Financial data protection: the difference between reacting and anticipating
Financial data has become one of the most valuable assets for both individuals and businesses. But they are also one of the most coveted by cybercriminals.
Credential theft, fraud, leaks, or identity theft are threats that grow daily and are no longer limited to large corporations or banks. Today, anyone with a bank account or investments is a potential target.
Protecting financial data is not just about security but also about trust, stability, and prevention. However, most of the time we continue to act when the damage is already done. and therein lies the significant difference between reacting and anticipating: in the first case, we try to put out the fire; in the second, we prevent it from starting.
Qondar, the tool that helps you anticipate
Before we delve into how to protect your financial data effectively, we want to mention a solution we've designed precisely for that purpose: Qondar.
Qondar is a tool for cyber surveillance designed for individuals and grounded in the principles of Continuous Threat Exposure Management (CTEM). Simply put, it means not waiting for an attack to occur before taking action. Its approach consists of monitoring, detecting, and anticipating potential data leaks or exposures of personal and financial information online, on both the visible and dark webs.
Thanks to this continuous monitoring, Qondar helps identify early signs of risk, such as leaked credentials, compromised accounts, or sensitive information published on forums or in databases. In this way, users can react before the problem becomes a real loss.
If you're worried about digital security, of your personal and financial information, now is a great time to try Qondar and discover how it can help you stay one step ahead of threats.
Why protecting financial data should be a priority
In Spain and around the world, we've seen an increase in attacks related to the theft of financial data. It's not just about large-scale operations: many begin with simple phishing emails or unauthorized access to personal financial accounts.
At an individual level, the most frequent risks are:
- Theft of bank credentials through phishing or malware.
- Identity theft to apply for credit or to make fraudulent purchases.
- Unauthorized access to wallets or investment applications.
- Personal data leaks that allow for the creation of financial profiles.
For companies, the impact can be devastating: loss of customers, legal penalties, reputational damage, and recovery costs.
Reacting vs. anticipating: two very different strategies
When a data breach occurs, many people and organizations follow the same pattern: they discover the problem when it's already too late. This is the reactivo: se actúa después del ataque, tratando de reparar los daños, avisar a los afectados y reforzar las medidas de seguridad que ya han sido vulneradas.
In contrast, the proactive or anticipatory approach seeks to detect vulnerabilities before they are exploited . by providing visibility into where and how financial data could be compromised and acting proactively.
The practical difference between the two approaches is enormous.
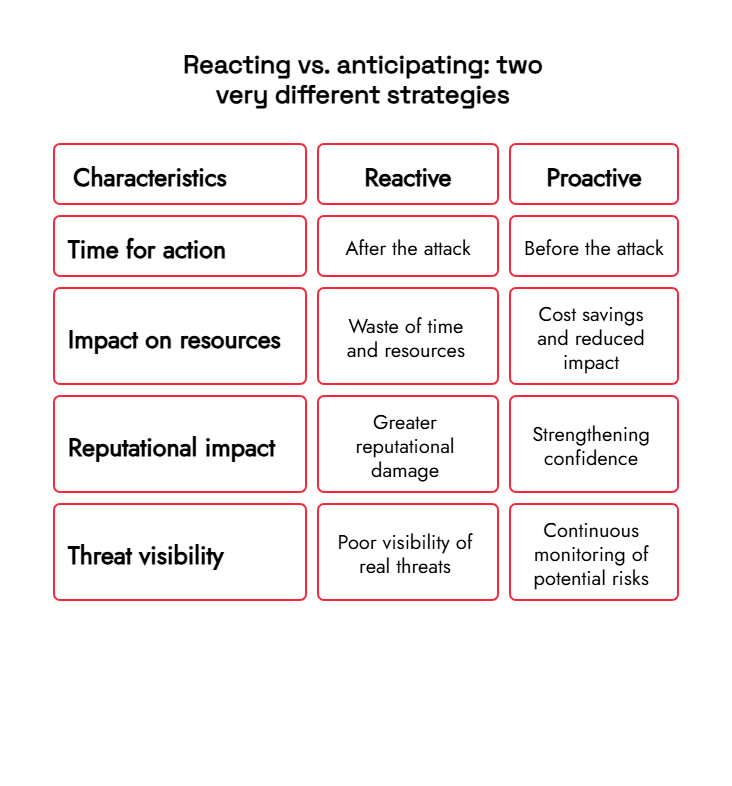
In other words, anticipation not only protects but also strengthens.
If you want to delve deeper into the term proactive approach, access our blog post→ Proactive security: what is it and why use it to prevent and detect threats and cyberattacks?
How to anticipate: the importance of the CTEM model
The CTEM approach starts with a simple idea: It is not enough to analyze risks once a year or after an incident.. Threats change every day, and security solutions must change too.
The CTEM model, used in solutions such as Qondar (for individuals) and Kartos (for companies), is based on three fundamental pillars:
1. Constant visibility
This is about maintaining active, continuous vigilance over the information circulating online. This includes detecting whether your financial data appears on forums, in illegal marketplaces, or in compromised databases.
With Qondar, this process is automated and updated in real time, avoiding reliance on manual or occasional reviews.
2. Exposure assessment
Not every exposure poses an immediate threat, but it's crucial to know what information is at risk and which one could be used against you. This analysis allows you to prioritize protective actions, focusing on what is truly urgent.
3. Early response and correction
The last step is to act quickly. When an exposure is detected. Qondar provides early alerts so users can cambiar contraseñas, revocar accesos o contactar con su entidad financiera antes de sufrir un ataque directo.
What can a person do to protect their financial data?
Although technology is essential, awareness and good practices remain the first line of defense. Some basic measures include:
- Avoid reusing passwords, especially for bank or investment accounts.
- Activate the two-step authentication on all platforms that allows it.
- Do not share personal or banking information through unverified emails or messages.
- Periodically check if your email address or data appears in filtered databases.
- Keep your device and app software up to date.
The key is to make protecting financial data a continuous habit, not in a one-off reaction to a threat.
Enthec: Cybersecurity as a process, not a patch
At Enthec, we specialize in offering solutions that integrate with this continuous, proactive approach. Our Kartos tool, for businesses, and Qondar, for individuals, enable dynamic management of exposure to threats and adaptation to changes in the digital environment.
Both solutions are designed under the philosophy that cybersecurity is not a product, but a living process that requires constant review, learning, and evolution.
In matters of financial data protection, responding can be costly. Not only in economic terms, but also emotionally: stress, loss of confidence, or the time spent regaining control are invisible but real costs.
Anticipating, on the other hand, is a way of safeguarding peace of mind.. Thanks to tools like Qondar; this prevention is no longer a luxury reserved for experts or large companies, but something accessible and valuable for anyone connected to the digital world.
