources, parameters or queries are required. Results are delivered in stages for experts and non-experts.
Unlimited users foreach license
Each company has multiple profiles that need access to information according to their role. This belongs to the company, so the number of users and profiles is not limited, offering maximum flexibility in permissions and alerts.

Corporate Threat Watchbots
Analysis of 11 Vectors
- Algorithms
- Certificates
- Services / IoT / VoIP
- DNS Health/Phishing
- Patch Management
- IP Reputation
- Web Security
- Email Security
- Document Leaks
- Credential Leaks
- Social Networks
Testing your companydoesn't cost anything
1,509.033
LEAKS FOUND IN 30 DAYS
100M
OF LINKS REVIEWED DAILY
2.500
DEEP WEB
Discover the threat before anyone else does

Heads of Cybersecurity and CISO

Kartos resolves the management of the organisation's exposure to its own and third-party threats in a single automated, autonomous and continuously operating platform. Kartos allows the CISO to implement a proactive cybersecurity strategy that identifies threats before they materialise into attacks and simplifies their management, strengthening corporate protection, facilitating data-driven decision-making and the involvement of the rest of the board in the strategy and ensuring legal compliance.

Third Party Risk Assessment
Third Party Risks
Companies have always needed third parties to develop their business. But the transformation processes in which most of them are immersed mean that the dependence and level of integration of these third parties is increasing and that they have practically become part of their structure, thus extending their attack surface. Kartos provides the necessary information to extend the requirement in terms of risk level to these third parties, and makes it possible to assess their cybersecurity at any time, without the need for authorisation and under objective parameters.
Supplier Evaluation
Assessing the level of supplier cybersecurity risk is close in importance to the well-known credit risk assessment. This is due to the enormous impact it can have on the corporate risk of companies and the economic and operational cost that an attack can have. Kartos provides the internal departments of companies whose core business is the evaluation of third party risks with the necessary information to determine the level of cybersecurity risk in supplier evaluation, approval and assessment processes.

