How to detect vulnerabilities in Active Directory before they are exploited
Active Directory has been the heart of IT infrastructure in thousands of organizations for years. Regardless of company size or industry, if there's a Windows domain, there's an Active Directory managing identities, access, and permissions.
That's precisely why it has become a favorite target for attackers. Not because it's inherently weak, but because it's often to grow, change, and be inherited over time... and that's where the cracks appear.
Detecting vulnerabilities in Active Directory before they are exploited is not a one-off task, nor is it something that can be resolved with an annual audit. It's an ongoing process that combines technical knowledge, real-world visibility, and risk context. In this article, we'll see how to do it in practice, without unnecessary technical jargon, and what role the Continuous Threat Exposure Management (CTEM) solutions play in this process.
At Enthec, we work precisely on this continuous approach. Kartos, our cybersecurity solution for businesses, helps identify, prioritize, and reduce exposure to real threats, including risks associated with Active Directory. It's not just about seeing vulnerabilities, but about understanding which ones truly matter and why.
If you want to know how this translates into the day-to-day work of a security team, keep reading.
Why does Active Directory remain a critical security point?
Active Directory is not just an authentication service. It's a complete ecosystem where users, computers, servers, group policies, services, and trust relationships coexist. A small error in your configuration can have a considerable impact.
Furthermore, attackers no longer improvise. In many recent incidents, the primary objective is not to encrypt data or exfiltrate information, but to take control of Active Directory.. Once inside, everything else falls into place.

Common vulnerabilities in Active Directory
Excessive permissions and poorly managed groups
One of the most frequent problems is the accumulation of privileges. . Users who change positions, service accounts created "temporarily," or groups that no one has reviewed for years.
A user with more permissions than necessary is an open door,. and in Active Directory, those doors are usually well hidden.
Outdated accounts and weak credentials
Accounts that shouldn't exist anymore, passwords that aren't rotated, or services that work with shared credentials. All of this is still commonplace. The use of compromised credentials remains a leading cause of security breaches, especially in corporate environments.
You may be interested in→ How to manage business passwords and credentials easily and securely to avoid online threats.
Poorly configured group policies
Group Policy Objects (GPOs) are powerful, but also delicate. A poorly implemented policy can disable security controls on hundreds of computers without anyone noticing. The problem here is usually not a lack of controls, but rather a lack of visibility into its real impact.
How to proactively detect vulnerabilities in Active Directory
1. Technical audits… but with continuity
The classic cybersecurity audits are helpful, but they have a clear limit: the photo becomes outdated very quickly.. Active Directory changes every week, sometimes every day. It's recommended to move from one-off audits to continuous review processes that analyze changes in real time.
2. Analysis of attack routes
Not all vulnerabilities carry the same weight. Some are only a problem when combined with others. That's why it's crucial to analyze real attack vectors, not just bug lists. This approach allows us to answer a much more helpful question:
"If an attacker logs in with this user account, how far could they go?"
3. Correlation with real threats
This is where Active Directory security often fails. Insecure configurations are detected, but they are not linked to
active threats or to techniques currently used by attackers.
CTEM methodologies focus precisely on that: on actual exposure, not on theoretical risk.
The role of cyber surveillance in Active Directory security
Traditional scanning tools often generate lengthy reports that are difficult to prioritize. The result is predictable: urgent issues are addressed, while the rest remain unresolved.
Cybersurveillance applied to Active Directory aims to detect early signs of exposure, even before it becomes an incident.
Kartos as support in continuous risk management
Kartos, our CTEM solution for businesses, is designed to identify attack surfaces, assess their impact, and prioritize actions.. In the case of Active Directory, this translates to:
- Continuous visibility over critical configurations.
- Detection of changes that increase exposure.
- Context to identify which vulnerabilities are truly exploitable.
It's not just a technical issue but also a strategic one: helping teams decide where to invest time and resources.
Indicators that your Active Directory needs urgent attention
Frequent changes without precise control
If no one is clear on who modifies what in Active Directory, it's a red flag. Changes without traceability often lead to accumulated errors.
Recurring minor incidents
Account lockouts, unauthorized access, or recurring alerts can be symptoms of a deeper structural problem.
Excessive dependence on privileged accounts
When too many processes depend on high-privilege accounts, the risk multiplies.
Reducing that dependency is key to improving Active Directory security.
Good practices for reducing exposure to threats
Among the best practices for reducing exposure to threats, we highlight:
Periodic review of privileges
It's not a pleasant task, but it works. Reviewing who has access to what and why drastically reduces the chances of abuse.
Segmentation and the principle of least privilege
Applying the principle of least privilege is not just a theoretical recommendation. It is one of the most effective measures to limit the impact of an attack.
Continuous monitoring with a CTEM approach
This is where many organizations are moving from reacting to anticipating, relying on solutions that provide continuous visibility and intelligent prioritization.
Active Directory as part of a broader security strategy
A common mistake is treating Active Directory as an isolated element. In reality, it's connected to email, applications, VPNs, cloud environments, and external services.
Therefore, Active Directory security must be integrated into a global strategy that accounts for the organization's entire attack surface.
In this context, tools like Kartos enable a unified view that links internal vulnerabilities to external threats and suspicious online activity. Detecting vulnerabilities in Active Directory before they are exploited is not a matter of luck or simply checking off a list. It's a matter of focus, visibility, and continuity.
If you want to know how Kartos can help you identify and reduce your Active Directory's actual exposure, at Enthec, we would be happy to analyze your case and show you how to apply a CTEM approach adapted to your environment.
Contact our team and start seeing your Active Directory from an attacker's perspective, before someone else does.
What is a ransomware attack, and how to anticipate it with advanced monitoring
Most organizations and, increasingly, individuals have heard of ransomware attacks. Still, few people really know what it entails, how it originates, and, above all, how to anticipate it before it causes real harm.
In recent years, incidents of this kind have become much more sophisticated and insidious. They don't usually begin with an alarming on-screen message, but with subtle signs that go unnoticed until it's too late.
Before we get into the subject, it is worth remembering that traditional prevention is no longer an option, especially as automated attacks proliferate and cybercriminals exploit any oversight.
For individual users, Enthec offers Qondar, a customized cyber-monitoring tool that detects early warning signs, data leaks, and suspicious activity that may indicate an attack on your digital identity.. It's a continuous service that alerts you when something requires your attention, preventing a minor incident from escalating into a serious security breach.
If you are an individual and want to know whether your information is circulating where it shouldn't be, Qondar can help you start today.
What exactly is a ransomware attack?
A ransomware attack is a type of cyberattack in which malware encrypts system files or locks the victim's device, demanding a ransom for their release.. The worrying aspect is that it's not just about "kidnapping" data; many current variants also steal data before encrypting it and threaten to leak it if the ransom isn't paid publicly.

