Industrial digitization is advancing faster than many imagine. What was once a largely isolated environment (production lines, machines, control systems, etc.) is now connected and therefore exposed.
We’re talking about operational technology, or OT, an area where security can no longer be treated as an optional add-on, but as a critical part of the daily operation of any company.
Some tools stand out, such as Kartos, which provides organizations with a clear, up-to-date, and prioritized view of the cybersecurity risks affecting them. It doesn’t just identify vulnerabilities; it helps assess the company’s actual exposure, where the risk lies, and how to reduce it before it is exploited.
Operational technology: an industrial environment that is no longer isolated
For decades, operational technology networks operated separately from traditional computer systems. This isolation was, in itself, a layer of security. However, the need to improve efficiency, share data, and remotely control processes has led OT systems to be interconnected with IT networks and cloud services.
What does this mean in everyday life?
IT/OT convergence offers clear advantages: continuous monitoring, predictive maintenance, energy savings, and reduced downtime. But it introduces a new scenario:
-
- More entry points for external threats.
- Industrial equipment that was not designed with cybersecurity in mind.
- Complicated updates that are delayed for fear of halting production.
- Dependence on external providers whose own vulnerabilities can affect the company.
In this scenario, relying on traditional controls or one-off reviews is no longer enough. The exposure changes weekly, sometimes daily.
You might be interested in> IoT and cybersecurity: Risks and strategies to protect connected devices.
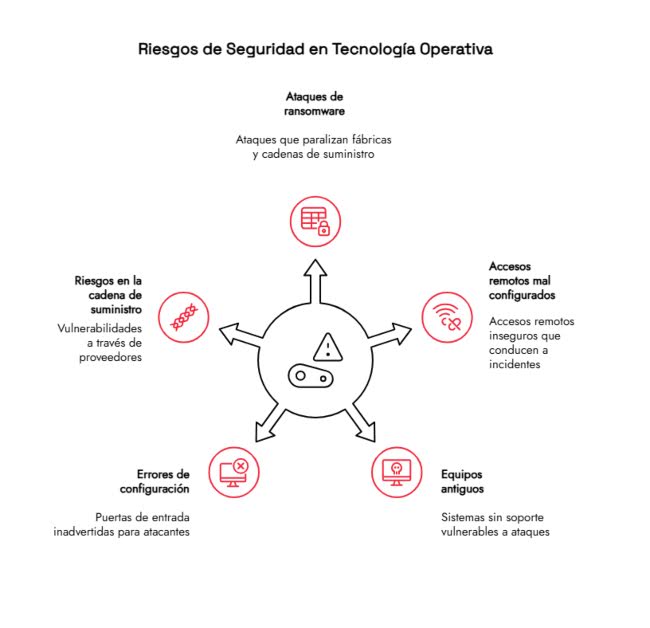
Main risks affecting operational technology OT today
Operational technology (OT) faces very different risks than those typically found in office computer systems. Here are some of the most common:
1. Ransomware in industrial environments
Ransomware attacks are no longer solely focused on stealing or encrypting data. They also aim to paralyze entire factories, disrupt supply chains, or compromise critical equipment.
2. Misconfigured remote access
Remote access is proper, yes, but it’s often enabled hastily, with weak passwords, or without adequate controls. This is one of the vectors that causes the most incidents in OT environments.
3. Older equipment without support
Many industrial machines are decades old. They’re still working, but they no longer receive security patches. When connected to the network, they become easy targets.
4. Configuration errors
Even a small, unmonitored open port can serve as a gateway for attackers.
5. Risks in the supply chain
Suppliers are also part of the OT ecosystem. A security breach in their network can ultimately affect the company as a whole.
All these factors make it clear that a specific protection strategy is needed for operational technology.
Why proactive cybersecurity is essential in OT
The philosophy of proactive cybersecurity is based on anticipating risks.. It is not enough to react when something goes wrong; we must identify threats before they create a real problem.
1. Operational technology cannot stop
In IT, a failure can lead to data loss or work interruptions. Serious, of course, but manageable. In OT, a failure can halt a production line, generate millions in losses, endanger workers, or affect critical services.
That’s why OT security should aim to prevent incidents from their origin.
2. Threats are constantly evolving
The attackers already know the weaknesses in the operational technology. They are looking for old faults, careless configurations, or forgotten access.
. An annual review or a static analysis is not enough to keep up with them.
3. The exposure changes, although the infrastructure does not.
Even if the company does not install new machines, its exposure may vary due to:
- New connections.
- Changes in suppliers.
- Software updates.
- Human errors.
- Newly discovered vulnerabilities.
Supervision must be continuous.
What does a CTEM approach bring to operational technology environments?
The Continuous Threat Exposure Management (CTEM) is a framework that has gained traction in recent years. It enables organizations to, on an ongoing basis, understand the risks they face, their potential impact, and the actions to prioritize.
How CTEM is applied to OT operational technology
A well-implemented CTEM strategy in OT helps to:
- Identify exposed assets, including those the company may have forgotten.
- Detect insecure configurations.
- Control how the attack surface changes.
- Prioritize risks based on actual impact, not assumptions.
- Guiding teams towards faster and more informed decisions.
This is where solutions like Kartos stand out for their comprehensive approach and their ability to continuously monitor exposure without interrupting industrial operations.
Kartos: a realistic and helpful solution for protecting operational technology
Unlike other tools that focus on vulnerability detection, Kartos helps visualize the actual exposure of each asset, supplier, and process connected to the network.
Advantages of using Kartos in an OT environment
- Provides a clear, prioritized view of the attack surface.
- Identifies risks in external providers.
- Facilitates quick decision-making.
- Reduces the likelihood of incidents that affect production.
- Provides context: it not only shows vulnerabilities, but also their potential impact.
For companies with complex OT environments, this is critical. Knowing what might fail before it does is a matter of money and safety.
Proactive cybersecurity best practices in operational technology
To strengthen an OT environment, these measures are especially recommended:
1. Complete and up-to-date inventory
You can’t protect what you don’t know. A living inventory, not a static document, is essential.
2. Network Segmentation
Properly separating IT and OT environments limits lateral movement in the event of an intrusion.
3. Continuous monitoring
OT systems require constant monitoring to detect unexpected changes.
4. Strict access control
You have accounts with minimal privileges and remote access protected by multiple factors.
5. Constant review of the supply chain
Every vendor is a potential point of attack. The good news is that many of these measures can be automated or better managed with CTEM tools like Kartos.
Anticipating is the only viable strategy
Digital transformation is already a reality in the industrial sector. Operational technology is more connected than ever, and that brings enormous benefits… but also obvious risks. In this environment, reactive cybersecurity falls short. Companies need approaches that are up to today’s challenges: continuous, intelligent, and aligned with real impact.
Solutions like Kartos help organizations understand and manage their exposure without slowing operations. That’s the key: protect without stopping, anticipate without alarm, monitor without interrupting.
If your company works with operational technology and wants to understand its actual exposure to threats, start today with continuous, proactive analysis.. Discover how Kartos can help you protect your industrial environment before risks become problems.


