Cybersecurity has been making it clear for years that simply “having protection” is no longer enough. Firewalls, antivirus software, and occasional audits are still necessary, but the current context goes far beyond that.
Threats change rapidly, new vulnerabilities emerge every week, and the digital footprints of businesses and individuals grow constantly. In this scenario, CTEM (Continuous Threat Exposure Management) is establishing itself as one of the most realistic and effective approaches to continuously manage digital risk.
Talking about CTEM is not talking about a specific tool, but about a way of understanding cybersecurity as a living processunder constant review and adaptation. And this is where cyber surveillance solutions like Kartos and Qondar, developed by Enthec, fit naturally as pillars of a modern Continuous Threat Exposure Management strategy.
Why traditional cybersecurity is no longer enough?
For years, many organizations have relied on periodic reviews: cybersecurity audits, annual inspections, periodic penetration tests, or reviews conducted after an incident. The problem is clear:
Threats don’t wait.
Furthermore, today it’s not just servers or internal networks that need protecting. There are forgotten domains, leaked credentials, mentions on underground forums, exposure on social media, and misconfigured cloud services. All of this is part of the attack surface, and it changes constantly.
This is where the CTEM approach makes sense.
What is CTEM (Continuous Threat Exposure Management)?
CTEM defines a working model that seeks to continuously identify, analyze, and reduce the real risks to which an organization or person is exposed.
It’s not just about detecting technical vulnerabilities, but about answering very specific questions:
- What digital assets are currently exposed?
- What sensitive information is circulating out of control?
- Which threats are real and a priority?
- What risks are growing without anyone monitoring them?
The key is in the word ‘continuous’: . CTEM is not a snapshot but a continuous monitoring process.
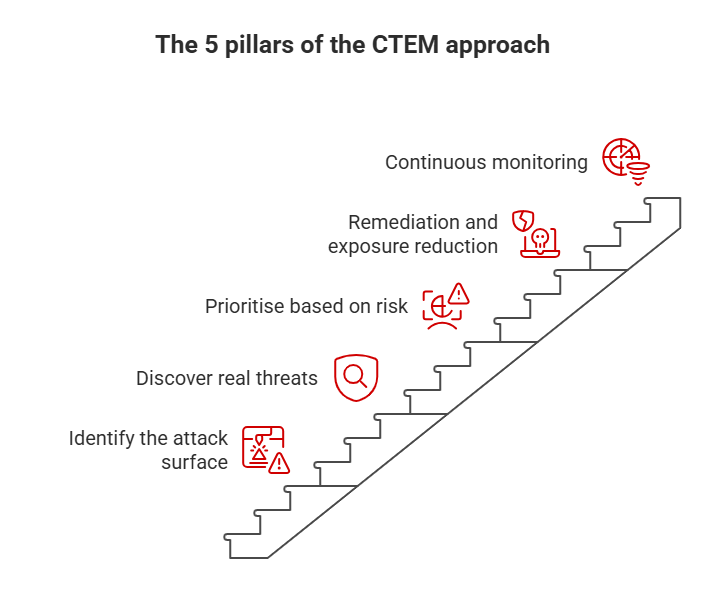
The five pillars of the CTEM approach
Continuous identification of the attack surface
The first step in CTEM is understanding what is actually exposed. Often, even companies themselves are unaware of all their digital assets: outdated subdomains, misconfigured cloud services, forgotten profiles, or even publicly accessible personal information.
A CTEM strategy involves constantly mapping that digital surface, not only at the beginning of a project.
Discovery of real threats
Not all vulnerabilities carry the same weight. CTEM focuses on exploitable threats, not only in endless lists of theoretical failures.
This is where cyber surveillance occurs: observing what is happening in forums, underground markets, leaks, or suspicious mentions related to a brand or a person.
Risk-based prioritization
One of the most common mistakes in cybersecurity is trying to fix everything at once. CTEM proposes prioritizing based on impact and actual probability, not just technical severity.
This allows resources to be dedicated to what really matters and reduces operational noise.
Remediation and exposure reduction
Detecting without acting is useless. The CTEM approach involves progressively reducing exposure by closing access, removing exposed information, or correcting insecure configurations.
Constant monitoring and continuous improvement
The cycle never ends. Continuous management involves starting over, reviewing, adjusting, and learning from each new finding.
CTEM applied to companies: Kartos as the cyber-surveillance solution
In the corporate sphere, Kartos, Enthec’s enterprise-oriented solution, is a perfect CTEM tool.
What does Kartos contribute to a CTEM strategy?
Kartos allows organizations to:
- Monitor their digital exposure in real time.
- Detecting data leaks, compromised credentials, or mentions in non-visible environments.
- To have a clear and centralized view of external risk.
- Anticipating incidents before they become a bigger problem.
From CTEM’s perspective, Kartos is not an isolated solution but a continuous monitoring system that feeds into cybersecurity decision-making.
This is especially relevant for companies with an online presence, multiple domains, cloud services, or remote teams, where the attack surface grows almost uncontrollably.
You might be interested in→ 9 healthy digital habits that will protect you from impersonation and data breaches
CTEM for individuals: Qondar and the personal protection
Managing ongoing threat exposure isn’t exclusive to businesses. Professionals, managers, content creators, and anyone with a significant digital presence are also at risk.
This is where Qondar, Enthec’s solution designed for individuals, comes into play.
The importance of CTEM at a personal level
Personal data leaks, identity theft, doxing, or misuse of private information are increasingly common risks. Qondar allows you to apply the CTEM approach to the personal sphere through:
- Monitoring of exposed personal data.
- Detection of compromised credentials.
- Monitoring mentions in open and non-conventional sources.
- Early warnings to act before the damage is greater.
In this way, the Continuous Management of Threat Exposure ceases to be a corporate concept and becomes a practical tool for everyday life.
Real advantages of the CTEM approach compared to other models
Adopting CTEM involves a change in mindset that offers clear benefits:
- Fewer surprises: incidents are detected earlier.
- Better use of resources: action is taken on real risks.
- Greater visibility of the digital exhibition.
- Progressive risk reduction, not just one-off patches.
Furthermore, CTEM is better suited to changing environments, where digital assets appear and disappear rapidly.
CTEM and the future of cybersecurity
Everything points to cybersecurity continuing to move away from static models. CTEM is one of the key approaches for the coming years, precisely because of its continuous and adaptive nature.
Organizations that adopt this approach will be better prepared for an environment where threats never rest, and digital exposure is constantly increasing.
Enthec and its commitment to Continuous Threat Exposure Management
Enthec has understood this market evolution and translated it into practical solutions. Both Kartos for companies and Qondar for individuals are designed with a clear CTEM logic, focusing on cyber surveillance, anticipation, and real risk reduction.
It’s not just about reacting to incidents, but about constantly monitoring, understanding, and acting.
Does it make sense to apply CTEM in your case?
If you manage a business, a digital project, or your own online presence, the answer is usually yes. The question isn’t whether there is exposure, but rather how much exposure you have right now and whether you are aware of it.
If you want to start applying the CTEM approach in practice, you can learn more about Kartos or Qondar and discover how continuous cyber surveillance can help you reduce risks before they become real problems.
Cybersecurity no longer allows for a reactive approach; we must be vigilant at all times. And in that regard, CTEM has become one of the best possible solutions.