Most common types of ransomware
There are several types of ransomware, and knowing them helps to understand the risk better:
- Encrypting ransomware:. It is the most common. It encrypts documents, databases, or backups, rendering daily operations unusable.
- Locking ransomware:. Prevents access to the entire operating system. It usually affects individual users more.
- Double extortion:. First, they steal the data, then they encrypt it. This model has grown significantly since 2021.
- Targeted ransomware:. Attackers select a specific company, study it, and orchestrate a manual attack that has been prepared over weeks.
- Ransomware-as-a-Service (RaaS):. Anyone without technical expertise can rent a "kit" to launch attacks. This model has multiplied incidents worldwide.
Ransomware symptoms that can warn you before disaster strikes
Many attacks take days to activate. During that time, systems may show signs that, if detected early, enable action before severe damage occurs. Among the most common ransomware symptoms are:
- Teams are slower than usual for no apparent reason.
- Programs that close automatically or stop responding.
- Appearance of new background processes that you do not recognize.
- Changes to system files or folder permissions.
- Unusual login alerts on online platforms.
- Notifications of failed login attempts to your accounts.
In organizations where systems are adequately monitored, these behaviors should trigger early warnings. For individual users, detecting these signals is more challenging, and automated tools like Qondar are handy.
Ransomware: what to do if we suspect we are being attacked
There is no magic formula, but there is a series of recommended steps to take when you think you are having an attack:
- Disconnect the affected device:. Disconnect the affected device: It prevents malware from spreading to other connected computers or services.
- Never pay the ransom:. INCIBE and Europol agree that the payment could worsen the situation. It does not guarantee recovery and fuels the criminal industry.
- Review the backups:. If they are recent and isolated, they can save all the information.
- Record all possible information:. Screenshots, messages, file names, or any other trace that helps identify the variant.
- Contact professionals:. Specialized support can stop the attack, recover data, and manage internal and external communication.
Recent ransomware examples that show its real impact
Analyzing real-world incidents shows that no sector is safe. Some recent cases include:
- An attack on several London hospitals in 2024, in which medical records were encrypted, and there were threats to publish sensitive patient information.
- Education sector, with universities paralyzed for weeks as internal management platforms were encrypted.
- SMEs from different countries were attacked via RaaS and forced to halt basic operations, such as logistics and customer service.
These ransomware examples demonstrate that the target is not always a large corporation; attackers look for any vulnerability, no matter how small.
Why advanced monitoring is key to anticipating problems
This point is where the modern approach to Continuous Threat Exposure Management (CTEM) comes in. . It is a process in which weaknesses, suspicious movements, external leaks, and any data that may indicate an imminent risk are constantly analyzed.
How CTEM helps against a ransomware attack
- Identifies credential leaks before they are used.
- Monitors domains, the deep web, and external sources for dangerous mentions.
- Controls vulnerabilities publicly exposed.
- Detects anomalous behavior indicative of early-stage infection.
- Reduces the time between detection and response.
Within the Enthec ecosystem, this approach materializes in two solutions:
Kartos, for companies
A cyber surveillance platform designed for organizations that need to monitor their attack surface 24/7. It allows them to detect threats before they become incidents.
Qondar, for private users
The ideal tool for those who don't have a technical team but still want to know whether their data is at risk. Qondar continuously analyzes whether your information appears in suspicious contexts, whether your credentials are being circulated, or whether someone is impersonating you.
This is precisely why it is beneficial to anticipate a ransomware attack targeting the end user, since many campaigns begin with prior espionage or password theft.
How to realistically anticipate a ransomware attack
Anticipation doesn't depend on a sophisticated trick, but on a combination of sensible measures:
- Review passwords and always enable two-factor authentication;. many incidents begin with stolen credentials via leaks or phishing.
- Keep systems updated:. Although it may seem basic, it remains one of the most exploited weaknesses.
- Monitor digital identity:. If your data appears to have been leaked, you are likely to be targeted for future attacks.
- Keep backups offline:. Copies linked to the system are encrypted in the same way as the primary data.
- Train the staff:. It's essential in companies. An employee who recognizes a suspicious email can prevent a disaster.
Ransomware has become one of the biggest digital threats of our time. Understanding what it is, knowing its variants, and learning to identify early warning signs gives us a better chance of protecting ourselves.
And if you're an individual, remember that you don't have to do it alone. With Qondar, you can let advanced monitoring do the work for you, alerting you when it detects any signs of risk. Protecting your identity is easier when you have tools designed for it.
Do you want to know if your data is exposed? Discover Qondar and start monitoring your digital security today.
Why operational technology needs a proactive cybersecurity strategy
Industrial digitization is advancing faster than many imagine. What was once a largely isolated environment (production lines, machines, control systems, etc.) is now connected and therefore exposed.
We're talking about operational technology, or OT, an area where security can no longer be treated as an optional add-on, but as a critical part of the daily operation of any company.
Some tools stand out, such as Kartos, which provides organizations with a clear, up-to-date, and prioritized view of the cybersecurity risks affecting them. It doesn't just identify vulnerabilities; it helps assess the company's actual exposure, where the risk lies, and how to reduce it before it is exploited.
Operational technology: an industrial environment that is no longer isolated
For decades, operational technology networks operated separately from traditional computer systems. This isolation was, in itself, a layer of security. However, the need to improve efficiency, share data, and remotely control processes has led OT systems to be interconnected with IT networks and cloud services.
What does this mean in everyday life?
IT/OT convergence offers clear advantages: continuous monitoring, predictive maintenance, energy savings, and reduced downtime. But it introduces a new scenario:
-
- More entry points for external threats.
- Industrial equipment that was not designed with cybersecurity in mind.
- Complicated updates that are delayed for fear of halting production.
- Dependence on external providers whose own vulnerabilities can affect the company.
In this scenario, relying on traditional controls or one-off reviews is no longer enough. The exposure changes weekly, sometimes daily.
You might be interested in> IoT and cybersecurity: Risks and strategies to protect connected devices.
Main risks affecting operational technology OT today
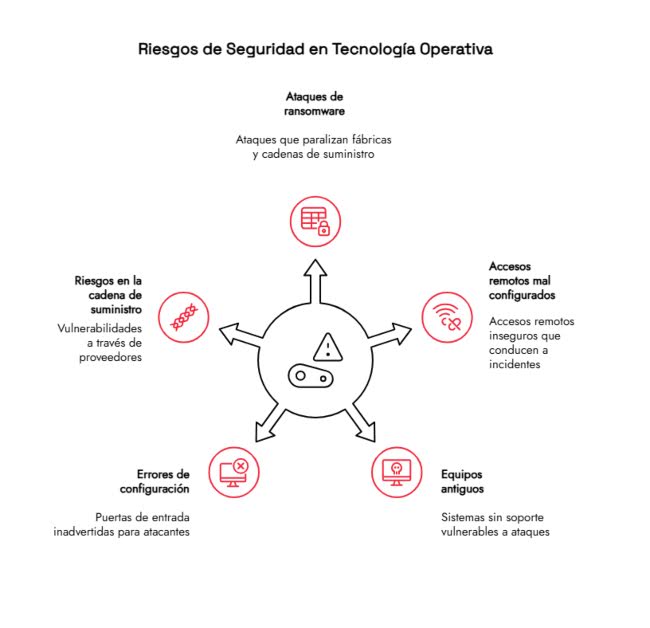
Operational technology (OT) faces very different risks than those typically found in office computer systems. Here are some of the most common:
1. Ransomware in industrial environments
Ransomware attacks are no longer solely focused on stealing or encrypting data. They also aim to paralyze entire factories, disrupt supply chains, or compromise critical equipment.