Take the step towards more conscious and preventative security. Discover how Qondar can help you protect your information and your financial peace of mind Contact us
Why cyber surveillance is key to any CISO's strategy
Today, we can observe threats evolving rapidly and attackers operating with sophistication. Cyber surveillance has become an essential pillar for anyone responsible for an organization's security.
If you are a CISO or security manager, simply reacting is no longer enough: you must anticipate, monitor, and continuously manage risk exposure.
Before delving deeper into this topic, let's talk about Kartos, Enthec's solution designed for businesses. Kartos is a cyber surveillance tool designed to provide continuous insight into your company's exposure to threats, helping discover vulnerabilities, validate which risks are real, and prioritize mitigation actions.
Kartos is part of the operational muscle a CISO needs to sustain a modern cybersecurity program.
What is cyber surveillance: definition and scope
We could say that the most useful definition of cyber surveillance today is:
The practice of continuously monitoring the digital environment (both internal and external) for signs of threats, data exposure, emerging vulnerabilities, or suspicious activity, to respond as quickly as possible and reduce impact.
But that definition does not fully capture its strategic meaning. Cyber surveillance is not just about "being vigilant," but about doing so in a structured, automated way, focusing on what really matters to the company.
In more technical terms, cyber surveillance falls under the Continuous Threat Exposure Management (CTEM) framework, which goes beyond one-off vulnerability scans.
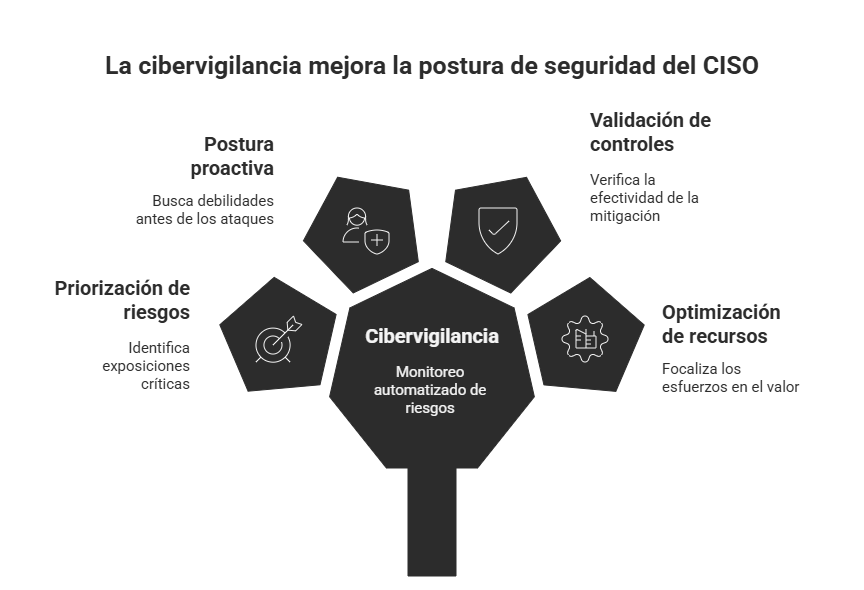
Why every CISO needs to incorporate cyber surveillance
1. The pace of risk doesn't wait.
Modern organizations typically identify tens of thousands of potential exposures each month. For example, according to a study by XM Cyber, an average of 15,000 exploitable exposures is identified across many organizations, with some exceeding 100,000.
With that volume, it is not feasible to manually review or prioritize without automating the risk criteria.
2. From reactive to proactive
Traditional security strategies (periodic scans, ad hoc tests) tend to fall behind in the face of constant change. CTEM, supported by cyber surveillance, allows us to move from a model in which we act after detecting an incident to one in which we look for weaknesses before they are exploited against us.
3. Risk-based and business-based approach
Not all vulnerabilities have the same impact. Cyber surveillance allows us to differentiate which exposures are critical to the business (for example, those that compromise sensitive data or critical processes) versus those that have little effect.
4. Continuous validation of controls
Detecting vulnerabilities is good, but how do you know if your controls effectively mitigate them? A cybersecurity surveillance solution like Kartos not only discovers flaws but can also validate whether the controls actually work in real-world scenarios through simulated attacks.
5. Alignment with the security strategy and resource optimization
A CISO cannot waste effort addressing minor risks. Properly implemented cyber surveillance allows a focus on the budget, team, and technical resources on what adds the most value.
How to apply cyber surveillance within the CTEM framework: key steps
For cyber surveillance to be effective, it should be framed within a clear CTEM cycle. The following are the recommended steps:
1. Scoping (delimitation)
Define which parts of the environment you are observing: assets, services, applications, cloud, external networks, etc. Set clear boundaries based on business value.
2. Discovery / Active Monitoring
This is where cyber surveillance, in the strict sense, comes in:it is crucial for detecting new assets, incorrect configurations, external exposures, leaked credentials, and suspicious activity. This monitoring must be automatic and continuous.
3. Prioritization of exposures
Not all detections warrant the same urgency. Here, each finding is evaluated based on ease of exploitation, potential impact, and business context. Cyber surveillance provides data (for example, whether that point is under attack) to improve this prioritization.
4. Validation / Simulation of attacks
It is not enough to see the vulnerability: It is necessary to validate whether it can actually be exploited. . Controlled simulations or advanced network teaming tests verify whether the risk is real. This bridges the gap between detection and action.
5. Remediation / Mobilization
Once validated, resources are allocated to mitigate or eliminate the exposure. Cyber-monitoring continues to confirm that the remediation is effective and does not generate side effects.
This cycle does not end: it returns to step 1 with continuous adjustments to maintain constant monitoring of the system.
Specific advantages offered by cyber surveillance
- Greater visibility without blind spots: what was previously unseen is revealed.
- The faster the earlier an exposure is detected, the smaller the window of risk.
- Reduction of actual risk: It is not enough to detect; it is also necessary to act reasonably and quickly.
- Continuous improvement: strategy evolves as threats and assets change.
- Better resource prioritization based on real risk avoids focusing efforts on irrelevant threats.
- Communication to the committee/managers: With quantified data on mitigated exposures, the CISO can demonstrate real impact on the business.
How Kartos fits into the CISO's strategy
Kartos, as a cyber-surveillance solution for businesses, is designed to be an active part of the CTEM cycle.. Some of its advantages are:
- It integrates detection, validation, and prioritization into a single platform.
- It provides a continuous view of the exposure, not just spot scans.
- It adapts to changes in the environment (new services, cloud environments, structural changes).
- It allows the CISO to demonstrate quantitatively how risk decreases over time.
- Connects with operational security processes (tickets, actions, tracking).
When cyber surveillance becomes an operational security muscle (rather than merely an informational layer), the CISO gains control over digital exposure.
If you are interested in learning how Kartos can fit into your organization and deploy an effective cyber surveillance program, you can request a demo or a personalized consultation. Contact us and we'll show you how to transform your security.
