SIM Swapping: what it is, how it works and how to avoid this scam in 2026
Our mobile phone is more than just a device: it's the center of our digital lives. We use it to access our social media, online banking, medical services, and work communications.
But have you ever thought about what would happen if someone hijacked your phone number? This is precisely what happens with SIM swapping, an impersonation technique that is on the rise.
Before going into details, it's worth presenting a solution that can be very useful for detecting an attack in time. Qondar, our tool, is a platform for individual cyber-surveillance to anticipate digital threats.
Qondar is an early warning system that identifies potential exposure of your personal information online and can help you detect signs of SIM swapping before it's too late.
What is SIM swapping?
You may have read about it in recent news or heard it called SIM swap or SIM swapping, but what exactly is SIM swapping?It is a digital scam that involves duplicating your SIM card without your consent.
In other words, a cybercriminal can take over your phone line, redirecting your calls, messages, and, most worryingly, the verification codes that many services send via SMS.
The objective is clear: access your accounts using popular two-step verification (2FA) systems. Many banks, social media platforms, and email services use this method to verify your identity, but if the attacker already has your phone number, they can receive these codes and access your data as if they were you.
SIM swap: how does it work?
The technique is not new, but it has gained popularity in recent years. The modus operandi usually follows this scheme:
- Obtaining personal data. Through leaks, social engineering, or even social networks, the criminal collects enough information about you (name, ID, address, phone number, etc.).
- Impersonation. With this information, they contact your phone provider, posing as you, and request a duplicate SIM card, claiming the device has been lost or damaged.
- Activating the new SIM. Once the operator validates the request, the new SIM is activated, and your line will no longer be available on your device.
- Account access: The attacker tries to access your accounts. If you have SMS authentication enabled, he is already on the hook.
In minutes, someone can gain complete control over your personal data, networks, online banking, and more.

How can you tell if someone has swapped your SIM card?
Detecting an attack in time can mean avoiding serious losses or blocking access before it causes damage. Here are the clearest warning signs:
- Your mobile phone suddenly loses coverage in an area where you normally have a signal. You're not receiving calls or messages, but there's no apparent technical cause.
- You receive notifications of changes to your account (changed passwords, login attempts) in services you haven't touched.
- There are unrecognized bank transactions or transfer attempts on your account.
- You receive an SMS or call from your operator confirming a SIM change that you did not request.
- You cannot access your email, social media, or online banking with your usual credentials.
If you experience any of these signs, act immediately. Call your operator to block the duplicate, contact your bank, and change the passwords for your main accounts from a secure device.
A tool like Qondar, our individual cyber-surveillance solution, can alert you to signs prior to an attack, such as the appearance of your data in security breaches or on dark web forums, allowing you to react before the SIM swap materializes.
How to protect yourself from SIM swapping?
It is normal to wonder how to avoid SIM swapping or what we can do to protect ourselves from this dangerous technique. Here are some recommended measures:
1. Minimize the information exposed on networks
Avoid sharing information such as your phone number, date of birth, or address on social media. Even seemingly harmless information can be used to create a fake profile and impersonate you.
2. Change authentication methods
Whenever possible, avoid SMS authentication. Opt for authentication apps like Google Authenticator, Authy, or physical keys (like YubiKey), independent of your mobile phone line.
3. Activate notifications on your operator
Some carriers allow you to notify them of any line changes, such as SIM card duplication or portability requests. Activate these notifications if available.
4. Use unique passwords and a password manager.
If an attacker can't guess or recover your password, it will be much harder for them to access your accounts, even with just your phone number. Use long, unique passwords for each service, and manage them with a secure password manager.
5. Continuously monitor your digital exposure with Qondar
Qondar, Enthec's solution for individual users, continuously monitors whether your personal data has appeared in security breaches, on the dark web, in cybercriminal forums, or in any space where it could be used to prepare a SIM-swapping attack.
Thanks to its CTEM (Continuous Threat Exposure Management)- based model, Qondar does not perform a one-off analysis of your situation; it continuously evaluates your digital risk and sends you personalized alerts when it detects signs of danger.
SIM swapping: How to prevent it with an early warning tool
Attacks don't always come in visible form. Often, personal data leaks online before a SIM swap. Emails, passwords, phone numbers, or addresses leaked in stolen databases are the cybercriminal's first step.
Qondar lets you know if your data has appeared in a security breach, if someone is trying to steal your identity, or if your phone number has been compromised. This information is vital so you can take timely measures, such as changing your password, contacting your carrier, or even temporarily blocking certain services.
Thanks to its model-based approach, CTEM (Continuous Threat Exposure Management), Qondar doesn't just analyze a snapshot of your digital situation; it continuously assesses your risks and adapts to the changing cybersecurity environment.
Why is SIM swapping an increasing threat in 2026?
SIM swapping is not an isolated problem. According to data from Europol and the National Cryptologic Center, these types of scams are rising in Europe. Attackers are targeting prominent public figures as well as ordinary citizens whose data has been exposed online.
SIM swapping is neither an isolated nor a new problem, but its reach has continued to grow. Several factors explain this increase:
- Greater digitization of critical services: Banking, insurance, healthcare, and public administration use the telephone as a verification tool, increasing the value of the phone number for attackers.
- Proliferation of data leaks. Every security breach that exposes millions of records provides criminals with the material they need to prepare social engineering attacks.
- Increasingly sophisticated techniques. Attackers use AI to generate convincing conversations with operators, mimic voices, or create fake documentation.
- Low barriers to entry. There are kits and tutorials on the dark web that make it easier for actors with little technical experience to carry out this attack.
The consequences of being a victim of a SIM swapping scam can include unauthorized bank transfers, identity theft to commit crimes, blocking of personal and professional accounts, loss of access to medical services or insurance in your name, and irreversible loss of digital assets such as cryptocurrencies.
Therefore, having tools that perform this monitoring automatically and constantly has become a real necessity.
What to do if you have already been a victim of SIM swapping?
If you believe you have suffered a SIM swap attack, act quickly by following these steps:
- Call your operator immediately. Report what happened and request that they block the fraudulent duplicate and restore control of your line.
- Contact your bank. Report the situation so they can block potential transfers and review your recent account activity.
- Change passwords from a secure device. Prioritize email, online banking, and social media. Use a trusted Wi-Fi network, never a public one.
- File a complaint. Contact the State security forces (National Police or Civil Guard) and INCIBE (017, the cybersecurity helpline).
- Review and strengthen your digital security. Remove SMS 2FA from all possible services and activate more secure authentication methods.
What can you do today?
Now that you know what SIM swap is and how easy it is to fall victim to this scam, you can make more informed decisions to protect yourself.
We recommend:
- Review your authentication methods in the most important digital services.
- Avoid using the phone number as the only verification method.
- Try Qondar, our cyber surveillance platform for individuals, which helps you keep your data safe with personalized alerts.
SIM swapping is a real, silent, and dangerous threat. You don't have to be a celebrity to be targeted: all it takes is for your data to have been leaked, even if it's on a website you registered with years ago.