2. Misconfigured remote access
Remote access is proper, yes, but it's often enabled hastily, with weak passwords, or without adequate controls. This is one of the vectors that causes the most incidents in OT environments.
3. Older equipment without support
Many industrial machines are decades old. They're still working, but they no longer receive security patches. When connected to the network, they become easy targets.
4. Configuration errors
Even a small, unmonitored open port can serve as a gateway for attackers.
5. Risks in the supply chain
Suppliers are also part of the OT ecosystem. A security breach in their network can ultimately affect the company as a whole.
All these factors make it clear that a specific protection strategy is needed for operational technology.
Why proactive cybersecurity is essential in OT
The philosophy of proactive cybersecurity is based on anticipating risks.. It is not enough to react when something goes wrong; we must identify threats before they create a real problem.
1. Operational technology cannot stop
In IT, a failure can lead to data loss or work interruptions. Serious, of course, but manageable. In OT, a failure can halt a production line, generate millions in losses, endanger workers, or affect critical services.
That's why OT security should aim to prevent incidents from their origin.
2. Threats are constantly evolving
The attackers already know the weaknesses in the operational technology. They are looking for old faults, careless configurations, or forgotten access.
. An annual review or a static analysis is not enough to keep up with them.
3. The exposure changes, although the infrastructure does not.
Even if the company does not install new machines, its exposure may vary due to:
- New connections.
- Changes in suppliers.
- Software updates.
- Human errors.
- Newly discovered vulnerabilities.
Supervision must be continuous.
What does a CTEM approach bring to operational technology environments?
The Continuous Threat Exposure Management (CTEM) is a framework that has gained traction in recent years. It enables organizations to, on an ongoing basis, understand the risks they face, their potential impact, and the actions to prioritize.
How CTEM is applied to OT operational technology
A well-implemented CTEM strategy in OT helps to:
- Identify exposed assets, including those the company may have forgotten.
- Detect insecure configurations.
- Control how the attack surface changes.
- Prioritize risks based on actual impact, not assumptions.
- Guiding teams towards faster and more informed decisions.
This is where solutions like Kartos stand out for their comprehensive approach and their ability to continuously monitor exposure without interrupting industrial operations.
Kartos: a realistic and helpful solution for protecting operational technology
Unlike other tools that focus on vulnerability detection, Kartos helps visualize the actual exposure of each asset, supplier, and process connected to the network.
Advantages of using Kartos in an OT environment
- Provides a clear, prioritized view of the attack surface.
- Identifies risks in external providers.
- Facilitates quick decision-making.
- Reduces the likelihood of incidents that affect production.
- Provides context: it not only shows vulnerabilities, but also their potential impact.
For companies with complex OT environments, this is critical. Knowing what might fail before it does is a matter of money and safety.
Proactive cybersecurity best practices in operational technology
To strengthen an OT environment, these measures are especially recommended:
1. Complete and up-to-date inventory
You can't protect what you don't know. A living inventory, not a static document, is essential.
2. Network Segmentation
Properly separating IT and OT environments limits lateral movement in the event of an intrusion.
3. Continuous monitoring
OT systems require constant monitoring to detect unexpected changes.
4. Strict access control
You have accounts with minimal privileges and remote access protected by multiple factors.
5. Constant review of the supply chain
Every vendor is a potential point of attack. The good news is that many of these measures can be automated or better managed with CTEM tools like Kartos.
Anticipating is the only viable strategy
Digital transformation is already a reality in the industrial sector. Operational technology is more connected than ever, and that brings enormous benefits… but also obvious risks. In this environment, reactive cybersecurity falls short. Companies need approaches that are up to today's challenges: continuous, intelligent, and aligned with real impact.
Solutions like Kartos help organizations understand and manage their exposure without slowing operations. That's the key: protect without stopping, anticipate without alarm, monitor without interrupting.
If your company works with operational technology and wants to understand its actual exposure to threats, start today with continuous, proactive analysis.. Discover how Kartos can help you protect your industrial environment before risks become problems.
How automation in cybersecurity helps reduce human error in online protection
Cybersecurity has been evolving for years at a pace that is sometimes difficult to keep up with. Threats change, attack methods become more subtle, and the amount of information we manage continues to grow.
Amid this scenario, one factor remains decisive: the human error,. not out of ill intent, but because we humans can't be aware of everything, all the time. Fortunately, cybersecurity automation has become an ally that helps us strengthen protection without adding complexity to daily life.
Before delving into the subject, it's worth pausing to consider a tool that perfectly encapsulates this evolution. We're discussing Qondar, Enthec's solution designed for individuals who want to manage their exposure to digital risks.. Its practical, visual, and continuous approach reveals where the sector is heading: constant monitoring, clear warnings, and the ability to make informed decisions without needing a master's degree in cybersecurity.
In short, Qondar shows how automation can be close, practical, and, above all, accessible.
Why human error remains one of the most significant security breaches
Most security incidents are not due to complex failures in highly advanced systems, but to everyday actions such as opening a suspicious email, reusing passwords, or downloading a file without thinking.
This makes sense; whoever attacks finds the easiest way to access a system,and we humans are often that weak point. While training is essential, relying solely on human attention isn't sufficient, especially in environments where we receive hundreds of notifications, messages, and tasks vying for our attention.
This is where cybersecurity automation becomes essential. It's not about replacing anyone, but about minimizing unavoidable oversights by delegating repetitive tasks, from surveillance and analysis to systems that do not get tired, do not get distracted, and do not forget.
How automation strengthens online protection
Automated cybersecurity is not an abstract or futuristic concept. It's already being implemented in companies large and small, and increasingly in solutions for individual users.. Here are some of the areas where it has the most significant impact:
1. Continuous, uninterrupted monitoring
An automated system can monitor in the background 24/7, detect unusual patterns, and provide instant alerts. This type of monitoring would be impossible if it depended solely on a person. Furthermore, it allows for anticipating attacks before they fully materialize.
At this point, automation in cybersecurity acts as a radar that never turns off.
2. Reduction of repetitive and error-prone tasks
Checking links, validating emails, verifying configurations, comparing databases… These are necessary tasks, but they are also precisely the type of processes where errors can occur due to fatigue or simple saturation.