Today, more than ever, a CISO cannot rely solely on one-off scans or reacting only after an incident occurs. Cyber surveillance, understood as continuous, automated, and risk-based monitoring, is becoming essential for monitoring the digital landscape and reducing exposure.
By integrating it into a structured cycle like CTEM, cyber surveillance ceases to be an auxiliary function and becomes the backbone of the security strategy. In this context, solutions like Kartos by
Enthec can offer a real advantage: constant visibility, practical validation, and prioritization based on business criteria.
Act today. Strengthen your security with real and continuous cyber surveillance.
10 tips to protect your digital assets from cybercriminals
Our online history, bank accounts, family photos, and sensitive personal data are all part of what we might call your "digital treasure." And like any treasure, some try to steal it, damage it, or blackmail you with it.
Before analyzing this topic, we want to introduce Qondar, our solution designed for individual users to perform constant threat monitoring. With Qondar, you can automatically monitor potential leaks of your personal data on dark web sites, filter out relevant alerts, and receive support to address incidents.
If you want to take a step further to protect your digital assets, Qondar is a tool that you can use directly, without relying on an extensive infrastructure.
Below, we offer 10 practical tips along with small actions that will be very useful when an attacker tries to compromise your digital assets.
Why is it urgent to protect your digital heritage?
Every year, the volume of attacks targeting individuals and businesses grows significantly. In Spain, for example, a recent increase of more than 20% in malware detections has been observed (
Cybersecurity in Spain: Impact and Keys to the Rise of Malware in Europe
)
In addition, the financial losses from cybercrime can be severe: Many ransomware, phishing, and credential theft attacks target both businesses and individuals.
Therefore, it is not enough to “hope it doesn’t happen to me”: we must act in advance.

1. Take an inventory of your digital assets
Before you can protect something, you need to know what you have to protect. . That includes:
- Online accounts (email, social media, banking, trading platforms, cloud storage services)
- Passwords, private keys, cryptographic keys
- Backups, important files
- Photos, videos, scanned documents
- Personal data such as scanned ID, passports, and medical certificates
- Digital identities: profiles, online reputation
Having an inventory will help you prioritize based on asset value and vulnerability. categorization (e.g., “very critical,” “important,” “less critical”). You can apply different measures depending on the risk level.
2. Use strong passwords and manage authentication well
This advice is more vital than many think:
- Avoid using overly obvious passwords (names, birth dates, dictionary words).
- Use long passwords with mixed characters (uppercase, lowercase, numbers, symbols).
- Do not repeat passwords between services.
- Use a secure password manager to generate and store strong combinations reliably.
If you want to delve deeper into this aspect, we recommend you take a look at our content→
How to manage business passwords and credentials easily and securely to avoid online threats
.
And, in addition:
- Activate the
multi-factor authentication
whenever possible. - Use the second step based on an app (Google Authenticator, Authy) or physical keys (such as YubiKey), instead of SMS, which can be intercepted.
- If your manager allows it, configure additional authentication or a local lock.
A strong password combined with 2FA significantly reduces the likelihood of someone accessing your accounts without your permission.
3. Make backups (and check their integrity)
Even the best-protected system can fail. So:
- Have regular backups of your most valuable files.
- Save these copies in different places: external drive, cloud server, and offline storage.
- Encrypt the copies, especially if they contain sensitive data.
- Check from time to time that the backups are working and that you can restore them correctly.
Backup is your digital insurance. against an attack that deletes or encrypts your files; having copies gives you a recovery option.
4. Keep your devices and software always up to date
Many attacks exploit known vulnerabilities that already have
patches
available:
- Activate automatic updates whenever possible (operating system, browser, antivirus, applications).
- If a critical application is no longer updated (due to manufacturer abandonment), reconsider using it or look for alternatives.
- Don't neglect obsolete systems: Even older smartphones or routers can become vulnerable if you don't update them.
An updated system significantly reduces classic attack vectors (known exploits).
5. Beware of phishing and digital scams
Many cybercriminals choose to trick you into giving them your keys:
- Don't click on suspicious links, even if they appear to be from reliable sources.
- Always check the sender's real domain.
- Be wary of urgent messages (e.g., “your account will be blocked”) that demand immediate action.
- Do not provide personal information (ID, card numbers) via email or text message.
- Always verify through another channel whether a message you receive really comes from the entity it claims to.
This type of scam is one of the most common, precisely because many users let their guard down.
You might be interested→
Phishing: what it is and how many types there are
.
6. Monitor your digital exposure (detect leaks and infiltrations)
One of the keys to protecting digital heritage is to find out if your data has already been compromised:
- Use monitoring tools to find out if your credentials or data appear on leaked lists or on the dark web.
- Qondar (Enthec's solution for individuals) offers precisely this capability: continuous threat monitoring, alerts when it detects that any of your data has been exposed, and practical instructions for action.
- When an alert occurs, act quickly: Change passwords, block access, verify account integrity.
Detecting a leak early minimizes damage.
7. Segment and control access to your accounts
Do not give more permissions than necessary:
-
- Use user accounts with limited permissions for everyday tasks (avoid always using the administrator account).
- In home networks, segment equipment (e.g., guest network, IoT device network).
- Check which apps have access to your accounts (OAuth authorizations, social media permissions) and revoke the ones you don't use.
- If you share devices, create separate profiles and prevent others from using your session.
The fewer privileges an access has, the less damage it can cause.
8. Encrypt your sensitive data
Encryption is a powerful barrier:
- Encrypt entire disks (BitLocker, FileVault, LUKS)
- Use encryption when transferring data (TLS/SSL, VPN connections).
- Use storage services that are end-to-end encrypted (so that not even the provider can read your data).
- For very sensitive data, you can use file encryption software (e.g., VeraCrypt).
This additional level means that even if someone accesses the file or disk, they cannot read it without the key.
9. Maintain an attitude of vigilance and habit
Protection is not a single action, but a habit:
- Regularly review logs, alerts, and access to your accounts.
- Don't ignore alerts, even if some are false; analyzing them is better than ignoring them.
- Update your digital inventory with new services, accounts, or devices.
- Stay informed: threats are evolving. Read news, specialized blogs, and cybersecurity reports.
10. Plan your incident response
Protecting isn't just about preventing: you must be prepared to act if something goes wrong:
- Define a simple plan: what to do first if you detect unauthorized access, leaked data, or receive a blackmail attempt.
- Have contacts for technical support, suppliers, banks, or services you work with on hand.
- Use recovery tools (e.g., restore from backup).
- Keep records of the incident (logs, screenshots) that could be used in a legal claim or complaint.
- Consider hiring specialized protection: Qondar can help you not only detect threats, but also manage ongoing exposure and provide incident support.
Today, digital exposure is constant,from email to the cloud to your smartphone. But protecting your digital assets is possible if you take the proper measures. You don't need to be an expert: with discipline, good tools, and a little vigilance, you can significantly reduce the risk.