Protecting yourself requires a combination of prevention, good digital practices, and tools that work for you.
Qondar by Enthec is precisely that: a digital shield that alerts you when something is wrong, when your data appears where it shouldn't. Thanks to its continuous monitoring capacity and threat exposure management, it becomes a key ally in preventing SIM swapping before it happens.
Want to check if your information has already been exposed?
Get access to Qondar and take the first step to protecting your digital identity. Visit Enthec and protect your data before it's too late.
The Relevance of Artificial Intelligence in Cybersecurity
Artificial intelligence (AI) has become a key player for many people in different personal and professional areas, but we must also know its ability to protect us against digital threats.
From businesses to individuals, we are all exposed to constantly evolving cyberattacks, where the combination of cybersecurity and artificial intelligence plays a decisive role. AI applied to cybersecurity improves the ability to detect and prevent threats, allowing a more efficient and faster response to possible attacks.
In this article, we will discover why artificial intelligence and cybersecurity are so closely linked, the applications of this technology, and its positive impact on our daily lives.
What is artificial intelligence in cybersecurity and why is it essential in 2026?
Artificial intelligence in cybersecurity is the set of technologies, algorithms, and machine learning systems specifically designed to identify, prevent, and neutralize digital threats autonomously and in real time. Unlike traditional tools, AI is not limited to recognizing known patterns, but continuously learns from new attack vectors.
The current cyber threat landscape has changed drastically:
- The deepfake attacks. Identity theft has increased by 850% since 2024, with generative AI creating fake audio and video recordings of executives authorizing fraudulent transfers.
- Adaptive ransomware uses machine learning to identify each organization's most valuable data before encrypting it, maximizing the pressure to pay ransoms.
- Polymorphic attacks change their code in real time, evading traditional detection systems that rely on static signatures.
According to the Global Cybersecurity Report 2026, 87% of security leaders identified AI-related vulnerabilities as the fastest-growing cybersecurity risk by 2025, surpassing even ransomware and supply chain attacks.
Why is artificial intelligence critical in cybersecurity?
The digital threat landscape has reached unprecedented complexity. Cybercriminals now employ the same AI technologies that organizations use to defend themselves, creating a digital battleground where only the most advanced systems survive.
Artificial intelligence for cybersecurity stands out because it can:
- Analyze large volumes of datain record time. AI for cybersecurity processes massive volumes of information that no human team could analyze, such as analyzing millions of security events per second, reducing the average detection time, and correlating information from multiple sources.
- Detecting suspicious patterns that might go unnoticed by humans through the analysis of anomalous behavior.
- Learn and adapt constantlyto improve its effectiveness. The human factor remains the weakest link in cybersecurity. According to IBM Security, 95% of security breaches in 2025 involved some type of human error.
The key lies in its ability to act proactively and automatically, making defense barriers more dynamic in the face of constantly changing threats.

Applications of AI for cybersecurity
Artificial intelligence applied to cybersecurity has a range of applications, ranging from threat detection to response automation. Here are some of the highlights:
Real-time threat detection
Advanced algorithms enable AI to analyze data traffic and detect anomalous behavior in real time. For example, it can identify an attempted intrusion into a network before it causes damage. This significantly reduces reaction times and mitigates potential risks.
Attack prevention
AI can anticipate attackers' movements by studying previous patterns. From here, it is possible to create more robust systems designed to prevent attacks before they occur. For example, some AI models can identify phishing emails even if they use advanced spoofing techniques.
Phishing attacks have evolved dramatically. Modern systems no longer rely solely on blacklists of malicious domains; instead, they employ natural language processing (NLP) and multimedia content analysis.
Response Automation
When an attack is detected, AI can automatically make decisions, such as blocking unauthorized access or neutralizing malware. By acting immediately, AI saves time and minimizes potential damage.
Information protection
AI is also crucial for protecting sensitive business and user data. You can detect data extraction attempts or unauthorized access by analyzing access patterns and blocking them in real-time.
Predictive and shared threat intelligence
Modern cybersecurity and artificial intelligence platforms integrate threat information from multiple global sources:
- Dark web analysis to identify discussions about vulnerabilities or leaked data from your organization.
- Correlation of attack campaigns across industries to anticipate which sectors will be targeted next.
- Early identification of compromised corporate credentials in third-party breaches before they are used in credential attacks.

Benefits of artificial intelligence in cybersecurity
Combining cybersecurity and artificial intelligence offers numerous benefits that enhance protection and optimize resource use. Here are some of the most important ones:
Early Threat Detection
One of the biggest challenges in cybersecurity is identifying threats before they cause damage. AI can analyze large amounts of data in seconds, making it possible to detect anomalies that might go undetected with traditional methods.
Prevention of human error
Human error is one of the leading causes of cyberattacks. Weak passwords, clicks on suspicious links, and incorrect configurations are gateways for attackers. AI helps minimize these risks by automating tasks and alerting users to unsafe behaviors.
Although we mustn't forget the risks of AI.
Adaptability
As attackers develop new techniques, AI systems can adapt quickly, learning from each attack attempt to strengthen defenses. This ensures that protective measures are always one step ahead.
The future of artificial intelligence applied to cybersecurity
The role of artificial intelligence in cybersecurity will only grow in the coming years. With the rise of the Internet of Things (IoT), the number of connected devices will increase, expanding the attack surface. AI will be instrumental in managing this complexity and developing more innovative, personalized solutions.
In addition, collaboration between humans and machines will be essential. Although AI is powerful, it does not replace human judgment. Instead, it amplifies our capabilities, allowing cybersecurity experts to focus on more strategic tasks.
Enthec: your expert partner in cyber-surveillance
At Enthec, we know that companies and individuals face unique challenges in cybersecurity. That's why we've developed specialized solutions through our platforms: Kartos, designed to protect businesses, and Qondar, focused on individual security. Both use artificial intelligence, which is applied to cybersecurity through threat watchbots.
Kartos, a cyber-surveillance platform for companies, helps your organization detect publicly leaked information in real-time, thus locating open and exposed security breaches.
On the other hand, Qondar focuses on protecting individuals from digital threats that can compromise their personal information, privacy, and peace of mind. It continuously and automatically monitors people's sensitive information and digital assets to protect individual privacy and prevent criminal or harmful use.
In a world where threats constantly evolve, intelligent tools like Kartos and Qondar are not a luxury but a necessity. Whether you're looking to protect your organization's data or your personal information, Enthec is here to help keep you safe.
The combination of artificial intelligence and cybersecurity is the key to facing the challenges of the digital world. With Enthec, you're one step away from the cybersecurity of the future.
What are you waiting for to leap with Kartos and Qondar? Together, we can protect your business and yourself. Contact us!
IAM in cybersecurity: the fundamental pillar for protecting access in your organization
Access to systems, applications, and data continue to grow each year, making it a strategic priority to control who can enter, when, and with what permissions. The concept of IAM in cybersecurity is not just about passwords or logins, but a complete discipline that manages digital identities and permissions to reduce risks and maintain control.