Automating them is doubly beneficial:
- Time is gained.
- It prevents an oversight from turning into a bigger problem.
3. Incident classification and prioritization
One common problem is the number of alerts generated each day. Without automation, many go unnoticed or are addressed late. With advanced tools, incidents are ordered by severity, allowing us to react sooner where it really matters.
4. Updates and patches without manual intervention
An essential part of security is keeping everything up to date.. Automation saves headaches here, too. A self-updating system reduces risks without requiring additional time.

CTEM: the new approach that unites surveillance and automation
In recent years, the concept of CTEM (Continuous Threat Exposure Management) has gained traction.. It is not a fad or an empty word; it is a methodology that combines continuous evaluation, risk prioritization, external and internal visibility, and agile response.
Essentially, CTEM applies automation in cybersecurity to keep under control what can be compromised, how, and with what level of urgency.
Enthec's solutions, Kartos, focused on businesses, and Qondar,designed for individuals, are a clear example of this philosophy. Both monitor in real time, detect leaks or exposures, and display information clearly so that each person can make decisions based on real, up-to-date data.
The importance of automating personal cyber surveillance
When we think about digital threats, we usually picture companies, large organizations, or critical infrastructure. However, individual users are increasingly becoming targets, not because we hold big secrets, but because we accumulate data, access credentials, and accounts that attackers can exploit.
What kind of risks do we avoid with automation?
- Password leaks in external services.
- Appearance of personal data in leaks.
- Identity theft on social networks.
- Suspicious access from unusual locations.
- Involuntary disclosure of private information.
Qondar automates this surveillance and provides clear, understandable notices for everyone. . You don't need to be a cybersecurity expert to recognize the risk and take action.
You may be interested in→ 9 healthy digital habits that will protect you from identity theft and leaks.
Automation doesn't mean disengagement; instead, it means making better decisions.
It's important to clarify that automating security doesn't mean "putting everything on autopilot," but rather ensuring that essential alerts don't go unnoticed,. while maintaining a balance between technology and human judgment.
The ideal combination is:
- Automation for monitoring, classifying, and alerting.
- The person to make the final decision.
This alleviates the mental burden and enables stronger protection without requiring additional time.
Real advantages of automation in cybersecurity for businesses and individuals
Although the contexts are different, both companies and individual users can benefit from a user-based approach to automation in cybersecurity:
For companies
- Fewer errors resulting from manual processes.
- Greater visibility over the attack surface.
- Early detection of exposures in equipment, employees, or suppliers.
- Optimization of IT department resources.
For individuals
- Absolute control over one's digital footprint.
- Clear, actionable alerts without technical jargon.
- Continuous security without relying on remembering to check.
- Ongoing updates to address new threats.
Automation is about better protection, not more complexity.
Automation does not replace human care, but it does add a layer of precision and consistency that is hard to match.. In an environment where cybercriminals automate their attacks, it is logical to respond with tools that can monitor at the same scale.
If you genuinely want to understand your digital exposure, receive early warnings, and improve your personal security without complications, Qondar by Enthec is a good starting point. If your company needs more comprehensive oversight, Kartos offers a level of depth designed for organizations.
Start protecting your online identity today.
Try Qondar and discover how cybersecurity automation can give you continuous, precise monitoring tailored to your daily life.. Your digital peace of mind starts with a click.
Managed Security Services (MSS): Features and Benefits
Cybersecurity has become a critical aspect for any organization. Threats evolve rapidly, attackers automate processes, and attack surfaces expand as companies incorporate new systems and tools.
In this context, MSS (managed security services) have become established as an effective option to strengthen digital protection without requiring companies to maintain internal resources that are difficult to sustain.
Before delving into what MSS contributes and why it's so prevalent in modern security strategies, it's worth taking a look at a tool that perfectly complements this model: Kartos, the solution from Enthec designed for companies that need a constant and realistic visibility of your external exposure. . This tool is part of the CTEM philosophy, an approach that continuously analyzes the attack surface, identifies real risks, and enables prioritizing efforts.
At a time when most incidents are triggered by known vulnerabilities or misconfigurations, having this view is crucial for any security strategy, including those based on MSS.
What precisely are Managed Security Services (MSS)?
The MSS are outsourced services offered by specialized providers to continuously monitor, manage, and improve an organization's security.. Although each provider may have its own catalog, the essence is the same: to provide expert knowledge, advanced tools, and constant follow-up.
An approach that frees up internal burden
Many companies don't have dedicated cybersecurity staff, or if they do, they're focused on day-to-day operational tasks. Internal teams are often left out overflowing for tasks such as:
- Analyze alerts that keep growing.
- Review security settings on various systems.
- Prioritize vulnerabilities that change every week.
- Keep an eye on emerging threats.
MSS allows some or all of these tasks to be delegated to specialists who work with technology, processes, and equipment dedicated exclusively to this.

Main features of MSS
Although each model is tailored to specific needs, most managed security services share a standard set of functionalities.
Continuous monitoring
It is one of the central components. MSS providers constantly monitor infrastructure, networks, and services to detect suspicious behavior, failures, or signs of intrusion.
Incident Management
When an attack attempt is detected, the provider not only generates alerts but also assists with analysis, containment, and recovery. Having processes defined and executed by professionals reduces damage, downtime, and financial losses.
Vulnerability Management
MSS typically include periodic scans, configuration reviews, and patch prioritization. However, this is where solutions like Kartos become essential, because they complement this internal view with an external X-ray that reflects what an attacker would see from the outside.
If you want to delve deeper into this topic, visit our blog→ Real-time vulnerability management: a step forward in cybersecurity.
Threat analysis and context
A Security Management System (SMS) doesn't just review logs: it interprets what's happening in the security world. For example, if a critical vulnerability is actively exploited, the provider helps the client assess whether their infrastructure is exposed and what measures they should take.
Periodic reports and advice
Those in charge typically receive accessible analyses that allow them to understand the evolution of risk, the level of exposure, and the impact of the measures taken. This transparency facilitates strategic decision-making.
The value of combining MSS with a CTEM approach
The traditional security model focused on protecting what was already within the perimeter. However, today that perimeter has become blurred: there are cloud services, external applications, remote access, personal devices, databases exposed in error, and a long list of constantly changing threat vectors.
This is where the CTEM and MSS complement each other naturally.
Internal visibility + external visibility
- The MSS review logs, devices, networks, and internal activity.
- Tools such as Kartos analyze what is exposed externally: domains, subdomains, leaks, unknown assets, third-party risks, and poorly published configurations.
By combining both perspectives, the company obtains a more complete and realistic map of its situation.
Prioritization based on actual risk
Many companies have hundreds or even thousands of vulnerabilities detected by their internal systems. The CTEM simplifies this landscape by highlighting what is truly urgent. If something can be exploited from the outside or appears on cybercrime forums, it moves to the top of the list.
