Find out why Gartner® Recognises Enthec® as a Manufacturer of:
Find out why Gartner® Recognises Enthec® as a Manufacturer of:

Corporate Threat Watchbots
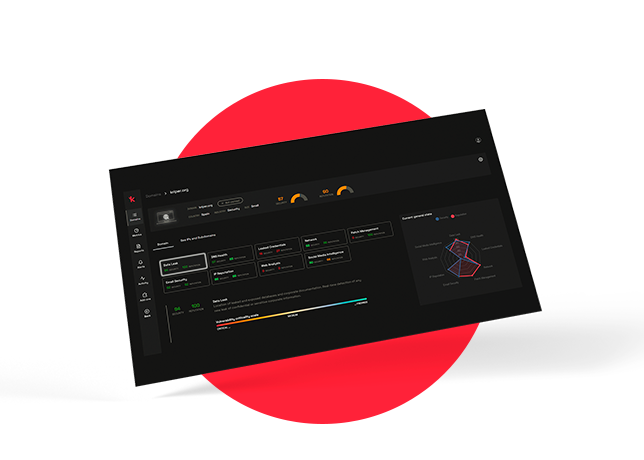
Kartos is an automated monitoring tool, independent of third-party applications, non-intrusive and continuous, that provides data and alerts on open and exposed vulnerabilities in real time by simply entering the domain of the company to be monitored.
False positives are now history
Kartos’ unique AI-based contextual tags to completely eliminate false positives in search results.
- Ciber-intelligence: Locate your organization's open and exposed information and vulnerabilities on the Internet, the Deep Web, the Dark Web and Social Networks.
- Cybersecurity: Extends cybersecurity strategy beyond the corporate IT perimeter.
- Scoring: Corporate cybersecurity score based on objective data taken in real time.
- Compliance: Corporate compliance based on objective data in real time.
- More phishing and ransomware protectionDetection of phishing, fraud and scam campaigns on social networks
- Do you need Brand Protection?Detection of trademark counterfeiting and fraudulent use of intellectual and industrial property.
- Have your credentials been leaked?
- Do you comply with the regulations?
- Third Party Risk
- External Attack Surface (EASM)

Detection of phishing, fraud and scam campaigns on social networks
- DNS Health: Squatting, Social Networking, domains and subdomains.
- AI analysis of the phishing, fraud and scam campaign and all its infrastructures in different countries.
- Transfer of IPs, domains and URLs information necessary to deactivate the campaign.
- Control and monitoring of the entire campaign and all its infrastructures.
- Takedown service

Detection of trademark counterfeiting and fraudulent use of intellectual and industrial property.
- Social Media Intelligence: Telegram, Facebook, X, LinkedIn, Instagram, Youtube and Spotify.
- Tracking of social networks for accounts containing cloned or similar corporate identity elements.
- Analysis of the detected profiles.
- Issuance of real-time alerts.
- Continuous monitoring until deactivation.
- Takedown service.

Credential Leak
- Locating leaked and exposed corporate credentials.
- Location of compromised corporate email accounts.
- Detection of security breaches causing the breach.


Regulatory compliance
- Data protection.
- Certifications and standards: ENS, ISO 27001, PCI…
- Assessment of compliance with all external and certain internal attack surface controls.
- Assistance in the implementation or renewal phase of certifications.
- Compliance testing based on objective data taken in real time for third parties and legal claims.

Third party risk and value chain control
- Real-time monitoring of value chain risk.
- Non-intrusive, no third party permission needed.
- Objective data obtained in real time.
- Complement to traditional valuation tests such as pentesting or due diligence for mergers or acquisitions.
- Third party cybersecurity scoring,
- Third party compliance.


External Attack Surface Management (EASM)
- Threat Hunting
- Net
- CVEs
- Locating filtered and exposed databases
- Locating leaked and exposed corporate information
- Patch management
- IP Reputation
- Web security
Protecting your digital identity and your online assets is protecting your personal integrity and your offline wealth.
Qondar is the platform that provides individuals with real-time information about their identity and digital assets and the ongoing activities related to them, so they can monitor their online security.
- 100% automated operation without human intervention in any part of the process.
- Research is conducted on the Internet, the Deep Web and the Dark Web and only on the person who has issued the protection authorisation, so its operation and the information obtained strictly comply with the limits imposed by law.
- The only platform that analyses conversations on social networks (Telegram, X, LinkedIn, Facebook, Instagram, TikTok) from the perspective of detecting threats to individuals.
- Elimination of false positives, which avoids confusion between people with identical names.
- Continuous operation that allows real-time detection of leaks of sensitive personal information and suspicious online activities that may pose a threat to the personal or financial integrity of the protected person.
- Maximum ease of use. You only need to enter the name and personal assets to be monitored and Qondar starts working autonomously.