Many companies invest in firewalls, antivirus software, and network monitoring, but they often forget that the main entry point is often through legitimate user access. A credential leak can open more doors than any technical exploit.
Therefore, understanding what IAM is in cybersecurity and how to apply it effectively is key for any organization that wants to protect its digital assets.
What is IAM in cybersecurity, and why does it matter?
When we talk about IAM in cybersecurity, we are referring to Identity and Access Management systems, that is, tools and processes that manage digital identities and control access to technological resources.
In simple terms, IAM defines who can access what and under what conditions. . But behind that definition lies a whole ecosystem of policies, authentication, roles, and audits.
Essential elements of an IAM system
A well-implemented IAM system typically includes:
- Authentication: identity verification (password, biometrics, MFA).
- Authorization: assignment of permissions according to roles.
- Identity management: user registrations, cancellations, and changes.
- Audit and traceability: access and action log.
These components work together to reduce human error, limit unnecessary privileges, and detect suspicious behavior.

The real problem: uncontrolled access and digital exposure
Many organizations believe they are in control because they use strong passwords or multi-factor authentication. . However, the risk usually lies elsewhere: exposure of assets on the internet.
Forgotten servers, old active accounts, misconfigured repositories… All of these form part of the attack surface. And without continuous monitoring, IAM alone is not enough.
This is where a more advanced approach comes into play: the Continuous Threat Exposure Management (CTEM).. This model not only manages identities but also continuously monitors which externally visible elements attackers can exploit.
IAM and CTEM: a necessary combination
Integrating cybersecurity IAM with CTEM strategies allows to move from a reactive to a preventative approach. It's not enough to protect access points; we need to know what could be attacked before anyone even tries.
Why combine both approaches
- IAM controls who enters.
- CTEM analyzes which doors are visible.
- Together, they allow for prioritizing real risks.
An IAM system without external visibility is like having new locks on a house with open windows. That's why more and more companies are seeking solutions that combine identity management with continuous monitoring of digital exposure.
How does IAM affect business security?
The impact of cybersecurity IAM extends beyond the IT department. It directly influences business continuity, reputation, and regulatory compliance.
Tangible benefits for the organization
A robust identity management model involves reducing unnecessary access,thereby reducing the likelihood of intrusion. It also strengthens the organization's internal controls, improves the user experience through centralized access, and simplifies regulatory compliance.
In addition, it is possible to detect anomalous patterns, such as a user logging in from two different countries within a few minutes.
The role of cyber surveillance in protecting access
The evolution of threats has changed the rules. Today, attacks don't always seek to directly compromise systems; they often first scan for existing assets and identify potential weak points.
That's where Enthec's proposal comes in,focused on cyber-surveillance solutions geared towards CTEM. Their solutions continuously analyze the exposed digital surface and detect risks before they escalate into incidents.
Kartos: business approach
Within this approach, Kartos stands out, designed for companies that need continuous visibility of their digital exposure.. The solution identifies exposed assets, credential leaks, and potential identity-related attack vectors.
This aligns directly with the cybersecurity IAM strategy: if you know which credentials or access points are compromised, you can take action before they are used.
Signs that your organization needs to improve its IAM
Many companies don't detect flaws in their identity management until an incident occurs. Some warning signs include:
- Users with permissions they don't need.
- Active accounts of employees who no longer work.
- Access without an audit log.
- Credential sharing.
- Lack of periodic review of privileges.
If any of these points appear in a cybersecurity audit, the IAM system will likely need adjustments.
Best practices to strengthen your IAM strategy
Effectively implementing cybersecurity IAM depends not only on the tool used, but also on how it is configured and managed.
. These practices help improve results:
Least privilege policies
Each user should only have the access necessary for their work. Nothing more. This reduces the impact if an account is compromised.
Periodic review of access
Permits should be reviewed regularly, especially after changes in position or employee departures.
Multi-Factor Authentication
It's not a magic solution, but it adds an extra layer of protection against credential theft.
Continuous monitoring
This is where cyber surveillance becomes valuable. Knowing what's happening outside your network can be just as important as monitoring what's happening inside.
IAM as part of a mature security strategy
A mature cybersecurity organization does not simply install tools; it builds a coherent ecosystem.. IAM must be integrated with monitoring, risk analysis, and external visibility.
The current trend points toward unified models in which digital identity becomes the central focus of protection. This is no coincidence: identity is the new perimeter.
Therefore, when someone asks what IAM is in cybersecurity, the most accurate answer would be: the system that decides who can act within your digital infrastructure and under what conditions.
Companies that anticipate these trends will have an advantage against increasingly sophisticated threats.
Cybersecurity IAM has become an essential foundation for any digital protection strategy.. No matter the size of the company, if there are systems, data, or users, there is risk.
The difference lies in anticipation. Combining identity management with continuous exposure monitoring enables you to detect weaknesses before they are exploited.
If you want to know your actual level of exposure and how to strengthen your access control, now is the time to review it with Enthec. Analyzing your digital surface today can prevent an incident tomorrow.
Information Security: 5 Best Practices to Implement in Your Company
In 2026, Data protection has become a critical priority in the business environment. Good information security practices are essential for companies to protect their digital assets against cyber threats that are evolving at an unprecedented rate, driven by AI and increasingly sophisticated techniques.
In this article, you will discover what good practices in information security are, why they are essential in your organization, and how to implement 5 essential measures that will strengthen your data protection strategy.
What is information security?
Information security protects information and information systems against unauthorized access, use, disclosure, interruption, modification, or destruction. It has become a critical obligation for organizations.
Companies of all sizes and sectors handle a wealth of information, from personal and sensitive employee and customer data to financial and intellectual property information. This information is a valuable asset that, if compromised, can cause serious harm to data subjects and significant damage to an organization's reputation and financial viability.
Therefore, organizations must establish procedures to ensure information security, protect against threats that may affect it, and ensure the continuity of their operations.
Procedures to Ensure Information Security
These procedures should include information security policies, access controls, information security training, security incident management, and disaster recovery and business continuity plans.
- Information security policies provide a framework for managing information security in an organization. These policies define employee responsibilities, security requirements for information systems, and procedures for handling security incidents.
- Access controls are measures that limit information access to authorized persons. These can include passwords, key cards, and two-factor authentication.
- Information security training is essential to ensure that all employees understand information security and their responsibilities regarding it. This training should cover topics such as the secure handling of information, identifying security threats, and responding to security incidents.
- Security incident management involves identifying, tracking, and resolving security incidents. These incidents typically include phishing attacks, data breaches, and different types of malware.
Disaster recovery and business continuity plans detail how an organization will respond to a security incident that results in a significant loss of information or operational capacity and nullify or minimize its effects.

Key Terms in Information Security
Three key terms allow us to understand the concept and constitute the characteristics of information security: confidentiality, integrity, and availability.
Confidentiality
It refers to the protection of information from disclosure to unauthorized parties. Confidentiality measures include data encryption, access control, and user authentication.
Integrity
In this case, it refers to protecting information against unauthorized modification or deletion. This ensures that the information is accurate and complete. Integrity measures include version control, backups, and intrusion detection systems.
