Today, we can observe threats evolving rapidly and attackers operating with sophistication. Cyber surveillance has become an essential pillar for anyone responsible for an organization’s security.
If you are a CISO or security manager, simply reacting is no longer enough: you must anticipate, monitor, and continuously manage risk exposure.
Before delving deeper into this topic, let’s talk about Kartos, Enthec’s solution designed for businesses. Kartos is a cyber surveillance tool designed to provide continuous insight into your company’s exposure to threats, helping discover vulnerabilities, validate which risks are real, and prioritize mitigation actions.
Kartos is part of the operational muscle a CISO needs to sustain a modern cybersecurity program.
What is cyber surveillance: definition and scope
We could say that the most useful definition of cyber surveillance today is:
The practice of continuously monitoring the digital environment (both internal and external) for signs of threats, data exposure, emerging vulnerabilities, or suspicious activity, to respond as quickly as possible and reduce impact.
But that definition does not fully capture its strategic meaning. Cyber surveillance is not just about “being vigilant,” but about doing so in a structured, automated way, focusing on what really matters to the company.
In more technical terms, cyber surveillance falls under the Continuous Threat Exposure Management (CTEM) framework, which goes beyond one-off vulnerability scans.
Why every CISO needs to incorporate cyber surveillance
1. The pace of risk doesn’t wait.
Modern organizations typically identify tens of thousands of potential exposures each month. For example, according to a study by XM Cyber, an average of 15,000 exploitable exposures is identified across many organizations, with some exceeding 100,000.
With that volume, it is not feasible to manually review or prioritize without automating the risk criteria.
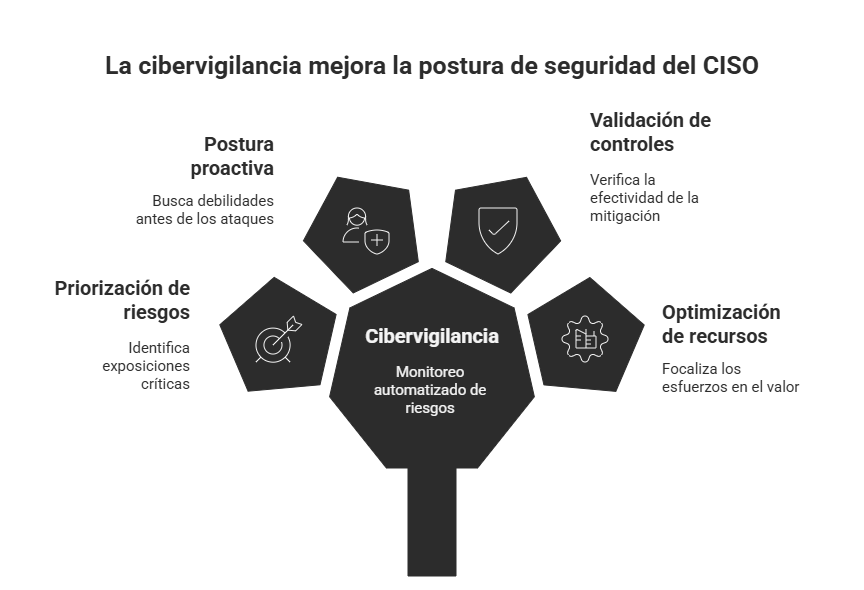
2. From reactive to proactive
Traditional security strategies (periodic scans, ad hoc tests) tend to fall behind in the face of constant change. CTEM, supported by cyber surveillance, allows us to move from a model in which we act after detecting an incident to one in which we look for weaknesses before they are exploited against us.
3. Risk-based and business-based approach
Not all vulnerabilities have the same impact. Cyber surveillance allows us to differentiate which exposures are critical to the business (for example, those that compromise sensitive data or critical processes) versus those that have little effect.
4. Continuous validation of controls
Detecting vulnerabilities is good, but how do you know if your controls effectively mitigate them? A cybersecurity surveillance solution like Kartos not only discovers flaws but can also validate whether the controls actually work in real-world scenarios through simulated attacks.
5. Alignment with the security strategy and resource optimization
A CISO cannot waste effort addressing minor risks. Properly implemented cyber surveillance allows a focus on the budget, team, and technical resources on what adds the most value.
How to apply cyber surveillance within the CTEM framework: key steps
For cyber surveillance to be effective, it should be framed within a clear CTEM cycle. The following are the recommended steps:
1. Scoping (delimitation)
Define which parts of the environment you are observing: assets, services, applications, cloud, external networks, etc. Set clear boundaries based on business value.
2. Discovery / Active Monitoring
This is where cyber surveillance, in the strict sense, comes in:it is crucial for detecting new assets, incorrect configurations, external exposures, leaked credentials, and suspicious activity. This monitoring must be automatic and continuous.
3. Prioritization of exposures
Not all detections warrant the same urgency. Here, each finding is evaluated based on ease of exploitation, potential impact, and business context. Cyber surveillance provides data (for example, whether that point is under attack) to improve this prioritization.
4. Validation / Simulation of attacks
It is not enough to see the vulnerability: It is necessary to validate whether it can actually be exploited. . Controlled simulations or advanced network teaming tests verify whether the risk is real. This bridges the gap between detection and action.
5. Remediation / Mobilization
Once validated, resources are allocated to mitigate or eliminate the exposure. Cyber-monitoring continues to confirm that the remediation is effective and does not generate side effects.
This cycle does not end: it returns to step 1 with continuous adjustments to maintain constant monitoring of the system.
Specific advantages offered by cyber surveillance
- Greater visibility without blind spots: what was previously unseen is revealed.
- The faster the earlier an exposure is detected, the smaller the window of risk.
- Reduction of actual risk: It is not enough to detect; it is also necessary to act reasonably and quickly.
- Continuous improvement: strategy evolves as threats and assets change.
- Better resource prioritization based on real risk avoids focusing efforts on irrelevant threats.
- Communication to the committee/managers: With quantified data on mitigated exposures, the CISO can demonstrate real impact on the business.
How Kartos fits into the CISO’s strategy
Kartos, as a cyber-surveillance solution for businesses, is designed to be an active part of the CTEM cycle.. Some of its advantages are:
- It integrates detection, validation, and prioritization into a single platform.
- It provides a continuous view of the exposure, not just spot scans.
- It adapts to changes in the environment (new services, cloud environments, structural changes).
- It allows the CISO to demonstrate quantitatively how risk decreases over time.
- Connects with operational security processes (tickets, actions, tracking).
When cyber surveillance becomes an operational security muscle (rather than merely an informational layer), the CISO gains control over digital exposure.
If you are interested in learning how Kartos can fit into your organization and deploy an effective cyber surveillance program, you can request a demo or a personalized consultation. Contact us and we’ll show you how to transform your security.
Today, more than ever, a CISO cannot rely solely on one-off scans or reacting only after an incident occurs. Cyber surveillance, understood as continuous, automated, and risk-based monitoring, is becoming essential for monitoring the digital landscape and reducing exposure.
By integrating it into a structured cycle like CTEM, cyber surveillance ceases to be an auxiliary function and becomes the backbone of the security strategy. In this context, solutions like Kartos by
Enthec can offer a real advantage: constant visibility, practical validation, and prioritization based on business criteria.
Act today. Strengthen your security with real and continuous cyber surveillance.