Personal Threat Watchbots
Qondar is software that helps people keep track of their personal information, making them aware of any leaks on the web, and providing them with data and alerts about open vulnerabilities before they can be discovered by cybercriminals.
- Protection of personal assetsTake care of your money and digital assets.
- Comprehensive protection of your communicationsDefend your digital privacy.
- Do you care about your personal reputation?Your digital image always intact.
- Defending against online threatsProtection against risks on the Internet
- Protection against identity theftPrevent digital identity theft
- Security for your Social NetworksProtect your social media accounts

Take care of your money and digital assets
Qondar secures your bank accounts, payment cards and cryptowallets, protecting your assets against cyber threats.


Defend your digital privacy
Protect your emails and social networks against cyber attacks and unauthorised access.

Your digital image always intact.
Prevent attacks that could damage your personal and professional reputation in the digital environment.

Protection against risks on the Internet
Qondar acts as a shield against malicious activities that may compromise your personal or financial integrity.


Prevent digital identity theft
Qondar prevents criminals from impersonating you online, protecting your digital identity.

Protect your social media accounts
Maintain the integrity of your LinkedIn, Facebook, X, Instagram, TikTok and Telegram profiles against hacking and manipulation.

What makes us different?


1. Trust
- Data quality: Exclusive in-house developed technology that eliminates false positives.
- Availability: Real-time information available 24x7
- Security / Confidentiality: No back doors. Development and maintenance are internal. The information obtained is not transferred to third parties at any time during the process.

2. Efficiency
- Five services on a single TEM platform (Threat Exposure Management):
- EASM: Management of the external attack surface
- DRP: Digital risk protection
- Brand Protection
- Third Party Risk
- VIPS and C-Levels Protection
- 100% automated platform
- Real-time information
- Cybersecurity teams focused on major tasks (Saving technological and human resources)

3. Flexibility
- Customised products: Solutions adapted to different scenarios and customers within your companies.
- Multitenant / Channel-oriented: Efficient management of multiple users or entities from a single platform.
- Adaptable configuration: Each implementation is tailored to the customer's specifications and requirements, offering a possible flexible solution for each case.

Threat Watchbots
Corporate & Personal cyber-surveillance
Testing your companydoesn't cost anything
1,509.033
LEAKS FOUND IN 30 DAYS
100M
OF LINKS REVIEWED DAILY
2.500
DEEP WEB
Resources

Individual Cybersecurity for Relevant Individuals
In the digital environment, protecting information has become a critical priority for organisations. Corporate cybersecurity strategies are designed to secure the organisation’s data and systems and prevent security breaches that could lead to an attack that could put them at risk.
Artificial Intelligence: The challenge for people's security
The emergence of artificial intelligence has revolutionised multiple sectors, offering significant benefits that no one doubts. However, as with every new technology, its development has also given rise to new threats and vulnerabilities.
Enthec® Blog
Risks of AI in people’s online safety
11 February 2026
AI in cognitive warfare: how are cyberattacks evolving?
6 February 2026
Our Partners

Our network of sales, consulting and service partners is made up of top-tier cybersecurity companies to provide the right response to each customer's needs. Our partners are a fundamental part of the success of our cybersecurity solutions and are spread across all the countries in which we operate to ensure close attention to our customers.
Certifications

ENS HIGH level

The National Security Scheme (ENS), originally designed for the area of e-Government in Spain, has been extended to include service providers that collaborate with public entities. This scheme defines security policies in the use of electronic media, establishing basic principles and minimum requirements to guarantee adequate protection of information.

ISO 27001

ISO 27001 is a globally recognized information security standard, which has been developed and is maintained by the International Organization for Standardization (ISO) and focuses on providing the specification for an information security management system or ISMS.