Availability
It refers to ensuring that information and information systems are available for use when needed. Availability measures include system redundancy, disaster recovery, and business continuity planning.
These 3 characteristics of information security should guide organizations in the development of security policies, procedures and controls.
However, information security is not a one-size-fits-all solution that can be applied uniformly across organizations. Each organization must assess its own risks and develop an information security strategy that is tailored to its specific needs.
In addition, information security is not a static state, but an ongoing process. As threats and risks evolve, so do security measures. This requires constant vigilance, regular evaluation of safety policies and procedures, and ongoing user education and training.
5 Best Practices in Information Security
Among the best practices in information security, implementing these five in your company that we detail below is the starting point for any corporate information security procedure.
1. Security Updates
Security updates are critical to
protecting organizations' information systems.
These updates contain patches that address the latest software vulnerabilities. Keeping systems up-to-date minimizes the risk of cyberattacks.
Discover the foremost common types of cyberattacks through our blog.
2. Access to information control
Access control is another crucial practice. It involves ensuring that only authorized individuals have access to sensitive information.
The organization should implement role-based access control policies to limit access to information based on its category and the job responsibilities of its employees.
3. Backups
Regular backups are essential for data recovery in the event of information loss.
The organization should make backups on a regular basis and store them in a safe place. In the event of a cyberattack, backups allow information to be restored and operational activity to be maintained.
4. Password management
Effective password management is vital for information cybersecurity.
It's critical to encourage employees to use strong, unique passwords for each account, as well as to renew them regularly. Additionally, it is advisable to implement two-factor authentication to add an extra layer of security.
You might be interested in-> How to easily and securely manage business passwords and credentials to avoid online threats.

5. Staff Awareness
The human factor remains the weakest link in the security chain. In 2026, social engineering powered by generative AI and highly personalized phishing are highly effective attack techniques that exploit a lack of awareness, creating emails and messages virtually indistinguishable from legitimate communications.
Your employees need to be informed about cybersecurity best practices and how to identify potential threats. Regular training is critical for them to stay up-to-date on the latest threats and how to prevent them.
Enthec helps to protect your company's information.
Kartos is the AI-powered cyber-surveillance platform developed by Enthec that automatically, non-intrusively, and continuously monitors your organization's exposed vulnerabilities in real time. You only need to enter your company's domain for Kartos to start protecting you.
What does Kartos detect that helps strengthen your security practices?
- Credentials compromised. Locates leaked corporate passwords and compromised email accounts on the Internet, Deep Web, and Dark Web before they are used in attacks.
- Phishing and ransomware threats. Detects impersonation, fraud, and scam campaigns on social media, analyzes the entire attack infrastructure using AI, and provides the necessary information to disable them.
- Vulnerabilities (CVEs). Identifies critical vulnerabilities affecting your technology infrastructure in real time, allowing you to prioritize patch management.
- Filtered documents and information. Locates databases and corporate documentation accidentally exposed in public repositories or underground markets.
- Brand protection. Tracks social media (Telegram, X, LinkedIn, Facebook, Instagram, YouTube, TikTok) for accounts that impersonate your corporate identity or fraudulently use your intellectual property.
- Third-party risk. Evaluates the cybersecurity level of your value chain without authorization, based on objective data taken in real time.
- Regulatory compliance. Provides objective proof of compliance for certifications such as ENS, ISO 27001, or PCI, facilitating audits and renewals.
Do you want to implement best practices in information security with a platform that detects threats before they materialize? Find out how Kartos can help you.
Egosurfing and online reputation: how your digital presence affects your image
First impressions no longer happen only in person. Today, they happen on Google, on social media, or in any corner of the internet where your name appears. This is where the term egosurfing comes in, an increasingly common practice for both individuals and companies who want to know what the internet is saying about them.
In this article, we'll look at the meaning of egosurfing, how it works, what tools exist, and why it has become a recommended habit if you care about your online identity.
What is egosurfing, and why should you care?
The term refers to the act of searching your own name on the internet to see what information appears.. That sounds simple, but egosurfing goes far beyond an occasional search out of curiosity.
Actually, it's a method for:
- Detect incorrect or outdated information.
- Discover mentions on websites or forums that you didn't know about.
- Analyze your public digital footprint.
- Identify reputational or security risks.
Today, more than 60% of the world's population has an active internet presence. This means that much of our identity is visible, indexable, and analyzable. Controlling that presence isn't something reserved for celebrities or large corporations, but a useful practice for everyone.
Egosurfing: how it really works
Understanding how egosurfing works requires understanding how search engines work first. Platforms like Google crawl millions of pages and store information in indexes.
When you enter your name, the algorithm displays results it considers relevant based on text matching, page popularity, domain authority, or your recent activity.
That's why two people with the same name may see different results.. Browsing history, location, and other factors influence what appears.

Beyond Google
Although many people associate this practice only with basic searches, egosurfing also includes checking:
- Social networks
- Public databases
- News
- Indexed images
- Filtered documents
Doing it manually can serve as a first step, but it falls short when it comes to constant monitoring.
Egosurfing on Google: the usual first step
Most people start by typing their name into a search engine, performing egosurfing on Google, as a basic step to find out what people are saying about them. This first look can reveal interesting things:
- Forgotten old photographs
- Profiles you thought were deleted
- Forum comments
- Exposed personal data
The problem is that Google only shows a portion of what exists. There are mentions that aren't indexed, or that appear in deeper layers of the internet. Therefore, relying solely on this method can create a false sense of control.
Egosurfing tools: when surveillance becomes professional
There are many free egosurfing tools that automate searches and send alerts when your name appears online. Some allow you to monitor keywords, while others track social media.
They are useful to start with, but they have limitations: they don't always detect leaks, their scope is partial, and they usually depend on publicly indexed data.
Advanced cyber surveillance solutions
This is where more comprehensive technologies come in. Specialized companies like Enthec have developed platforms designed to continuously monitor digital exposure.
Their solutions operate under the CTEM (Continuous Threat Exposure Management) approach, a model that not only monitors results but also analyzes potential risks and detects threats before they become problems.
- Kartos is geared towards organizations and companies that need to control their digital presence and their online assets.
- Qondar is designed for individuals who want to monitor their digital identity, personal data, and potential leaks.
These tools don't replace manual egosurfing, but they greatly enhance it. They let you maintain a realistic, consistent view of what's happening online around your name or brand.
What risks can egosurfing reveal?
Many people believe that if they haven't posted anything controversial, they have nothing to fear. However, your online reputation doesn't depend solely on what you share.
Egosurfing can bring to light situations such as identity theft, exposed personal data in leaks, old comments taken out of context, or photographs published by third parties.
Difference between curiosity and digital strategy
Searching for your name once a month can give you a general idea of your online presence. It's a useful practice for individual users who simply want to know what appears online about them.
Egosurfing as a strategic habit
When it becomes a structured routine, egosurfing becomes a reputation management tool. . At this level, trends, evolution of results, and potential risks are analyzed.