Reduction of “noise” in MSS
A managed SOC receives thousands of alerts every week. When the provider leverages a CTEM platform, it eliminates noise and focuses on relevant threats. This results in more effective defense and faster response times.
Benefits of MSS for organizations
The Managed Security Services have become a key solution for businesses of all types. Their most valued advantages are usually:
1. Controlled and predictable costs
Hire cybersecurity specialists is complex and expensive; keeping them trained is even more so. MSSs allow access to complete teams at a known monthly or annual cost.
2. Greater security maturity without increasing staff
Especially useful for SMEs and companies that cannot (or do not want to) create an internal team.
3. Rapid incident response
Response time is critical. MSS drastically reduces the hours (or days) that an internal team would spend detecting a problem on its own.
4. Regulatory compliance
Many standards, such as the ENS or the NIS2,require continuous monitoring and risk management. An MSS service facilitates compliance with these requirements through appropriate documentation and processes.
5. Tranquility
Perhaps the least technical benefit, but the one most valued by management. Knowing that experts are monitoring the infrastructure 24/7 provides security and prevents improvised decisions.
Kartos and the MSS: a strategic combination
Companies across all sectors use Kartos to strengthen their security processes, and many integrate it directly into their MSS strategy. At Enthec, we've observed that this combination enables:
- Reduce actual exposure to attacks.
- Optimize response times.
- Improve coordination with internal or external security teams.
- Avoid breaches caused by unknown or misconfigured assets.
Furthermore, Kartos provides clear, practical reports that facilitate the work of both the MSS provider and the client. This alignment between internal and external capabilities is, today, one of the cornerstones of effective security.
MSS have become established because they help organizations protect themselves in an increasingly complex environment.. However, monitoring is not enough: it is necessary to understand the exposure, prioritize what really matters, and act continuously.
That's where the combination of managed services and solutions like Kartos, based on CTEM, comes in to elevate security to a more practical, intelligent level, adapted to current reality.
If your company wants to strengthen its security strategy, improve its external visibility, and have a modern, comprehensive, and sustainable approach, we invite you to learn how Enthec can help you achieve this. Contact us.
Cybersecurity and the human factor: the most common mistake in digital protection
Cybersecurity is one of those issues we all know we should be taking care of, but we keep putting it off. Updating passwords, checking permissions, verifying links… These are simple tasks, yes, but they're often overlooked. And that's precisely the root of the problem: In cybersecurity, the human factor remains the weakest link.
This isn't about blaming anyone, but about acknowledging an apparent reality. Human error is, currently, the most common cause of digital incidents.
In recent years, the rise of remote work, the fast pace of life, and the daily use of connected devices have made this vulnerability even more pronounced. And if we think about it for a moment, it makes sense: an impulsive click or a weak password can open the door to problems that cost time, money, and reputation.
Before moving on, it's worth introducing a tool that's helping to reduce this exposure in the daily lives of all users: Qondar, Enthec's cyber-surveillance solution for individuals. Qondar is a key component of Continuous Threat Exposure Management, providing timely warnings about data breaches, password leaks, and other risks that directly affect a person's digital life.
Understanding the relationship between cybersecurity and the human factor
The expression “cybersecurity and the human factor” encompasses a straightforward idea: Digital security does not depend solely on systems, firewalls, or artificial intelligence,but also on how we use technology. Companies can invest in advanced tools, but they're of little use if an employee falls for a phishing email or unintentionally shares sensitive information.
Why do we keep failing at the same things?
Several reasons explain this phenomenon:
- Information overload. We live surrounded by notifications and simultaneous tasks. In that pace, double-checking a suspicious email isn't always a priority.
- Overconfidence. In both our professional and personal lives, we often think, "It won't happen to us." But no one is safe: neither individuals nor companies.
- Lack of ongoing training. Many attacks evolve so rapidly that what we knew a year ago is no longer sufficient. And this is where the CTEM concept comes into play.

The importance of Continuous Threat Exposure Management (CTEM)
Cybersecurity can no longer be viewed as a one-off project. It's not enough to conduct a single audit and assume everything is under control. Threats evolve. Data moves. And attackers refine their techniques.
Continuous Threat Exposure Management (CTEM) seeks precisely this: to constantly monitor which vulnerabilities we have and which risks are active at any given time. . It's not just about reacting, but about detecting before the damage occurs.
What does CTEM contribute to the field of human factors?
- Constant visibility: allows you to see if leaked credentials, breaches, or risk signals associated with common errors have appeared.
- Realistic prioritization: It helps determine which vulnerabilities require immediate attention and which do not.
- Data-based prevention: The sooner a problem is identified, the easier it is to correct.
This is where solutions like Kartos (for businesses) and Qondar (for individuals) play an instrumental role. Both allow this continuous exposure approach to be implemented without complex processes or specialized equipment.
Most frequent human errors in cybersecurity
Below are some of the most common mistakes in both the business and personal spheres. All of them are directly related to cybersecurity and the human factor, and many could be avoided with minimal monitoring or training.
1. Reusing passwords
A classic. According to a NordPass study, most users still reuse the same password across more than 10 different services. If one of those platforms suffers a data breach, they are all exposed.
You may be interested in→ How to manage business passwords and credentials easily and securely to avoid online threats.
2. Falling for fraudulent emails or messages
Phishing is becoming increasingly sophisticated. Many attacks perfectly mimic well-known companies, banks, or even coworkers. An innocent click can compromise the entire device.
3. Underestimating “harmless” information
Sometimes we share seemingly irrelevant data: a photo with location, a personal email on a website without HTTPS, an automatic response on vacation… All of that can be useful to an attacker.
4. Trusting open Wi-Fi networks
Having a coffee while we work is tempting, but connecting to an open network can expose sensitive information to third parties.
5. Failure to monitor personal data leaks
Many users are unaware whether their credentials have been exposed on forums, in leaked databases, or on the dark web. This lack of control fuels risks that accumulate without us even realizing it.
How to reduce human vulnerability: habits and tools
The good news is that improving cybersecurity and the human factor doesn't require being an engineer or dedicating hours every week. Often, simple measures are enough.
Basic digital hygiene
- Use unique and strong passwords.
- Activate two-step verification.
- Be wary of unsolicited links or files.
- Review application permissions.
- Keep systems updated.
Continuing education in companies
It's not just about giving an annual talk. Organizations that reduce incidents typically implement short, dynamic, and frequent training sessions. Even small reminders have a real impact.
Cyber surveillance for individuals
This is where Qondar comes in, designed so that anyone can:
- Find out if passwords have been leaked.
- Detect digital identity theft.
- Monitor mentions or data in high-risk areas.
- Receive clear and actionable notifications.
It's a simple way to effortlessly integrate the CTEM mindset into your daily routine, helping to make the human factor no longer a permanent problem.
Technology helps, but the responsibility is shared.
Although tools like Kartos or Qondar facilitate risk management, cybersecurity remains a shared responsibility. The sum of human behavior and technological surveillance is what truly builds a safe environment.