If you are concerned about your safety and
personal privacy
in the digital world, we invite you to learn about Qondar, a practical tool for individuals who desire constant monitoring and active alertness.
Want to learn how to get started with Qondar or create a personalized digital protection plan? Contact us and we will help you.
Red team in cybersecurity: how it works
The term red team is sparking interest in the world of computer security: what exactly does it mean, how does it work, and why is it useful? In this article, we'll clearly and comprehensively explain what it is, its advantages, its limitations, and how it fits into a modern defense strategy like the one we offer at Enthec with our Kartos solution.
Before diving in, it's a good idea to learn a little about Kartos: it's a cyber surveillance solution designed for businesses that seeks to offer Continuous Threat Exposure Management (CTEM). In other words, Kartos helps you permanently identify weak points in your infrastructure, prioritize the most dangerous ones, and ensure that vulnerabilities don't reappear.
What is a red team?
A red team is a specialized team that simulates the role of a real attacker to test an organization's security. Rather than just performing spot tests, their approach seeks to replicate advanced techniques, combining technical, human, and sometimes physical methods to determine if an adversary could compromise critical assets without being detected.
In the cybersecurity sector, “red teaming” means turning those simulations into intentional and structured exercises, with defined objectives, clear rules, and mechanisms to learn from the results.
Unlike a routine vulnerability audit or scan, a red team seeks to emulate how a real attacker, with the resources, skills, and patience, would attempt to infiltrate, hide, move laterally, and achieve a goal (e.g., exfiltrate data).
A red team executes an adversary emulation exercise on a network, system, or IT environment to identify critical flaws and gaps that are difficult to detect using other methods.
Red teaming vs. penetration testing (pentesting)
It is common to confuse red team with pentesting, but there are key differences:
- Pentesting is usually more limited in time or scope, focusing on finding specific known vulnerabilities.
- The red team, on the other hand, is more free and prolonged, aimed at seeing if an attacker can achieve a fundamental objective, not just list faults.
- Red teaming also assesses the detection and response capabilities of internal teams, not just the presence of vulnerabilities.
- The red team often operates without warning or with minimal visibility to simulate real-life conditions.
A red team exercise can last weeks, involve multiple vectors (email, remote access, phishing, deception, social engineering), and conclude with a report detailing the progress made, the detections, and the defensive flaws that need to be addressed.

How a red team works: typical stages
To better understand this, I'll break down the typical phases of a red team exercise:
1. Definition of objectives and scope
Before attacking, the intended targets are agreed upon (e.g., accessing sensitive data, gaining administrator access, leaking information), and systems are evaluated as either within or outside the perimeter (what is excluded). Rules of engagement are also established to prevent unwanted damage.
2. Reconnaissance/intelligence
The team gathers public, internal, or compromised information about the organization: domains, employees, networks, exposed services... This allows for the construction of realistic attack scenarios.
3. Initial exploitation/entry point
Here, the red team uses vulnerabilities, phishing, weak credentials, or social engineering to gain a foothold within the target network. This involves gaining initial access without being detected.
4. Persistent access and lateral movement
Once inside, the simulated attacker escalates privileges, moves laterally, explores the network, searches for other vulnerable systems, and moves toward the defined target.
5. Goal achievement / final scenario
The red team, if successful, carries out the planned scenario: data extraction, maintaining a hidden presence, etc.
6. Report and recommendations
The team delivers a report with findings, attack routes used, points where attacks were stopped or detected, and recommendations for correcting weaknesses.
7. Correction and validation phase
Recommendations are reviewed, issues are corrected or mitigated, and in some cases, a subsequent verification (light re-red teaming) is performed to confirm that the improvements have been practical.
These stages allow us to understand not only where there are vulnerabilities, but also how an intelligent attacker would exploit them in a real-life environment.
Advantages of the red team within a CTEM strategy
Incorporating red teaming as part of a CTEM strategy brings benefits that go beyond simple fault finding:
- Dynamic visibility: With red teaming, you discover how holes interact with each other and how they might combine to form critical attack paths.
- Realistic prioritization: It is not enough to fix all the bugs; you have to know which ones can actually be exploited.
- Continuous evaluation of defenses: Helps test detection, alerts, and response capabilities.
- Culture of constant improvement: Encourages security and operations teams to advance and evolve.
When integrated with a platform like Kartos, red teaming becomes part of the CTEM cycle, as it is not a one-off exercise but rather an ongoing process of monitoring exposure to threats.
Furthermore, by being part of a CTEM framework, the red team's results are automatically fed back: new findings are integrated into the platform, prioritized based on their impact and risk, and periodic measurements are taken to verify that exposure is being reduced. This is the core of the Continuous Threat Exposure Management approach.
Limits and risks of the red team
Although the red team is very valuable, it's not a perfect or magic solution. It's essential to understand its limitations:
- Cost and time: these exercises often require specialized human resources and extended deadlines. Not all organizations have the budget for frequent red teaming.
- Partial coverage: An exercise cannot attack all possible systems, environments, or vectors, so there are “blind spots” in areas.
- Risk of interruptions: If not well planned, the simulated attack could cause failures or overloads in production systems.
- Limited in time: The threat landscape is changing; what works today may not work tomorrow. That's why red teaming, as a stand-alone exercise, is no substitute for ongoing vigilance.
For all these reasons, a good approach is to use red teaming in combination with other forms of assessment (continuous analysis, automated scans, more frequent simulations) within a CTEM framework.
How Kartos fits into this equation
Here is Enthec with its Kartos tool, a CTEM platform that allows:
- Integrate the red team's results into the ongoing exposure vision.
- Prioritize detected risks based on impact, probability, and complete attack paths.
- Monitor whether the proposed fixes have actually been applied or whether errors reappear.
- Automate alerts, reports, and follow-up tasks to maintain a secure posture over time.
Good practices for successfully using Red Team
For a red team exercise to truly deliver value, it's recommended to follow these practices:
- Define clear, realistic, and business-aligned objectives.
- Establish strict rules of engagement (what can be touched, what can't, what levels of risk do you accept).
- Maintain secrecy or controlled visibility (depending on the purpose).
- Involve the internal response team, at least in the reporting and correction phase.
- Incorporate lessons learned into the CTEM cycle so that they are not isolated.
- Repeat with partial frequency (for example, with minor exercises) to prevent the organization from settling.
- Measure its effectiveness with detection times, percentage of compromises detected, improvements after corrections, etc.
With these practices, red teaming ceases to be an isolated event and becomes a powerful lever for ongoing improvement and strengthening.
Red teaming is an advanced and powerful technique for simulating real attacks, assessing an organization's defenses, and discovering attack paths that other methods would miss. Red teaming within a CTEM framework, for example, by integrating it with the solution Kartos by
Enthec,
multiplies its value: it is not a one-off exercise, but part of a continuous mechanism for evaluating and improving the security posture.
