Do you know how to protect your user privacy?
Protecting user privacy online is essential for several reasons, from personal security to preserving autonomy and privacy.
When a user browses the Internet and visits various web pages, he leaves a trail of data that can be collected, analyzed, and used in multiple ways, both legitimate and malicious.
Many entities, from companies to governments to hackers, can use Internet user tracking techniques. These techniques allow data collection about users’ online activity, providing valuable information for various purposes.
Collecting private information can be dangerous if that data is not protected. This vulnerable data can be stolen by cybercriminals and published through Deep Web leaks.
By using Internet services, the user is aware that legal entities use tracking methods in which they actively or passively collect personal information. And he trusts that third parties should not use this information, exposing threats to his privacy.
Therefore, the user’s general tendency when using technologies is to accept tracking and not worry beyond about his private information.
Why it is important to protect your user privacy
Protecting privacy is essential to guarantee users’ security, freedom, and autonomy in the digital environment.
- Personal security: Personal information shared online, such as names, addresses, phone numbers, and financial data, can be exploited by cybercriminals to commit fraud, identity theft, or harassment.
- Protection of sensitive data: Some websites collect sensitive data about health, political opinions, and sexual orientation, among others. The exposure of this data can lead to discrimination, manipulation, or even persecution in some cases.
- Preservation of privacy: Online privacy is essential to keep certain aspects of private life out of the reach of the general public. Everyone has the right to keep certain aspects of their life out of the gaze of others.
- Avoid excessive personalization: If browsing data is used to create detailed user profiles, this can lead to extreme personalization that limits the diversity of information and opinions to which an individual is exposed.
- Autonomy and freedom: Protecting privacy online is essential to maintain the autonomy and freedom of expression Self-censorship can occur if people feel they are being watched or judged for online activities.
Monitoring techniques
Entities use these techniques to profile users’ habits, tastes, and other details.
- Cookies: Text files that store information sent by the web service in the user’s browser.
- Privacy policies: When the online service stores and manages confidential data, it must indicate to the user how this information will be used.
- HTML5 Elements: Storage mechanism, also known as “Client-Site-storage,” with more storage capacity than cookies.
- IP address and geolocation: When a user browses the Internet, the service provider automatically assigns the IP address used. An online service may use This IP address to identify your city of residence.
- Social networks: All social networks such as X, Facebook, or Instagram take the information provided by users and share it with third parties
- Google Services: Google has several services that monitor and record each of the activities carried out by its users.
Tools to protect your user privacy
The following are some of the most commonly used online tools and services to prevent the leaking of personal information.
Search Engines
There are alternative search engines where there is no vulnerability to privacy when making queries and do so confidentially and anonymously:
- Ixquick: A search engine that does not log the IP address, does not correlate with its visitors and search criteria, and does not use tracking cookies.
- Startpage: A search engine based on Ixquick with the characteristic that it can function as a proxy server between the user and the Google search engine. The results will be the same as those returned by Google, but without collecting information about the user performing the searches.
- DuckDuckgo: It does not record the user’s personal information or search criteria, nor does it allow you to send information about the user or their search criteria visit. It also does not allow sending information about the user to the sites he visits.
Privacy settings in browsers
- Firefox: The privacy settings section called “Tracking” contains the option to indicate options to avoid tracking.
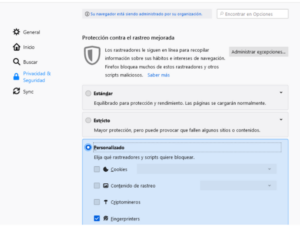
- Opera: It is possible to apply configuration options that allow the management of cookies, SSL certificates, and passwords.
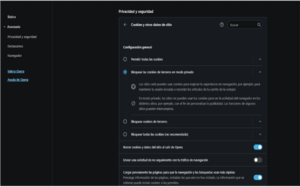
- Chromium: In the same way as Opera and Firefox, it is possible to manage various privacy details of cookie management.
- VPN: VPN is a technology that allows you to create private connections between two points using a public network such as the Internet. The benefit of VPNs is to hide the user’s IP and be able to access Internet sites that are blocked in the country from which the request is made. The VPN service is responsible for routing the request to the website using an IP address that belongs to a different country
Anonymous proxy servers
A proxy server is a middleware solution that works by routing requests and responses transparently between the two.
It allows hiding the client’s IP since the destination will only see the proxy’s IP address.
There are several lists of anonymous proxy servers that allow IP hiding:
- Zend2 Proxy: https://zend2.com/
- DontfilterUs: http://donfilter.us/
- Proxify: https://proxify.com/
- Kproxy: http://kproxy.com/
Other tools to protect your user privacy
In addition to these, there are other interesting techniques and tools to protect against tracking:
- HTTPS Everywhere Extension: Extension developed by the Tor Project and the EFF team, with the main goal of capturing requests made with the HTTP protocol against a list of sites and overriding the requests to use HTTPS.
- Web browser plugins: Extensions that allow you to clean the information stored in the browser easily, like Click and Clean.
- Privacy Badger: Plugin developed by EFF that allows you to block trackers like Ghostery but also will enable you to stop “Ads.”
Thus, many entities use Internet user tracking techniques for commercial, security, or malicious purposes. Therefore, as an exercise of personal responsibility and to avoid significant problems, users must be aware of these practices and take steps to protect their privacy online.