The key is to create a culture where asking questions, checking, and being skeptical are the norm, not the exception, where it's understood that a mistake isn't a personal failing, but a reminder that we are all vulnerable.
The relationship between cybersecurity and the human factor is undeniable. As long as distractions, overconfidence, and a lack of healthy digital habitsexist, incidents that could have been avoided will continue to occur. That's why it's so important to integrate continuous monitoring at both the company and individual levels.
If you want to improve your personal protection,whether it's your own data or that of your close circle, Qondar is an accessible, practical option that lets you see what's happening with your data in real time. Discover our tool and start controlling your digital exposure today. More conscious cybersecurity is just a step away.
The relevance of cybersecurity audits in companies
Any company, even the smallest ones, operates in some way connected to the online world and depends on data, devices, and applications. The reality is simple: if your business uses the internet, it's also exposed to threats. And that's precisely why the cybersecurity audit has become a fundamental tool for maintaining operational continuity and preventing further damage.
Before delving deeper into this type of analysis, it is worth mentioning a solution driving a remarkable evolution in the sector: Kartos by Enthec,. a platform designed for companies that need a clear, consistent view of their exposure. More than just a monitoring tool, Kartos is part of the Continuous Management of Threat Exposure.
Throughout the article, you will understand why both things need each other and how integrating them can strengthen the security of any company.
What is a cybersecurity audit, and why should you care?
Although it may sound technical, this type of audit is simply a detailed analysis of an organization's systems to assess its actual level of protection. When someone asks what a cybersecurity audit is, the answer involves checking processes, infrastructure, internal policies, and any weaknesses that attackers could exploit.
Unlike other technical reviews, an audit examines habits, roles, access, security culture, and the way things are done. It's not enough to have good firewalls: you have to review how information is managed daily.
Cybersecurity auditing for companies is a necessity
In practice, security incidents don't only affect banks or large technology companies. Therefore, cybersecurity audits in businesses are no longer just a recommendation; they are now a mandatory step for any organization that depends, even minimally, on its systems.
The most interesting thing is that the result of a good audit is not just a report. It also provides:
- A clear record of vulnerabilities.
- A roadmap to solve them.
- Indicators of the return on investment in security.
- Guidelines for improvement, both technical and organizational.
- A higher level of regulatory compliance (GDPR, ENS, ISO 27001…).
And if the company combines this one-off audit with CTEM tools like Kartos, continuous monitoring allows it to detect new threats even after correcting previous ones.
Types of cybersecurity audits: approaches according to need
When discussing the types of cybersecurity audits, they are usually divided into three main categories:
1. Internal cybersecurity audit
The internal cybersecurity audit is conducted from within the organization. It is typically carried out by in-house teams or consultants who work closely with the company.. Their main advantage is that they understand the real context, procedures, and potential points of friction.
It is beneficial for:
- Verify compliance with internal policies.
- Review access and permissions.
- Analyze data management.
- Check the staff's level of awareness.
2. External Audit
The external audit aims to obtain an independent and unbiased view.. Specialized third parties usually intervene, analyzing the system from the perspective of a real attacker and combining methodologies such as OWASP or OSINT analysis.
It adds value by allowing you to identify failures that have gone unnoticed and to validate whether internal measures actually work.
3. Specialized technical audits
They include tests such as:
- Pentesting (controlled attacks).
- Code review.
- Network analysis.
- Phishing simulations.
- Cloud security review.
This set allows for a comprehensive view and is suitable for companies with more specific needs or complex infrastructures.
Why an audit is not enough without continuous monitoring
This is where Enthec's CTEM perspective becomes especially relevant. Although the audit provides a detailed snapshot of the moment, that snapshot can become outdated in a matter of weeks. Systems change, new updates are installed, vulnerable software appears, or information is unintentionally exposed.
Platforms like Kartos allow the company to:
- Detect data leaks or exposures in real time.
- Identify open services that shouldn't be open.
- Continuously monitor domains, subdomains, or IPs.
- Receive direct alerts when a relevant threat appears.
- Prioritize risks according to their actual impact.

Main benefits of auditing cybersecurity
Everything learned during the audit is a dynamic process that evolves in tandem with the business. This allows us to gain various advantages for the organization.
1. Reduction of economic risks
An attack can paralyze operations for days. The average cost of a security breach is estimated to exceed $4.45 million. Obviously, these figures are lower for small and medium-sized businesses (SMEs), but the proportional impact remains enormous.
2. Better decision making
When a company has clear, well-explained, and prioritized results, it knows where to invest and what to expect in return.
3. Alignment with legal requirements
In regulated sectors, demonstrating that regular audits are conducted is almost mandatory. Audits facilitate this traceability and provide verifiable reports.
4. Strengthening customer confidence
More and more users and companies are asking about security before hiring services. Demonstrating formal auditing processes can be a deciding factor.
How Kartos fits into the audit cycle
We can summarize the relationship between both elements in three steps:
1. Before the audit
Kartos identifies exposures, neglected domains, vulnerable services, leaked information, and emerging risks. This allows for audit preparation using real-world data.
2. During the audit
Auditors can use Kartos' findings to delve deeper into critical areas, reducing time and improving accuracy.
3. After the audit
Instead of leaving the report in a drawer, Kartos maintains active surveillance, detects new flaws, and alerts when something is at risk again.
In other words, the audit establishes the framework, and Kartos keeps it up to date.
The combination of traditional auditing and continuous monitoring is currently the most realistic way to protect a business. Auditing detects structural weaknesses; a CTEM platform, such as Kartos, prevents those weaknesses from recurring without warning.
If your company has not yet conducted a cybersecurity audit, or if you have been putting it off, now is the time to do it.
Do you want to discover how to improve your company's security with Kartos? Contact Enthec to learn how to combine regular audits with a continuous monitoring system to help you anticipate real threats.
Mobile device security: the key to protecting your digital identity
Mobile devices have become an extension of our daily lives. We store photos, documents, conversations, passwords, and even banking information on them.
This level of dependence has made mobile device security a crucial issue not only for businesses but also for individual users seeking to protect their digital identity.
Today, cybercrime is no longer limited to large corporations or sophisticated attacks on corporate networks. Every mobile phone is a potential entry point for attackers. That's why understanding mobile device security and implementing effective protective measures is essential to keeping our personal information safe.
Before delving into practical recommendations, it's worth getting to know a tool that helps more and more people every day: Qondar, Enthec's cyber-surveillance solution designed to protect people from digital threats.. Through Continuous Threat Exposure Management, Qondar helps detect vulnerabilities, data leaks, and potential incidents before they can be exploited. In other words, it allows you to understand and control your digital footprint to keep your identity safe.
The growing digital exposure: a silent challenge
Every app we install, every public Wi-Fi network we connect to, or every file we download can open a door to cyberattacks. According to Verizon's "Mobile Security Index 2025" report, 70% of companies acknowledge having experienced security incidents on their employees' personal mobile devices in the past year.