If your company is already using monitoring or scanning tools, adding red teaming (in a well-balanced way) can significantly increase the level of security. Ideally, these results shouldn't be isolated but rather integrated into a CTEM strategy to ensure improvements are maintained over time.
Reasons to use multi-factor authentication in companies
Cybersecurity is no longer the exclusive domain of technical departments; it has become a strategic priority for all companies, regardless of their size and scope. Cyberattacks have become increasingly sophisticated, and criminals are no longer just after financial data; they are also targeting confidential information, login credentials, internal plans, and any digital trace that can be used for their own benefit.
In this scenario, protecting user accounts with a simple password is no longer sufficient:
phishing attacks,
credential theft, and password reuse make it essential to strengthen access controls.
Today, we want to discuss multi-factor authentication (MFA), an additional layer of security that can be a valuable ally in preventing
security breaches
.
Before delving into the details of how it works, it is worth mentioning Kartos, the solution for Continuous Threat Exposure Management (CTEM) developed by Enthec. Designed for businesses, Kartos enables organizations to continuously understand their exposure to potential digital risks, detect vulnerabilities, and anticipate attacks before they occur.
Multi-factor authentication is a fundamental step in this overall protection strategy, as it reduces the attack surface at one of the most critical points: access to accounts and systems.
What is MFA, and why is it so important?
To understand the need for this system, it is helpful to answer the question: What is MFA? Multi-factor authentication is an identity verification method that requires the user to present two or more pieces of evidence before accessing a digital resource. Simply put, a regular password isn't enough; you need to provide one or more additional verifications.
These tests are based on three main categories:
- Something you know: a password, PIN, or security question.
- Something you have: a code sent to the mobile phone, a physical token, or an authentication application.
- Something you are: facial recognition, fingerprint, or voice.
When we combine at least two of these categories, the chance of a cybercriminal gaining access, even if they steal the password, is drastically reduced.

Examples of multi-factor authentication
Although it may seem like a complicated technology, the reality is that we use it almost unconsciously in our daily lives. Some common examples of multifactor authentication are:
- Access to online banking: In addition to your password, you receive a code via SMS or an authentication app.
- Corporate email: The company requests a temporary code generated by an app such as Google Authenticator or Microsoft Authenticator.
- Social networks and cloud services: You are asked to confirm access from your own mobile device.
These examples of multi-factor authentication demonstrate that its use not only increases security but has also become a natural practice, accepted by both users and organizations.
Main benefits of multi-factor authentication in companies
Implementing an MFA system not only translates into a higher level of security but also into multiple advantages that affect the business as a whole.
1. Reducing the risk of credential theft
Password theft is one of the most common techniques used in cyberattacks. With MFA, even if attackers gain access to your password, they will still need a second factor to gain access.
2. Regulatory compliance
Increasingly, data protection regulations, such as the General Data Protection Regulation (GDPR) or the National Security Scheme (ENS) in Spain, recommend or even require additional authentication mechanisms. Implementing MFA helps meet these standards.
3. Trust and reputation
Customers and partners appreciate a company's commitment to security. Adopting measures such as multi-factor authentication helps build trust and strengthen the company's image in the market.
4. Lower long-term costs
Although implementing MFA involves an investment, the truth is that preventing a security breach can save thousands of euros in fines, data loss, and reputational damage.
5. Flexibility and adaptability
Today, there are multiple MFA solutions, from SMS to advanced biometrics. This allows companies to choose the option that best suits their size, sector, and needs.
Multi-factor authentication and CTEM: a necessary combination
Multi-factor authentication is just one piece of a much larger puzzle: that of continuous threat exposure management (CTEM).. Adopting MFA protects access, but security must go further.
This is where solutions like Kartos can help your business. Kartos not only helps implement security controls but also provides a constant view of the company's digital attack surface, detecting potential weak points and facilitating a rapid response to any threat.
There's little point in implementing multifactor authentication if we don't know what other entry points might be open. That's why the CTEM approach is so valuable: it anticipates, monitors, and mitigates risks in real-time, integrating measures such as MFA into a comprehensive global cybersecurity strategy.
Common obstacles and how to overcome them
Not all companies take the step immediately. Among the most common barriers to implementing MFA are:
- Employee resistance:Some individuals view MFA as an additional step that complicates access to accounts. The key is communicating the benefits and choosing simple methods, such as mobile apps.
- Initial cost:Although there are very cost-effective solutions, some companies perceive the investment as a hindrance. However, compared to the price of a security breach, MFA is much more cost-effective.
- Integration with legacy systems:In organizations with outdated software, this can be more difficult. However, some integrators and solutions allow for gradual adaptation.
Experience shows that these obstacles can be overcome through training, awareness, and the strategic use of technology.
You may be interested in→
Cyberintelligence: what it is and what are its advantages at the strategic and tactical levels
.
The future of multi-factor authentication
Everything suggests that MFA is evolving toward even more convenient and secure methods. Biometrics, physical security keys, and artificial intelligence-based solutions will mark the next stage. There's even talk of a passwordless future, where authentication will be based on stronger, harder-to-fake factors.
For businesses, adopting MFA today is a step forward toward tomorrow's security. . It's not just a tool for the present, but the foundation on which the future of digital protection will be built.
Multi-factor authentication is not a fad or an optional extra: it is a necessity for any company that wants to protect its information, comply with regulations, and instill confidence in its customers. Integrating it into a broader security strategy, such as the one offered by Enthec's Kartos through its CTEM approach, is the best guarantee that corporate access will be protected against attacks.
In an environment where cyberattacks are becoming increasingly frequent, failing to act promptly can be costly.. If your organization still relies solely on passwords, it's time to strengthen security.
Discover how
Enthec
can help you implement proactive protection and enhance your company's security.
Cybersecurity in teleworking: 7 habits every professional needs
Working from home has become routine for millions of people in Spain. What was initially an improvised solution is now a well-established reality in many sectors.
However, this change has also introduced new risks, including an increase in cyberattacks targeting employees working remotely. Therefore, discussing cybersecurity in the context of teleworking is essential.
In this context, having tools that strengthen our protection is essential. One of them is
Qondar,
Enthec's solution designed for individuals. Qondar is not just an antivirus or a point-in-time solution: it's a Continuous Threat Exposure Management (CTEM) solution, which means it constantly monitors for risks and reduces the attack surface.
Before exploring the practical habits you can implement starting today, it's worth remembering the essentials: taking care of your digital security not only protects your personal data but also safeguards your professional image, your company, and your work environment.
1. Always keep your devices updated
It seems obvious, but it's one of the most common mistakes. We often postpone updates because they interrupt our work, without realizing that those small downloads usually contain critical security patches.