Companies often work this way because they know that online reputation directly influences sales, trust, and credibility.. But more and more freelancers are adopting the same approach. Recruiters, clients, or collaborators search for names online before making decisions.
Maintaining that online presence doesn't mean becoming obsessed, but rather being aware that the internet has a memory.
How to do egosurfing effectively
Simply typing your name and looking at the first page of results isn't enough. To make it truly useful, you should follow certain steps:
-
- Search for variations of your name (with second surname, without accents, with initials).
- Check the images and news tab.
- Analyze results in different browsers or in incognito mode.
- Check social media manually.
- Set up automatic alerts.
This process offers a more comprehensive view. However, it has a clear limitation: time. Doing it manually on an ongoing basis can be tedious, and that's where professional tools add value.
CTEM solutions, such as those from Enthec, enable automated tracking and alerting for any relevant changes. . This reduces the margin for error and makes it easier to take action before a problem escalates.
Warning signs you shouldn't ignore
When egosurfing, it's advisable to pay attention to certain signs, ranging from fake profiles with your name to visible personal data, even finding sensitive information or results associated with crimes or controversies that have nothing to do with you.
If you detect something like this, acting quickly is crucial. The longer it remains posted, the more likely it is to spread.
The future of egosurfing
Everything suggests that this practice will become increasingly common. The reason is simple: our digital lives continue to grow. We publish more, interact more, and leave more traces.
In this context, egosurfing ceases to be a curiosity and becomes a basic digital literacy skill.. Just as we learned to protect our passwords, we now need to learn to manage our online identity.
The ideal combination is usually:
- Periodic manual inspections.
- Use of automated tools.
- Continuous monitoring in sensitive cases.
If you want to take it a step further and have real control over your digital presence, it's worth exploring specialized solutions like Qondar by Enthec.
If you're worried about what the internet might be saying about you without your knowledge, now's a good time to check. Start monitoring your online presence today and make information your best ally.
Risks of AI in people's online safety
The risks of AI are transforming the cybersecurity landscape at an unprecedented pace. While artificial intelligence offers revolutionary advances, it also presents increasingly sophisticated threats that directly affect people's online security.
By 2026, the dangers of artificial intelligence have evolved dramatically, from autonomous agents capable of executing full-scale attacks to hyper-personalized phishing generated in seconds. In this comprehensive guide, we'll analyze the most critical threats and the most effective protection strategies.
At Enthec, we work with a preventive approach, based on early detection and the actual reduction of the attack surface. In this context, solutions like Qondar enable identifying exposed vulnerabilities, forgotten assets, and risks arising from AI use before they are exploited, providing a clear, continuous view of the current security state.
How is the development of AI affecting people's online safety?
The development of artificial intelligence (AI) is revolutionizing online security, transforming both opportunities and challenges in the digital realm. AI's ability to process and analyze large volumes of data, identify patterns, and learn from them brings significant benefits. Still, it is also creating new vulnerabilities and threats that affect people.
One of the most apparent aspects of AI's positive impact on online security is the automation of threat detection. AI-based cybersecurity tools can monitor in real time, detect anomalous behavior, identify fraud attempts, and detect malicious attacks before they cause significant damage.
This has dramatically improved incident response capabilities and reduced the time needed to neutralize threats. For individual users, this translates into better protection of their personal and financial data held by companies.

New AI-Driven Threats
However, cybercriminals also leverage AI to improve their targeted attack tactics, which target a specific person rather than an organization.
The creation of deepfakes, for example, uses AI algorithms to generate fake images, videos, or audio that are almost indistinguishable from the real thing. These deepfakes can be used to spread false information, impersonate people in critical situations, or even commit fraud and extortion. AI's ability to replicate human voices has also led to highly convincing voice scams, in which scammers pose as family members or authority figures to trick their victims.
Another significant risk is the exploitation of vulnerabilities in social networks. AI can analyze profiles and behaviors on these platforms to identify potential targets, collect personal information, and launch targeted attacks. AI-powered bots can also amplify disinformation campaigns and manipulate public opinion, affecting the security of personal data and the integrity of the information we consume.
To mitigate these risks, users must adopt robust security practices. This includes ongoing education about emerging threats and verifying sources before sharing information.
Using advanced security tools that integrate AI capabilities can provide a proactive defense against sophisticated attacks. In addition, being selective about the personal information shared online and adjusting privacy settings on social media can limit exposure to potential threats.
You might be interested in-> The relevance of artificial intelligence in cybersecurity
The 8 most relevant AI dangers in 2026
Among the most relevant risks of Artificial Intelligence, we highlight the following.
-
Autonomous AI Agents
The most sophisticated threat of 2026 is AI agents capable of autonomously executing complete attack cycles:
- Automated recognition of vulnerable systems
- Exploitation of vulnerabilities without human intervention
- Dynamic adaptation to evade detection systems
- Machine-speed operation, exceeding human response capabilities
By replicating human voices, scammers can impersonate trustworthy people. These scams often involve posing as family members or colleagues to deceive their victims and obtain sensitive information or money. They can be extremely convincing and difficult to detect without the right tools.
This ability to fully automate represents a paradigm shift in cybersecurity, enabling attackers to launch sophisticated operations without in-depth technical knowledge.
For more information on autonomous AI, access our post-> The future of autonomous AI: challenges and opportunities in cybersecurity
-
AI-generated hyper-personalized phishing
Phishing has evolved radically by 2026. AI allows us to create customized attacks in seconds with near-perfect realism.
Cybercriminals are using AI to automatically create official-looking documents, bypassing traditional security filters and employing social engineering techniques so advanced that they mimic genuine communication patterns.
-
Malware via WhatsApp
WhatsApp has become one of the most dangerous attack vectors in 2026:
- Lack of security filters compared to corporate email
- Circulation of malicious documents, images, and links without prior analysis
- Compromised devices turned into espionage tools
- Exponential risk for public figures and sensitive processes, such as elections
-
Deepfakes and disinformation
The deepfakes have reached an alarming level of sophistication and are being used in critical processes such as remote job selection.
These synthetic contents are also used for corporate fraud. Through fake videos of executives authorizing transactions, election manipulation and mass political disinformation, extortion using fabricated compromising content, and breaches of biometric facial authentication systems, this development calls into question the reliability of identity verification systems that we considered secure until recently.
-
Voice cloning with minimal samples
Voice cloning technology in 2026 requires barelyseconds of audio to create convincing replays:
- Telephone scams impersonating family members in emergency situations
- Corporate fraud through calls from fake executives
- Obtaining urgent bank transfers
- Compromise of voice authentication systems
The ease with which a voice can be cloned has made this type of attack one of the most effective and difficult to prevent.
-
AI-powered ransomware
The ransomware powered by AI has evolved to include capabilities that make it more devastating than ever.
The attacks are faster and harder to attribute to specific perpetrators, and small groups can scale up to massive operations using Ransomware-as-a-Service (RaaS). Experts confirm that ransomware will continue to rank among the top global threats, but now with exponentially greater capacity for damage, thanks to the integration of AI.
