
Third-Party
Managing third party risk is critical to protect the organization and grow the business
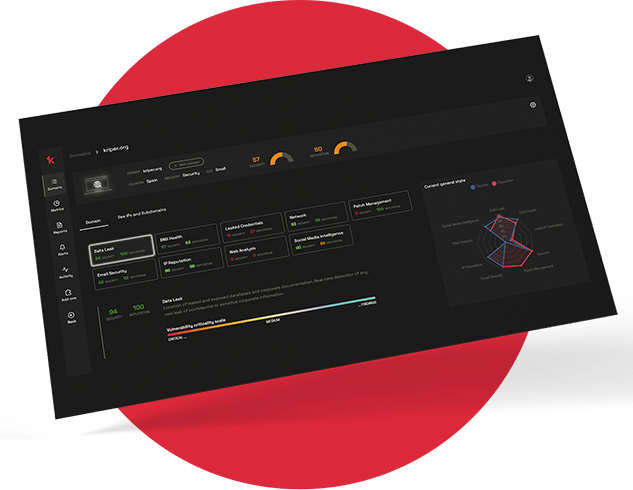

Kartos Third-Party

Accurate risk assessment of potential third parties and evaluation of the maturity of your cybersecurity strategy.Effective risk management of third parties and peers throughout the contractual relationship and continuous assessment of your cybersecurity strategy.Automated, real-time detection of third-party and nested security breaches and assessment of the degree of risk threat to the organization.Monitoring of risk remediation by the third party.
Use Kartos' non-intrusive system to:
Company
Manage the organization’s third-party risk on an ongoing and automated basis.
Business Relationships
Assess the risk of third parties prior to the formalization of the commercial relationship.

Corporate Threat Watchbots
Kartos is the Continuous Threat Exposure Management (CTEM) platform, which allows you to monitor your value chain risk in a non-intrusive, automated, continuous and real-time manner.
Ongoing third party risk management
Ongoing third party risk management throughout the duration of the business relationship.
- Updated and objective data from third parties obtained in real time.
- Alarm reception for a threat associated with a third party in real time.
- Different licenses for the different levels of criticality in the value chain.
- Risk monitoring of critical nth parties.
- Guide for the efficiency of other assessment methods: audits, offensive security tests.
- Evidence of an effective third-party risk management for hiring with administrations and critical entities included in NIS 2 and other international regulations.
Assessment prior to commercial relationship
Third-party risk assessment prior to the formalization of the business relationship
- Information with objective data obtained in real time.
- Continuous risk monitoring of the potential third party during the evaluation period.
- Continuous monitoring of the risk of potential critical nth parties during the evaluation period.
- Complement to other assessment methods: pentesting and due diligence.

Corporate Threat Watchbots
Kartos provides objective real-time data on ongoing threats related to the value chain, to locate and neutralize them before they affect the organization.

Corporate Threat Watchbots
Vectors monitoredby Kartos Third parties:
- Algorithms
- Certificates
- Services / IoT / VoIP
- DNS Health/Phishing
- Patch Management
- IP Reputation
- Web Security
- Email Security
- Document Leaks
- Credential Leaks
- Social Networks
Putting your company to the testcosts nothing

Kartos Third-Party

Advantages of Kartos Third Parties
- Objective assessment method that does not require human intervention.
- Non-intrusive method that does not require third-party authorization.
- Objective, up-to-date, and precise data on third-party information leaks and exposure, as well as the security breaches causing the leaks.
- Continuous and real-time monitoring and analysis of third-party risk throughout the commercial relationship.
- Control of hidden information.
- Capability to evaluate nth-party risks.
- Reports on the risk level associated with the value chain.
- Easy implementation.
- Automated operation.

Uses of Kartos Third Parties
- Real-time management of value chain risk
- Risk assessment of a potential third party
- Risk assessment of a cyber policy for insurance companies
- Digital risk assessment for a merger or acquisition
- Legal compliance