- Operating systems, such as Windows, macOS, or Linux, frequently release updates to address known vulnerabilities.
- The same thing happens with everyday applications, such as browsers, office suites, and video calling tools.
A cyberattacker only needs one crack. If you keep everything up to date, that entry point disappears.
2. Separate the personal from the professional
Teleworking has blurred the lines between home and office, but that doesn't mean we should use the same computer for everything.
- If your company gives you work equipment, use it exclusively for that purpose.
- If you use your personal computer, create different user profiles for leisure and work.
This way, if you download a suspicious file in your free time, the impact on your work information will be less. This simple habit can make a significant difference in protecting your projects and maintaining your clients' trust.
You might be interested→
How to protect your digital identity against major threats
.
3. Strengthen passwords and use two-factor authentication
Cybercriminals are aware that many users still use passwords such as "123456" or "password." And what's worse: they repeat the same password across multiple services.
- Opt for long sentences or unique combinations that include letters, numbers, and symbols.
- Use a password manager to store them safely.
- Activate two-factor authentication (2FA) whenever possible: a code that arrives on your mobile phone or email, adding an extra layer of security.
This habit, although it may seem complicated and slow, drastically reduces the possibility of unauthorized access and ensures that your
sensitive data
is not circulating on the Internet.

4. Be careful with public Wi-Fi networks
Working from a coffee shop may sound tempting, but the free connection you use may be exposed. According to the National Cybersecurity Institute (INCIBE), open networks are one of the most common points used by cybercriminals to intercept data.
If you have no other option:
- Use a VPN to encrypt the information.
- Avoid sending sensitive files or accessing bank accounts over these connections.
On the other hand, if you work from home, make sure your router is configured correctly, with a secure password and updated firmware.
5. Be wary of suspicious emails
Phishing remains the king of attacks. An email that appears to come from your boss or a trusted company may hide a malicious link.
To detect them:
- Look at the actual sender address.
- Check if there are spelling mistakes or suspicious alerts (“Change your password in the next 10 minutes”).
- Never download attachments you weren't expecting.
This is where solutions like Qondar excel, as they allow you to detect exposed information and prevent it from being used to design a phishing attack before it's too late.
6. Lock and protect your devices
Teleworking doesn't always happen in safe spaces. You can be at home, but you can also be in a shared or coworking space. Leaving your laptop without a password, even for "just a moment," is opening the door to trouble.
- Always activate automatic locking after a few minutes of inactivity.
- Protect your equipment with a secure password or PIN.
- On mobile phones and tablets, utilize biometric systems, such as fingerprint or facial recognition.
Physical carelessness can be just as dangerous as a cyberattack.
7. Monitor your digital footprint with advanced tools
The last habit is the least known, but it is increasingly necessary. When we work remotely, we leave digital traces constantly: platform access, cloud logs, social media posts... Cybercriminals can exploit all of this.
This is where continuous cyber surveillance comes in. It is not about being paranoid, but about having systems that monitor your actual online exposure.
With Qondar, Enthec offers just that capability: detecting in real-time if your credentials have been leaked on forums, if your email address appears in compromised databases, or if there are active threats related to your profile. This way, you not only react once the attack has already occurred, but you also prevent it before it happens.
Additional tips to strengthen cybersecurity when working remotely
In addition to the seven habits above, there are other details worth keeping in mind:
- Encrypt your disks and backups to prevent irreversible data loss.
- Disconnect external devices when you are not using them.
- Be an active participant in your company's cybersecurity culture by engaging in training and drills.
Remember: digital security depends not only on the IT department, but on every person who uses a computer connected to the Internet.
Protect your business and your peace of mind
.Cybersecurity in teleworking is not just a set of good practices; it is an investment in peace of mind and business continuity. Cybercriminals never rest, but you can be prepared.
With simple habits and the support of Continuous Threat Exposure Management solutions like Qondar, you can work remotely as securely as in a secure office.
If you want to take it a step further and protect your business and personal data, discover how
Enthec
can help you with its solutions tailored to both companies (
Kartos
) and professionals and individuals (Qondar).
Discover Qondar and see how Cyber surveillance can become your best ally in your daily teleworking routine.
Contact us
.
How to protect yourself from stalkerware with digital monitoring tools
Stalkerware is a type of spyware designed to monitor a person without their consent. . Although it sometimes disguises itself as a legitimate app, its primary goal is clear: to collect private information, including messages, locations, calls, and even passwords.
The problem is more common than it appears, and every year, more cases are reported in which individuals discover that their devices have been compromised.
In this context, preventive cyber surveillance has become a necessity, not only for businesses but also for individuals. Enthec, a company specializing in Continuous Threat Exposure Management (CTEM), has developed solutions capable of detecting and reducing digital risks before they become a problem.
For individuals, Qondar is the key tool. It is a system designed to monitor each person's digital footprint and provide alerts if suspicious behavior is detected.. In a world where digital harassment is on the rise, having an extra layer of protection can be the difference between feeling safe and living under invisible surveillance.
What is stalkerware, and why is it so dangerous?
Stalkerware is a type of spyware that is especially invasive. Unlike other malware that seeks to steal money or access corporate data, this one focuses on monitoring a person's private life.
Characteristics of stalkerware
- Concealment: It usually runs in the background, with no visible notifications.
- Full access: You can read messages, listen to calls, track GPS location, or even activate the camera and microphone.
- Easy installation: In most cases, a few minutes of physical access to the device is all that is required to install it.
The most concerning aspect is that we're not always discussing unknown cybercriminals. Often, the person who installs stalkerware is someone close to them, such as a partner, family member, or even a boss seeking to control them beyond what's allowed.
How to know if I have stalkerware
The big question for many is how to detect stalkerware on a device. Although it's not always obvious, some signs can alert us.
Most common signs
- Battery draining too quickly: Spyware consumes resources by being constantly active.
- Device overheating: This issue occurs even when the device is barely used.
- High mobile data usage: Stalkerware requires transmitting the collected information.
- Strange behaviors: unexpected restarts, crashes, or apps that appear without explanation.
If you've ever wondered, “How do I know if I have stalkerware?”, pay attention to these signs. They're not definitive proof, but they are a clue to take action.

How to safely detect stalkerware
Manual detection can be tricky, as these types of programs are designed to go undetected. However, there are helpful strategies:
Check your app permissions
Many legitimate apps request access to your location, camera, or microphone. But if you see an unknown app with suspicious permissions, it's time to take action.
Install digital monitoring solution
This is where tools like Qondar come in, enabling you to monitor your digital exposure continuously. It's not just about looking for malware, but also about determining whether there are personal data leaks, unauthorized access, or traces that may provide clues to a stalker.
Keep your devices updated
Manufacturers release updates to fix vulnerabilities; . if you ignore them, you leave the door open to more uncomplicated and severe intrusions.