-
Data privacy issues
Artificial intelligence systems require massive amounts of data for training and operation, leading to the indiscriminate collection of personal information without explicit consent or user knowledge.
Companies that implement generative AI and language models are exposing sensitive customer and employee data through systems that can leak information via generated responses, creating unintentional privacy breaches.
The risk is compounded by the misuse of personal datato train business models without compensation or authorization from the owners, the exposure of sensitive information in autonomous AI systems that make decisions without human supervision, and the lack of transparency about what data is collected, how it is processed, and with whom it is shared.
-
Intellectual property infringement
Intellectual property infringement by AI has become one of the most complex and difficult legal risks to address. Generative AI models are being trained on copyrighted content without the original creators' authorization, including text, images, code, music, and artwork.
This creates multiple problems: the generation of content that infringes copyright by reproducing distinctive elements of protected works, sophisticated plagiarism through the creation of content that imitates styles and works of specific authors without attribution.
How to protect yourself from AI risks
Protecting yourself from AI-related personal online security risks requires education, advanced tools, robust security practices, and collaboration.
Education and Awareness
The foundation of good online security is education. Knowing the risks and how to deal with them is essential. People also need to stay informed about cybercriminals' latest tactics, including the use of AI.
Participating in online courses and webinars, and reading blogs specializing in cybersecurity, are effective ways to stay current. Continuing education allows us to recognize warning signs and respond appropriately to threats.
Source and Authenticity Verification
One of the most significant risks today is the threat of deepfakes, which use AI to create content that appears real. To protect yourself, it's crucial to always verify the authenticity of information before sharing or acting on it.
Verification tools, such as services that verify the authenticity of news and emails, can help identify and prevent deception.
Use Advanced Security Tools
Numerous security tools use AI to provide advanced protection. These include antivirus software, malware detection programs, and mobile security apps. These tools can analyze behavior in real-time, detect suspicious patterns, and alert users to potentially dangerous activities.
It's essential to keep these tools up to date to ensure they're equipped to deal with the latest threats.
Protection of personal data
The protection of personal data is critical in today's digital environment. People should be cautious about the information they share online. Setting your social media privacy settings to limit who can see and access personal information is essential.
It is critical to use strong, unique passwords for each account and change them regularly. Additionally, using password managers can help maintain security without the need to remember multiple passwords.
Multi-Factor Authentication
Multi-factor authentication (MFA) adds an extra layer of security. In addition to a password, MFA requires a second factor of verification, such as a code sent to a mobile phone. This makes it difficult for attackers to access the accounts, even if they manage to obtain the password. Implementing MFA across all accounts is an effective way to increase security.
Constant monitoring
Constant monitoring of accounts and online activity can help quickly detect unusual behavior. Setting up alerts for suspicious activity, such as login attempts from unrecognized locations, allows you to act immediately.
Some services monitor the use of personal information on the dark web and alert users if their data is at risk.
Collaboration and communication
Collaboration and communication with friends, family, and colleagues about cybersecurity can help build a support network and share best practices. Discussing common threats and how to deal with them can raise collective awareness and reduce the risk of falling into cybercriminal traps.
Qondar helps you protect your data and digital assets from AI threats
Qondar is the solution developed by Enthec to protect people's personal online information and digital assets.
Qondar monitors sensitive data, financial and patrimonial assets, and individual social profiles to detect public leaks of these assets and prevent their criminal or illegitimate use.
If you want to protect your digital assets or those of your organization's relevant members and avoid the dangers posed by artificial intelligence to humans, contact us to learn how Qondar can help.
AI in cognitive warfare: how are cyberattacks evolving?
When we talk about cyberattacks, we used to think almost exclusively of viruses, data theft, or system outages, but today the scenario is much more complex.
Technology, and especially artificial intelligence, has opened a new dimension to digital conflict: cognitive warfare. It's no longer just about breaking systems, but about influencing, confusing, and manipulating people's and organizations' perceptions.
AI in cognitive warfare has become an essential concept for understanding how cyberattacks evolve and why traditional defense is no longer sufficient. Threats target not only technical infrastructure but also decision-making, reputation, and trust.
What is cognitive warfare, and why does it matter?
Cognitive warfare is a form of conflict that seeks to influence how we think, decide, and react. In the digital environment, this translates into disinformation campaigns, identity theft, narrative manipulation, and attacks aimed at eroding trust.
Unlike classic cyberattacks, the objective is not always technical.. Sometimes, all it takes is one person clicking where he shouldn't, believing a false message, or making a bad decision under pressure.
AI in cognitive warfare amplifies this problem by enabling the automation and scaling of these attacks with a precision that did not exist before.
From systems to minds
Today, attackers no longer just look for vulnerabilities in servers or applications. They also look for human weaknesses such as lack of information, overconfidence, fatigue, urgency, and stress.
AI allows analyzing behaviors, adapting messages, and launching customized attacks in real time.. The result is a type of threat that is much harder to detect and stop.
The role of artificial intelligence in new attacks
Artificial intelligence is neither good nor bad in itself. The problem arises when it is used for malicious purposes.. In the field of AI in cognitive warfare, its use has spread rapidly.
More credible and personalized attacks
Thanks to language models and data analysis systems, attackers can create fake emails, messages, or documents that are almost indistinguishable from the real thing. This has increased the levels of phishing and spear phishing.

Large-scale disinformation
AI also facilitates the creation and mass dissemination of fake content, including manipulated news, fake social network profiles, and coordinated campaigns to damage the reputations of companies and individuals.
At this point, AI in cognitive warfare ceases to be a theoretical concept and begins to directly affect business, brand image, and the internal stability of organizations.
Why do traditional cybersecurity models fall short?
Many security strategies still rely on a reactive approach: protecting the perimeter, installing patches, and responding only after an incident occurs. The problem is that in cognitive warfare, damage often occurs before any technical alerts are triggered.
The limit of reactive safety
When an employee falls for a well-designed deception or a false narrative is spread internally, the impact can be immediate:
- Erroneous business decisions
- Loss of trust from customers and partners
- Unnecessary exposure to new threats
This is where a more advanced approach comes into play, focused on the Continuous Threat Exposure Management (CTEM).
CTEM: anticipate instead of reacting
The CTEM approach starts with a simple idea: Protection is not enough; we must continuously understand the threats we face.. This includes both technical assets and human and contextual factors.
In an environment shaped by AI in cognitive warfare, this type of management becomes especially relevant. The CTEM model
Cyber surveillance: a fundamental element in cognitive warfare
Cyber surveillance has become a fundamental tool for detecting early signs of attacks, especially those aimed at influencing or manipulating.
This is where Enthec adds value with its specialized solutions.
Kartos: cyber surveillance for companies
Kartos is geared toward organizations that need a clear, continuous view of their threat exposure. It goes beyond simply detecting technical vulnerabilities; it helps understand how and where an attack could originate, including those related to AI and cognitive warfare.
Among its capabilities are:
- Continuous monitoring of the attack surface
- Identification of emerging risks
- Support for CTEM strategies adapted to the business
This approach allows for informed decisions to be made before the problem escalates.