But the problem doesn't only affect the business sector. Individuals are also frequent targets. Fake apps, malicious links on social media and even simple fraudulent SMS messages can compromise a large amount of personal data. The main problem is that most users underestimate the factors that affect mobile device security, trusting that common sense is enough to prevent an attack.
However, the reality is that cybercriminals evolve as fast as technology.. New techniques, such as “smishing” (phishing through SMS) or attacks through seemingly legitimate applications, have become increasingly sophisticated.
Factors that affect the security of mobile devices
Security in the mobile environment depends on multiple factors. Some of these are readily controllable by the user, but others require more advanced monitoring and protection tools.
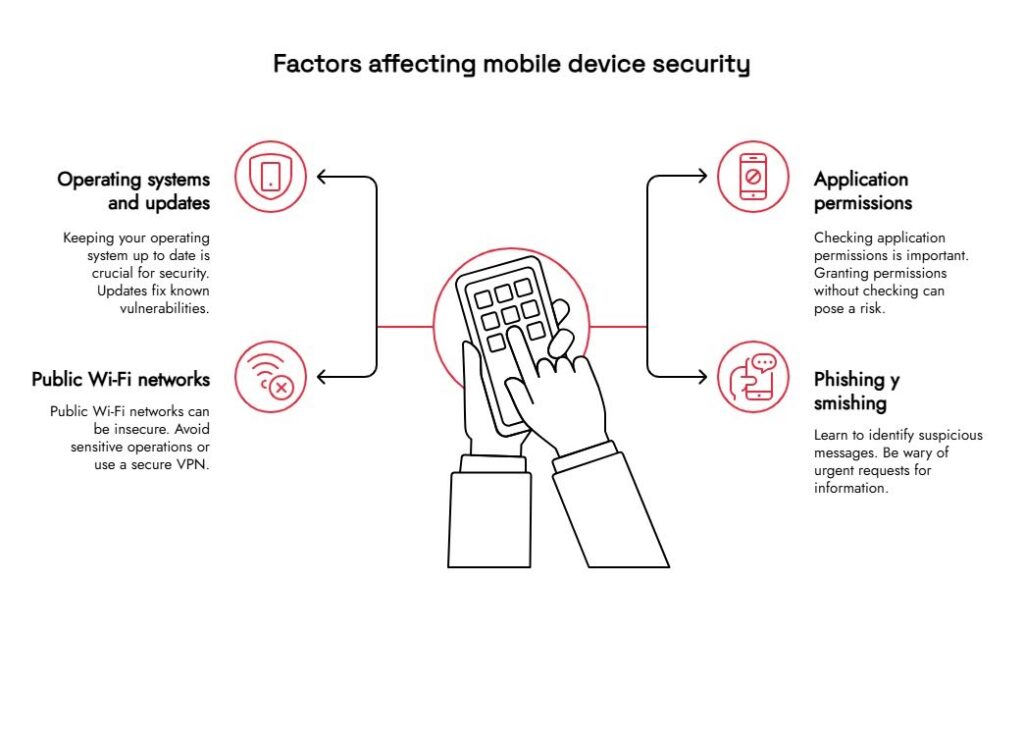
1. Operating systems and updates
One of the most relevant aspects of mobile device security is operating system maintenance. . Each new version of Android or iOS includes patches that fix known vulnerabilities. Even so, many users delay these updates, leaving their devices vulnerable.
2. Application permissions
Apps often request permission to access the camera, contacts, or location. While many of these requests are legitimate, granting them without review can pose a risk.. Periodically reviewing which applications have access to what information is a basic but effective measure.
3. Public Wi-Fi networks
Open Wi-Fi networks, such as those found in cafes or airports, can be a point of attack. Criminals can intercept traffic and obtain passwords or confidential information. It is advisable to avoid performing sensitive operations (such as online banking) on public networks or, if that is not possible, use a secure VPN
4. Phishing and smishing
Through emails or messages, attackers try to trick users into revealing information or downloading malware. Learning to identify suspicious messages, checking URLs before clicking, and being wary of urgent requests for data are fundamental steps to avoid these mobile device security incidents.
Mobile device security measures that actually work
In addition to good digital habits, there are mobile device security measures that anyone can easily and effectively implement:
- Secure screen lock: use fingerprint, facial recognition, or a strong PIN.
- Two-factor authentication (2FA): mainly used on social media, in banking, or for email.
- Device encryption: systems activate it by default, but it's best to double-check.
- Review the download sources: Only install apps from official stores like Google Play or the App Store.
- Regular backups: This minimizes losses if the device is compromised.
These measures do not eliminate the risk, but they significantly reduce the exposed area. And it is precisely in this constant reduction that we must apply the proactive cyber surveillance that Enthec proposes with Qondar.
Qondar: personalized digital surveillance
Qondar is not an antivirus or a cleaning application. It is an advanced digital surveillance solution that continuously analyzes a user's online exposure. Through the CTEM methodology, the tool identifies vulnerabilities, monitors for personal data leaks, and alerts in real time about threats.
For example, if your data appears in a data breach or your phone number is published on an information marketplace forum, Qondar detects it immediately and notifies you. This way, you can take action before the damage becomes irreparable.
The most interesting thing is that Qondar does not require advanced technical knowledge.. Its approach is designed for individual users concerned about their digital privacy, from professionals who manage sensitive information to people who simply want to avoid being victims of fraud or identity theft.
Mobile security as part of your digital well-being
Thinking of mobile device security as merely a technical matter falls short. It's really a matter of personal well-being. Protecting your phone means protecting your memories, your conversations, your finances, and ultimately, your identity.
Adopt a proactive approach, review permissions, keep updates current, and use monitoring tools like Qondar not only reinforces security but also peace of mind.
Furthermore, t demand for CTEM tools will grow by 35%, especially in hybrid environments where professional and personal life are intertwined.
How to start protecting yourself today
To improve the security of your mobile devices, the first step is to understand your digital exposure. Knowing what information about you is accessible on the Internet, what applications have access to your data, and what vulnerabilities you might have is essential.
Qondar, from Enthec, offers you that visibility.. It is a continuous cyber-surveillance tool that turns information into protection, helping you make informed decisions about your online security.
Mobile device security is no longer optional; it's a basic necessity in today's connected world. Cyberattacks don't discriminate between large corporations and individual users: we are all potential targets.
Taking simple steps, staying informed, and having continuous monitoring tools are the best ways to maintain peace of mind.
Protecting your digital identity starts with your mobile phone. And today, you have solutions at your fingertips that make it easier than ever.
Discover how Qondar can help you stay one step ahead of threats. Contact us and take the first step towards a safer digital life.
How to implement industrial cybersecurity in your company
If your company is on a path of digital transformation, you should know that industrial cybersecurity is a critical asset to manage.