The role of digital monitoring against stalkerware
In the past, digital protection was limited to installing an antivirus. Today, that defense is no longer sufficient. Stalkerware evolves rapidly and can disguise itself as any other app.
The key is to anticipate threats through continuous monitoring and vigilance. The concept of Continuous Threat Exposure Management (CTEM) goes beyond simple detection: it involves monitoring the digital footprint 24/7, identifying potential risks, and reducing them before they become a real problem.
Qondar: a solution designed for people
While Kartos is Enthec's tool designed for businesses, Qondar focuses on individuals. Its purpose is clear:
- Monitor personal digital exposure.
- Detect leaks of sensitive data on the net.
- Alert about threats that may be related to the use of stalkerware or cyberbullying.
The interesting thing is that Qondar not only reacts, but offers preventive information, . which means you can find out if your email, passwords, or social profiles have been compromised before someone uses them to spy on you.
In a context where digital harassment and unwanted surveillance are becoming increasingly frequent, having this type of service provides genuine peace of mind and security.
Good practices to reduce risk
While having tools like Qondar is essential, there are also practical steps you can take in your daily life:
Strengthen your passwords
Use long, unique combinations for each account. Avoid repeating the same password across different services.
If you want to delve deeper into this topic, we recommend our publication → How to manage business passwords and credentials easily and securely to avoid online threats
Activate two-step verification
Even if someone obtains your password, they will still need a second factor of authentication to gain access.
Check your devices
Clean up your apps periodically and delete any you don't recognize or use.
Talk about cybersecurity
Cyberbullying is still a taboo subject. Sharing information with family and friends helps you be more prepared.
What to do if you suspect stalkerware
If you detect clear signs that your device may be compromised, it is recommended to:
- Disconnect the internet temporarily to cut off data transmission.
- Make a backup of your most essential files.
- Reset the device to factory settings.
- Use monitoring tools like Qondar to ensure you are not exposed again.
Digital security starts with you
Stalkerware isn't a distant problem or exclusive to celebrities. Anyone can be a victim, which is why it's crucial to be informed and have advanced protection tools.
Today, digital security is no longer limited to installing an antivirus. It requires constant monitoring and CTEM solutions, such as those offered by Enthec with Qondar. If you want to feel more secure in your digital life and prevent third parties from accessing your privacy, taking the step toward this type of protection is an investment in peace of mind.
Want to learn more about how Qondar can help you protect your digital privacy? Visit Enthec and learn how to safeguard your personal information from threats like stalkerware today.
ClickFix: What to do if you click on a malicious link
We've all experienced that moment of doubt. You're checking your email, browsing social media, or even chatting at work, and suddenly a seemingly harmless link pops up. You open it without giving it much thought... and instantly realize something's off. That's when the question arises: what do I do now?
In this article, we are going to talk about ClickFix,a term that refers to the immediate actions you should take after clicking on a malicious link. We'll give you practical advice and explain how solutions like Qondar, developed by Enthec, can help you reduce your risk and stay ahead of these threats.
What exactly is a ClickFix?
A ClickFix is the set of emergency measures you should take when you have already made the mistake of clicking on a fraudulent link.. It isn't the time to lament, but rather to react quickly to minimize damage. The longer you delay acting, the easier it will be for attackers to exploit your device or your data.
Instead of panicking, the most helpful thing is to have a clear response protocol in place. . You don't have to be an expert to apply it: with a little organization and the right tools, you can turn a scare into an anecdote without significant consequences.
The absolute risk of a malicious click
A wrong click can have several consequences:
- Malware downloads onto your device, which can slow it down, remotely control it, or steal information.
- Phishing occurs when the fraudulent website imitates an official page (a bank, a social network, an online store) and asks you for credentials or sensitive data.
- Exposure of personal data, which can then be sold on dark web forums.
According to the Global Risks Report 2025, by the World Economic Forum, cyber threats are already among the top issues worrying both businesses and citizens in the short term, and phishing attacks remain the most common entry point.

ClickFix Quick Start Guide: Step-by-Step Instructions
Once you've clicked on a malicious link, the most important thing is not to get blocked. Order is key, because every action helps cut off potential avenues of attack and protect your personal information.
1. Disconnect the device
If you suspect that the link has downloaded something or that the page is not trustworthy, the first thing is to disconnect the device from the internet.. This prevents the malware from communicating with the attacker.
2. You do not provide data
If you have reached a website that asks for credentials, don't fill anything in.. If you did, immediately change the passwords for those services from another secure device.
3. Scan the system
Run updated antivirus software and use specific malware removal tools. It's important not to let time pass.
4. Review access and suspicious activity
Check your email, social media, and bank accounts. Attackers often try to access your most common services quickly.
5. Inform and ask for help
If you're using your company computer, notify your IT or cybersecurity team. If it's a personal device, seek expert advice if you detect any anomalies.
Beyond reaction: the importance of prevention
Applying a ClickFix is essential when you've already made the mistake, but the important thing is not to get to that point. Cybersecurity isn't built in a single step, but with continuous monitoring. This is where we can count on solutions like Qondar, by Enthec.
Qondar is designed for individuals who want to keep their exposure to digital threats under control.. It is a Continuous Threat Exposure Management (CTEM) tool that constantly analyzes the data circulating online and determines whether cybercriminals can exploit it. So, instead of reacting when the damage has already been done, you can anticipate and reduce risks.
Think about it: isn't it more relaxing to browse knowing someone is watching over you?
Why is digital exposure a growing problem?
We're constantly connected. From online shopping to banking and communicating with friends and family, everything happens online. That means your digital identity is continuously at stake.
Cybercriminals don't need a sophisticated attack to compromise you. All it takes is:
- A password leaked on a forum.
- An email address exposed in an old database.
- Or a simple click on a malicious link.
In fact, according to a Verizon study (Data Breach Investigations Report 2025), 60% of data breaches are due to some human factor, whether error, breach of trust, or social engineering.
Qondar against malicious links
The advantage of Qondar is that it doesn't wait for you to make a mistake. Its approach is proactive: it continuously monitors your digital footprint and alerts you if your data is at risk.
For example:
- If your email is breached, you'll receive a warning to change your password before attackers can exploit it.
- If your personal information moves in suspicious spaces on the network, Qondar detects it.
- If there is an increase in impersonation attempts linked to your name, the platform will flag it.
This way, even if you fall for a fraudulent link one day, the impact may be much smaller because a continuous surveillance system will protect you.
Practical tips to reduce risks in everyday life
In addition to having a ClickFix plan and monitoring tools like Qondar, there are simple habits you can apply daily to minimize the chances of falling into a malicious link. . They don't require advanced technical knowledge, just a little attention and perseverance.
Learn to identify suspicious links
Always check the URL before clicking. Attackers often use addresses that mimic the real thing by changing a letter or adding a character.