Qondar: protection for individuals in a hostile environment
Cognitive warfare doesn't just affect large companies. Managers, professionals, and individual users are also common targets.
Qondar Enthec's solution for individuals offers tools for cyber surveillance designed to protect digital identity and reduce personal exposure to increasingly sophisticated threats.
In a context where AI in cognitive warfare is infiltrating emails, social networks, and work platforms, having this type of support is no longer optional.
The human factor remains decisive
No matter how much technology is implemented, the human factor remains at the heart of the problem. The difference is that now the attacks are designed to exploit it systematically and rely on AI.
Awareness and context
It's not just about training users, but about giving them context:
- Understanding how threats evolve
- Knowing how to identify subtle signs of manipulation
- Having systems in place to support their decisions
The combination of awareness, clear processes, and CTEM tools is the best defense against AI in cognitive warfare.
Looking to the future: a silent but constant conflict
All indications are that these types of attacks will continue to grow. Artificial intelligence will continue to evolve, and with it, manipulation and deception techniques will evolve as well.
The question is no longer whether an organization or a person will be targeted by AI in cognitive warfare, but when and with what level of preparedness.
Adopting a Continuous Threat Exposure Management approach, supported by cyber-surveillance solutions such as Kartos and Qondar, enables a shift from a defensive posture to a conscious, proactive strategy.
Understanding to better protect
Cognitive warfare has changed the rules of the game. Cyberattacks no longer just seek to exploit technical flaws, but also to influence how we think and act.. AI in cognitive warfare is a reality that affects both companies and individuals.
Given this scenario, the key lies in understanding the actual exposure to threats, anticipating them, and having tools that offer continuous visibility.
If you want to know how to reduce your exposure and prepare for this new type of attack, discover the cybersecurity solutions from Enthec and take the first step towards a more conscious and present-adapted security.
The importance of maintaining security on mainframes and its impact on the business
Mainframes have been at the heart of many large organizations: banks, insurance companies, public administrations, energy companies, and large retailers continue to rely on them to process critical operations, manage huge volumes of data, and ensure business continuity.
However, this historical reliability has, in some cases, led to a false sense of security.
Today, talking about mainframe security is no longer a technical matter reserved for specialized departments. It is a strategic concern that directly affects the reputation, operations, and economic viability of any company that depends on these systems.
The current role of the mainframe in the modern enterprise
Although technology discourse often revolves around the cloud, artificial intelligence, and microservices, the reality is that mainframes still process a significant share of global transactions. Many organizations have modernized their environments by connecting the mainframe to APIs, web applications, and external services.
This new hybrid scenario has clear advantages, but also expands the attack surface. . The mainframe is no longer isolated in an internal "bubble": it now communicates with multiple systems, users, and vendors. And every connection is a potential entry point.
Mainframe security: a risk that is often underestimated
One of the most common mistakes is thinking that the mainframe is secure “by default.” It is true that its architecture is robust, but security does not depend solely on technology; it also depends on how it is configured, managed, and monitored over time.
In many corporate environments, worrying patterns continue to repeat themselves, such as excessive privileges granted to some users, inherited access from employees who changed positions or left the company, or outdated configurations that have not been updated to current standards.
These factors create a breeding ground for security flaws in mainframe environments, especially when the system is integrated with more modern open platforms.

The real impact of a breach in a mainframe
When an incident affects a peripheral system, the damage is usually limited. But when the problem is on the mainframe, the consequences multiply.
The following may occur:
- Serious service disruptions.
- Large-scale exposure of financial or personal data.
- Economic sanctions for legal non-compliance.
- Loss of trust from customers and partners.
These flaws not only facilitate unauthorized access but also complicate regulatory compliance (GDPR, ISO 27001, PCI DSS, among others).
Mainframe security testing: an essential practice
For years, mainframe security testing has been treated as a one-off event: annual audits, sporadic reviews, or reactive analyses after an incident. This approach is no longer sufficient.
Current reality demands an evolution from ad hoc review to continuous assessment. . Environments change, users rotate, permissions are modified, and integrations expand. Without constant visibility, it's impossible to know the true level of exposure.
Modern security testing should allow:
- Identify critical assets and their level of exposure.
- Detect insecure configurations before they are exploited.
- Prioritize risks according to their actual impact on the business.
- Measuring the evolution of security over time.
This is where new approaches like Continuous Threat Exposure Management (CTEM) come in.
CTEM applied to the mainframe: a necessary evolution
The CTEM model is not just about detecting vulnerabilities, but about understanding the company's actual exposure to specific threats. Instead of endless lists of alerts, it prioritizes what truly matters.
Applied to mainframe security, this approach provides a clear and up-to-date view of risk. This allows technical failures to be linked to their business impact, enables data-driven decision-making, and reduces the gap between technical teams and management.
Kartos by Enthec: Visibility and continuous control for companies
In this context, solutions like Kartos by Enthec provide clear value for companies that want to go a step further in protecting their critical systems.
Kartos is positioned as a cyber-surveillance tool, a cybersecurity solution for businesses and CTEM oriented to corporate environments,helping to continuously identify where the organization is truly vulnerable. It's not just about detecting problems, but about understanding their relevance and acting with sound judgment.
Among its main contributions are:
- Continuous visibility about assets and configurations.
- Early identification of security flaws in mainframe environments and connected systems.
- Risk prioritization based on operational impact.
- Support for continuous improvement strategies of security.
Mainframe security as part of the business strategy
One of the biggest changes in recent years is that cybersecurity is no longer just a technical issue. Today, mainframe security is part of the company's global strategy.
Good safety management reduces response times, prevents unexpected downtime, and improves coordination between teams.
The mistake of relying solely on one-off reviews
Many companies still rely on annual audits as their primary control mechanism. The problem is that the photo quickly becomes outdated.. A change in permissions, a new integration, or a forgotten account can generate exposure in a matter of days.
Experience shows that attacks and incidents don't wait for the audit schedule. That's why more and more organizations are opting for continuous monitoring models, supported by specialized tools.
A more realistic and sustainable approach
Having absolute control over all security is not realistic. What is possible, however, is to constantly reduce the attack surface, understand where the risks lie, and act before they become serious problems.
The combination of good practices, trained teams, and cyber-surveillance solutions such as Kartos enables us to move towards that goal in a sustainable and measurable way.
Does your company rely on a mainframe and lack real visibility into its exposure?
If you want to know what risks exist in your environment today, how to prioritize them, and what steps to take to improve your security posture, it's time to adopt a continuous approach.
Discover how Kartos by Enthec can help you consistently manage exposure to threats in alignment with your business.
CTEM (Continuous Threat Exposure Management) as a prominent cybersecurity approach
Cybersecurity has been making it clear for years that simply "having protection" is no longer enough. Firewalls, antivirus software, and occasional audits are still necessary, but the current context goes far beyond that.