In this article, we explain, in a clear and accessible way, how to implement industrial cybersecurity in your company, what you should consider, and the role solutions like Kartos by Enthec can play in helping you.
Suppose you're looking for a tool that continuously manages threat exposure in industrial environments. In that case, it's worth considering Kartos,. a continuous monitoring solution designed for organizations that lets you monitor, assess, and respond to cybersecurity risks on an ongoing basis.
Why is industrial cybersecurity critical now?
The adoption of technologies characteristic of the “fourth industrial revolution” (also known as Industry 4.0) is expanding the scope and complexity of risks in industrial environments.
For example, many companies in the industrial sector are integrating previously unconnected control systems, robots, and IoT sensors, thereby expanding the attack surface.
In this context, implementing a robust cybersecurity strategy for Industry 4.0 is no longer only about protecting data, but also about safeguarding critical operational processes, controlling physical and digital risks, and ensuring business continuity.
You might be interested in→ IoT and cybersecurity: Risks and strategies to protect connected devices.
Step 1: Diagnosis and awareness
Before taking action, you need to understand the situation. This first step involves analyzing your company's current state, identifying vulnerabilities, and building a knowledge base to support a solid strategy. Without a precise diagnosis, any action will be incomplete or ineffective.
Initial assessment
The first thing you need to do is understand your company's current state regarding industrial cybersecurity.. This implies:
- Map assets: machinery, control systems, OT (operational technology) networks, IoT devices.
- Identify connections within the IT environment (information technology) and OT.
- Knowing which protocols, standards, and policies already exist (for example, is your company aligned with the ISA/IEC 62443 standard for industrial control systems?).
- Evaluate the safety culture: What do employees know, what practices are followed, what training is available?
Raising awareness
Technology is not enough if people don't know what they are doing or what risks they face. Here, training and awareness remain key for Industry 4.0 cybersecurity.

Step 2: Defining a strategy adapted to the industrial environment
Once you understand your weaknesses and your organization's maturity level, it's time to define a coherent strategy. This lays the foundation for industrial cybersecurity, guiding technical, human, and operational decisions.
Governance and roles
Your company must determine who is responsible for cybersecurity:IT, OT, security, and production teams. A clear governance structure facilitates the integration of industrial cybersecurity into daily operations.
Policies, standards, and controls
Define internal policies that:
- Segregate IT and OT networks or establish adequate security perimeters.
- Review and update industrial hardware and software.
- Monitor the entire network: connected devices, anomalous traffic, access controls, etc.
Continuous defense strategy
This is where the concept of CTEM (Continuous Threat Exposure Management) comes in. A single assessment is not enough: Risks change, vulnerabilities emerge, attackers evolve.. Solutions such as Kartos by Enthec enable continuous monitoring, tailored for industrial environments, to detect, assess, and respond dynamically.
Implementing industrial cybersecurity with this philosophy implies a change of mindset: from reacting to incidents to anticipating them.
Step 3: Technical Implementation. Best practices for cybersecurity in Industry 4.0
Now comes the practical part. It's time to implement the technical measures that bring the strategy to life. Here, theory becomes concrete action: segmenting networks, controlling access, monitoring, protecting, and responding.
Network segmentation and isolation
In an industrial environment, it's common to have control networks (e.g., SCADA and PLCs), production networks, and administrative networks. You must segment to limit damage in case of an attack.. This measure appears among the most recommended in Industry 4.0 studies.
Updates and patches
One of the most frequent intrusion vectors is legacy or outdated systems.. Industrial cybersecurity requires regularly reviewing industrial equipment (sensors, controllers, gateways) and implementing proactive security measures.
Threat monitoring and detection
Here again, continuous monitoring is key. Thanks to CTEM systems like Kartos, you can monitor anomalies, events, unusual access, and OT device behavior.
Identity and access management
Limit who can access which system.. This includes privileged access management, strong authentication, activity logging, and deletion of inactive accounts. In Industry 4.0, with an ever-increasing number of connected devices, this aspect becomes critical.
Incident response
Have a plan: What should be done if a device is compromised? How should a segment be isolated? How should operations be restored? As noted, many facilities still lack an adequate response plan.
Step 4: Practical cases and examples in cybersecurity of Industry 4.0
- A manufacturing plant that has deployed IoT sensors to monitor machinery conditions can be exposed if those sensors are not on a segmented network or under constant supervision; an attacker could access the control network and alter parameters.
- Another example: the convergence of IT and OT without security coordination, which can result in administrative access (from IT) granting unauthorized access to OT systems. This lack of synchronization between IT and OT is a key risk.
- Also, facilities that lack continuous monitoring of OT traffic and have not assessed emerging vulnerabilities. According to recent studies, industry protection must evolve toward a multi-layered, continuous, and adaptive approach.
Step 5: How to integrate a solution like Kartos into your plan
The Kartos tool from Enthec enables you to implement a continuous threat monitoring system tailored to the industrial environment. Here are some key points on how it fits in:
- Visualizing the risk landscape: Kartos groups incidents, vulnerabilities, and connected devices, enabling you to gain a global view of your company's exposure.
- Active monitoring: not only specific analyses, but constant monitoring of behaviors, early warnings, and response capacity.
- Recommendations and prioritization of actions: In the face of multiple vulnerabilities, Kartos helps prioritize based on operational impact and real risk.
- Integration with your industrial cybersecurity strategy: relying on defined processes, policies, and training, Kartos becomes an ally, not only a tool.
If your company works with industrial systems, control networks, connected sensors, and automated machinery, a solution like Kartos enables you to shift from a reactive to a proactive approach to industrial cybersecurity.
Step 6: Measurement, review, and continuous improvement
Industrial cybersecurity is not a finish line, but a process of continuous improvement. You must establish indicators (for example: number of vulnerabilities detected, average response time, percentage of segmented devices, number of OT incidents detected), review them periodically, and adjust your strategy accordingly.
Furthermore, production environments are changing (new devices, new interconnections, new suppliers), and therefore, Industry 4.0 cybersecurity requires updated plans and controls.. Adapting to a rapidly evolving threat landscape is becoming increasingly important.
Implementing industrial cybersecurity in your company is a challenge, but also a great opportunity: an opportunity to strengthen your operations, protect your assets, ensure continuity, and trust that digitalization will not expose you to preventable attacks.
To do it successfully:
- Start with the diagnosis and awareness.
- Define a clear strategy with governance, policies, and continuous monitoring.
- Apply specific good technical practices: segmentation, updates, monitoring, controlled access, and incident response.
- Integrate tools adapted to the industrial environment.
- Establish a continuous cycle of measurement, review, and improvement.
The transformation to Industry 4.0 opens many doors, but it also demands that cybersecurity be an integral part of the process.. In Enthec, we are prepared to help you take this step with confidence and vision.
Would you like us to design an industrial cybersecurity plan tailored to your company? Contact our team. Let's begin today.