Activate two-step authentication
Even if your credentials are leaked, a second authentication factor can block access.
Keep your devices updated
Many threats take advantage of old vulnerabilities. Installing updates is a simple but very effective measure.
Use strong and unique passwords
Never repeat the same password across multiple services. Password managers are great allies.
A ClickFix is the immediate reaction to stop the damage of a malicious link,. but true peace of mind comes when you combine that reaction with active prevention. And that's where tools like Qondar excel, because they allow anyone to continuously manage their exposure to threats and reduce risks in their daily digital lives.
You might be interested→ 9 healthy digital habits that will protect you from identity theft and leaks.
Take the next step
If you've ever felt unsure of what to do after a suspicious click, it might be time to think about more comprehensive protection.. At Enthec, we work to ensure that both companies, with Kartos, and individuals, with Qondar, can live their digital lives with confidence and security.
Find out how Qondar can help you to stay ahead of cybercriminals and turn your ClickFix into more than just a patch: into a continuous protection strategy.
Zero Trust: What it is and why it's essential for your business
Cybersecurity is no longer something that can be left on the back burner. Today, any organization, large or small, can become a target of an attack.
From data theft to unauthorized access to critical systems, risks are increasingly varied and sophisticated. In this context, the Zero Trust model has established itself as one of the most effective approaches to protecting companies against current and future threats.
Before going into detail, it is worth highlighting that at Enthec, we have been working for years on solutions that help organizations strengthen their digital security. . Kartos, our enterprise cyber surveillance tool, is designed to offer Continuous Threat Exposure Management (CTEM). With Kartos, companies can identify vulnerabilities in real time, analyze risks, and stay ahead of cybercriminals.
What is Zero Trust
The term Zero Trust, also known as "zero trust," refers to a security model based on a straightforward premise: Don't trust anything or anyone by default, regardless of whether they are inside or outside the corporate network.
This means that every user, device, or application that wants to access a system must validate their identity and prove that they have permission to do so; it's not enough to be on the network or have a saved password; each request is evaluated as if it came from a potentially hostile environment.
Basic principles of the Zero-Trust model
- Continuous verification:Initial authentication isn't enough. Each access requires real-time verification.
- Least possible privilege: Users and devices are only given the permissions strictly necessary to perform their task.
- Microsegmentation: Networks and systems are divided into smaller segments, reducing the attack surface.
- Total visibility: Everything that happens on the network must be constantly monitored.
Why is it essential for your company
The importance of Zero Trust is best understood when we analyze how threats have evolved.. Today's cyberattacks are far more sophisticated than they were a decade ago. A perimeter firewall or simply relying on employees to act in good faith is no longer enough.
Adapting to a hybrid and remote environment
Many companies have adopted hybrid or fully remote work models. This means employees connect from personal devices, home networks, or even from public Wi-Fi networks such as those found in coffee shops and airports. The traditional security perimeter has disappeared, blindly trusting that whoever accesses the network is legitimate can be fatal.
The zero-trust approach allows every connection to be evaluated, regardless of where it originates.
Reducing the impact of incidents
According to data from IBM (Cost of a Data Breach Report 2025), the average cost of a data breach exceeds $4.4 million globally. With a Zero Trust model, even if an attacker manages to infiltrate, their ability to move within the network is limited by microsegmentation and least privilege controls.
In other words, the impact of an incident is drastically reduced.
Compliance
Increasingly, cybersecurity regulations and standards, such as the GDPR in Europe and the NIST framework in the United States, recommend implementing Zero-Trust security models to ensure the protection of sensitive data. Adopting them not only helps protect your company but also facilitates legal compliance.
Zero-Trust and CTEM: A Necessary Combination
Zero-Trust is a solid theoretical framework, but to apply it realistically, companies need tools that enable them to maintain continuous visibility and control over their risks, for example, Enthec's Kartos.
Kartos acts as an active cyber surveillance layerconstantly monitoring potential attack vectors. It focuses on Continuous Threat Exposure Management (CTEM), an approach that prioritizes identifying and mitigating vulnerabilities before attackers can exploit them.
By integrating Kartos into their zero-trust strategy, organizations can:
- Detect incorrect configurations that facilitate unauthorized access.
- Monitor the exposure of leaked credentials on the dark web.
- Control vulnerabilities in external suppliers or partners.
- React quickly to any sign of intrusion.
In short, the model of zero-trust gains strength when combined with a system that provides actionable, up-to-date intelligence at all times.

Challenges and benefits of implementing a Zero-Trust model
Adopting a zero-trust security strategy involves a change in mentality and processes.. As with any technological transformation, companies encounter certain obstacles at the outset, but the benefits gained from overcoming them are key to business continuity.
Initial challenges
- Resistance to change: Many IT teams are accustomed to perimeter models and struggle to adapt to tighter control.
- Initial investment: Although it pays off in the long term, implementing a Zero Trust security model requires financial and human resources.
- Technical complexity: Segmenting networks, managing identities, and ensuring multi-factor authentication isn’t always easy.
Clear benefits
- Greater global security: the possibility of internal and external attacks is drastically reduced.
- Granular access control: Each user only accesses what he or she really needs.
- Better incident response: Attackers encounter more barriers and fewer opportunities to move within the system.
- Scalability: adapts to cloud, hybrid, and remote environments without losing efficiency.
Case Studies: How Zero Trust is Applied
The zero trust model is not exclusive to large multinationals or highly regulated sectors. It can be applied in various industries and across different company sizes, with results tailored to the needs of each individual.
Financial sector
Banks and insurance companies handle extremely sensitive information. Implementing zero-trust security ensures that even employees with authorized access are limited in their permissions, thereby reducing the risk of internal fraud.
Healthcare sector
In hospitals and clinics, where medical records are a frequent target of cybercriminals, the Zero-Trust model protects every access to information systems, ensuring that only authorized personnel can consult them.
You might be interested in our publication→ Cybersecurity in Hospitals: How Continuous Monitoring Protects Sensitive Patient Data.
SMEs and startups
It's not just large corporations that should be concerned. Small businesses can also benefit from Zero Trust security, especially when working with external vendors or handling customer data. With solutions like Kartos, implementation is much more accessible.
Digital security cannot be based on blind trust. Zero-Trust is not a fad, but a necessity for any company that wants to protect its data, comply with regulations, and stay ahead of cybercriminals.
Adopting a zero-trust model may seem challenging, but the medium- and long-term benefits far outweigh the initial efforts. And with tools like Kartos by
Enthec, the transition to this approach is significantly easier, providing accurate and real-time information on the organization's exposure.
Don't wait for an incident to occur to strengthen your security. Start building a Zero-Trust-based protection model today and safeguard your business's future.
Do you want to discover how to apply the philosophy of Zero-Trust in your company with the support of Kartos?
Contact Enthec and request a personalized demo.