Threats change rapidly, new vulnerabilities emerge every week, and the digital footprints of businesses and individuals grow constantly. In this scenario, CTEM (Continuous Threat Exposure Management) is establishing itself as one of the most realistic and effective approaches to continuously manage digital risk.
Talking about CTEM is not talking about a specific tool, but about a way of understanding cybersecurity as a living processunder constant review and adaptation. And this is where cyber surveillance solutions like Kartos and Qondar, developed by Enthec, fit naturally as pillars of a modern Continuous Threat Exposure Management strategy.
Why traditional cybersecurity is no longer enough?
For years, many organizations have relied on periodic reviews: cybersecurity audits, annual inspections, periodic penetration tests, or reviews conducted after an incident. The problem is clear:
Threats don't wait.
Furthermore, today it's not just servers or internal networks that need protecting. There are forgotten domains, leaked credentials, mentions on underground forums, exposure on social media, and misconfigured cloud services. All of this is part of the attack surface, and it changes constantly.
This is where the CTEM approach makes sense.
What is CTEM (Continuous Threat Exposure Management)?
CTEM defines a working model that seeks to continuously identify, analyze, and reduce the real risks to which an organization or person is exposed.
It's not just about detecting technical vulnerabilities, but about answering very specific questions:
- What digital assets are currently exposed?
- What sensitive information is circulating out of control?
- Which threats are real and a priority?
- What risks are growing without anyone monitoring them?
The key is in the word 'continuous': . CTEM is not a snapshot but a continuous monitoring process.
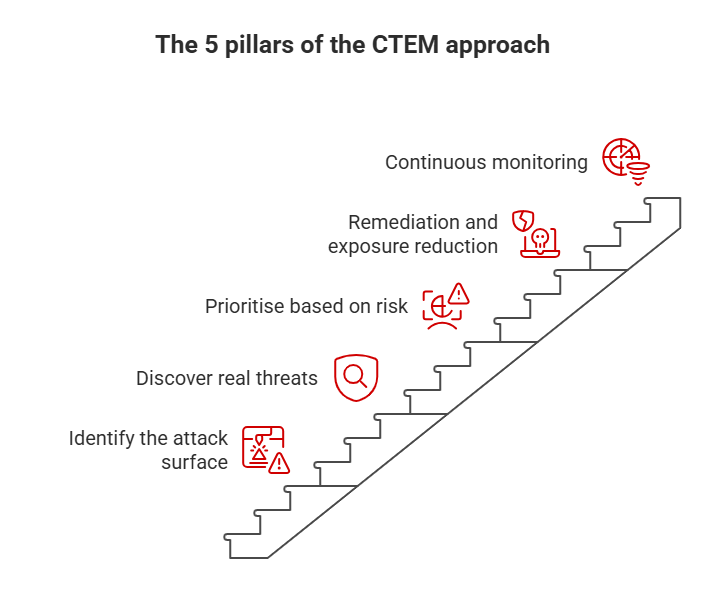
The five pillars of the CTEM approach
Continuous identification of the attack surface
The first step in CTEM is understanding what is actually exposed. Often, even companies themselves are unaware of all their digital assets: outdated subdomains, misconfigured cloud services, forgotten profiles, or even publicly accessible personal information.
A CTEM strategy involves constantly mapping that digital surface, not only at the beginning of a project.
Discovery of real threats
Not all vulnerabilities carry the same weight. CTEM focuses on exploitable threats, not only in endless lists of theoretical failures.
This is where cyber surveillance occurs: observing what is happening in forums, underground markets, leaks, or suspicious mentions related to a brand or a person.
Risk-based prioritization
One of the most common mistakes in cybersecurity is trying to fix everything at once. CTEM proposes prioritizing based on impact and actual probability, not just technical severity.
This allows resources to be dedicated to what really matters and reduces operational noise.
Remediation and exposure reduction
Detecting without acting is useless. The CTEM approach involves progressively reducing exposure by closing access, removing exposed information, or correcting insecure configurations.
Constant monitoring and continuous improvement
The cycle never ends. Continuous management involves starting over, reviewing, adjusting, and learning from each new finding.
CTEM applied to companies: Kartos as the cyber-surveillance solution
In the corporate sphere, Kartos, Enthec's enterprise-oriented solution, is a perfect CTEM tool.
What does Kartos contribute to a CTEM strategy?
Kartos allows organizations to:
- Monitor their digital exposure in real time.
- Detecting data leaks, compromised credentials, or mentions in non-visible environments.
- To have a clear and centralized view of external risk.
- Anticipating incidents before they become a bigger problem.
From CTEM's perspective, Kartos is not an isolated solution but a continuous monitoring system that feeds into cybersecurity decision-making.
This is especially relevant for companies with an online presence, multiple domains, cloud services, or remote teams, where the attack surface grows almost uncontrollably.
You might be interested in→ 9 healthy digital habits that will protect you from impersonation and data breaches
CTEM for individuals: Qondar and the personal protection
Managing ongoing threat exposure isn't exclusive to businesses. Professionals, managers, content creators, and anyone with a significant digital presence are also at risk.
This is where Qondar, Enthec's solution designed for individuals, comes into play.
The importance of CTEM at a personal level
Personal data leaks, identity theft, doxing, or misuse of private information are increasingly common risks. Qondar allows you to apply the CTEM approach to the personal sphere through:
- Monitoring of exposed personal data.
- Detection of compromised credentials.
- Monitoring mentions in open and non-conventional sources.
- Early warnings to act before the damage is greater.
In this way, the Continuous Management of Threat Exposure ceases to be a corporate concept and becomes a practical tool for everyday life.
Real advantages of the CTEM approach compared to other models
Adopting CTEM involves a change in mindset that offers clear benefits:
- Fewer surprises: incidents are detected earlier.
- Better use of resources: action is taken on real risks.
- Greater visibility of the digital exhibition.
- Progressive risk reduction, not just one-off patches.
Furthermore, CTEM is better suited to changing environments, where digital assets appear and disappear rapidly.
CTEM and the future of cybersecurity
Everything points to cybersecurity continuing to move away from static models. CTEM is one of the key approaches for the coming years, precisely because of its continuous and adaptive nature.
Organizations that adopt this approach will be better prepared for an environment where threats never rest, and digital exposure is constantly increasing.
Enthec and its commitment to Continuous Threat Exposure Management
Enthec has understood this market evolution and translated it into practical solutions. Both Kartos for companies and Qondar for individuals are designed with a clear CTEM logic, focusing on cyber surveillance, anticipation, and real risk reduction.
It's not just about reacting to incidents, but about constantly monitoring, understanding, and acting.
Does it make sense to apply CTEM in your case?
If you manage a business, a digital project, or your own online presence, the answer is usually yes. The question isn't whether there is exposure, but rather how much exposure you have right now and whether you are aware of it.
If you want to start applying the CTEM approach in practice, you can learn more about Kartos or Qondar and discover how continuous cyber surveillance can help you reduce risks before they become real problems.
Cybersecurity no longer allows for a reactive approach; we must be vigilant at all times. And in that regard, CTEM has become one of the best possible solutions.











