Cybersecurity in law firms: How to know if your confidential data has already been exposed
Information is worth more than ever.. In the case of law firms, this takes on a critical dimension: we are not just talking about sensitive personal data, but of highly confidential information related to court cases, contracts, businesses, inheritances, international litigation, or even legal strategies.
The leak of just one of these documents can lead to devastating consequences for both clients and the office itself.
And the question is inevitable: Do you know if your data, or that of your customers, has already been exposed without your knowledge?
Cybersecurity in law firms: an urgent challenge
Cybersecurity in law firms is not a luxury, nor a fad, nor something that can be put off until tomorrow. It is an obligation.
The legal sector has historically been one of the most conservative in technological terms, resulting in a significant gap between the digitalization of its processes and the level of protection it offers.
As law firms adopt technological solutions to work more efficiently, so do attack vectors: emails, misconfigured servers, employee accounts, collaborative tools, and a long list that cybercriminals are well aware of.
Is your data already exposed online?
One of the most common mistakes is to think that only large companies or high-profile cases are targeted. The reality is different: Attacks do not discriminate by size or notoriety;. in many cases, criminals target smaller firms because they know their defenses are weaker.
This is where the concept of Continuous Threat Exposure Management (CTEM) comes in. This approach goes beyond traditional antivirus or firewalls: it's about constantly monitoring the digital perimeter of your office to detect leaks, vulnerabilities, or data that are already circulating on the network, including the dark web, without anyone being aware of it.
Kartos: A cybersecurity tool to take control
In this context, Kartos, the solution developed by Enthec, stands out as a cyber surveillance tool adapted to the real needs of law firms.
Kartos is a Continuous Threat Exposure Management platform that monitors in real-time whether a firm's digital assets, such as domains, emails, credentials, and devices, are compromised or at risk. And not only to protect the firm itself, but also to monitor the cybersecurity status of its clients, providing a competitive and operational advantage that is increasingly valued in the legal sector.
Thanks to Kartos, law firms can:
- Detect proactively leaks of confidential information.
- Verify if there are email accounts associated with the office that have been compromised.
- Obtain certified digital evidence that may be helpful in litigation or claims by clients who are victims of cyberattacks.
- Control regulatory compliance for client companies, thereby offering an added service of great value.
What if your firm could detect a security issue at a client company before it becomes news?
How do you know if your office has already been affected?
Red Flags
Your firm may have suffered a security breach without your knowledge. Some signs that should put you on alert:
- Clients are receiving suspicious emails that appear to come from the firm.
- Appearance of your internal documents in strange places.
- Leaks of emails, passwords, or databases.
- Suspicious movements in bank accounts related to the firm.
- Unexplained incidents such as account lockouts or unauthorized changes.
If you want to take action before these warning signs occur, we recommend you take a look at our post → How to manage business passwords and credentials easily and securely to avoid online threats.

Check if you are exposed
The best way to check if your data is already circulating on the internet or in shadowy environments, such as the dark web, is to use specialized tools. Kartos automates this analysis and generates a comprehensive report that identifies assets at risk, their location, level of exposure, and the severity of the issue.
The important thing is not only to detect, but to act quickly.
The legal advantage of staying ahead with cybersecurity in law firms
It's not just about protecting the firm's interests. In the legal context, anticipating risks is also a matter of professional responsibility.. If your client suffers a cyberattack and you, as their legal advisor, can provide objective and verifiable reports on the status of their digital exposure, you will be taking a step forward in your role as a professional.
In addition, Kartos provides the possibility of monitoring the cybersecurity of third parties, making it a key tool for expanding services in the area of technological compliance or claims related to cybersecurity incidents.
And what about self-employed workers or individual lawyers?
For self-employed legal professionals, Enthec has also developed Qondar, a personal cyber surveillance solution that allows you to detect whether your digital identity has been compromised.
Cybersecurity is part of your professional reputation as a lawyer.
The prestige of a law firm is not based solely on its successful rulings or the reputation of its partners. Today, trust is also built in the digital realm.. A client who submits their most personal or business documentation expects, at the very least, that it will be responsibly protected.
Cybersecurity in law firms is no longer an option; it's an operational and reputational necessity.
Want to know if your firm data has already been exposed?
Start now by contacting us, and discover Kartos, Enthec's solution that is already helping law firms throughout Spain protect their reputation and clients.
Applying OSINT to cybersecurity: A valuable guide for professionals and teams
Protecting the information is no longer just a task for large corporations or government departments. Every company, regardless of size, is exposed to risks that evolve at a dizzying pace.
In this context, open source intelligence (OSINT) has become a key tool in cybersecurity. But what exactly does applying OSINT mean in the professional field, and how can it make a difference in an increasingly hostile digital environment?
Before delving into the details, it's worth highlighting the role of Kartos, Enthec's solution designed specifically for companies seeking to elevate their cybersecurity strategy to the next level. Kartos allows you to continuously monitor your exposure to external threats, automating processes for collecting and analyzing public information about the company, its employees, and its digital infrastructure.
What is OSINT?
The term OSINT (Open Source Intelligence)refers to a process by which publicly available information is collected, analyzed, and utilized, information that is legally accessible to anyone, to obtain practical knowledge.
In cybersecurity, this means detecting potential attack vectors before they are exploited, finding leaked information from an organization, or anticipating vulnerabilities using data available on the network.
Why is OSINT important in cybersecurity?
Applying OSINT techniques enables security teams to anticipate threats, gain a deeper understanding of their public exposure, and identify and address weaknesses before malicious actors can exploit them. It's like conducting an audit from the attacker's point of view.
Among the most relevant benefits, the following stand out:
- Early identification of information leaks.
- Detection of fake domains or profiles that impersonate the brand.
- Assessment of the level of exposure of key employees.
- Discovery of leaked credentials on forums and dark websites.
All of this can be accomplished without compromising the legality of the process, as all the information is extracted from open-source OSINT sources, including search engines, social networks, public databases, forums, among others.

The OSINT process step by step
Although there are many methodologies, the OSINT process is typically divided into five fundamental phases. Understanding them is key to effectively integrating this discipline into cybersecurity workflows.
1. Definition of objectives
Before you start searching for data, it's essential to know what you're looking for. This could include research on a specific company's exposure, a manager's fingerprint, or the evaluation of an external supplier.
2. Selection of OSINT sources
This is where open-source OSINT comes in: from Google and social media, to logs, DNS records, pastebin services, forums on the deep web, or platforms like Shodan or Have I Been Pwned.
3. Data collection
At this stage, we utilize automated or semi-automated OSINT tools to facilitate the gathering of large amounts of information. . This is essential to document this phase well, so that the data is traceable and verifiable.
4. Analysis and correlation
Data alone is worthless if it's not interpreted correctly. Here, the collected information is analyzed, irrelevant information is discarded, and hypotheses about potential risks or vulnerabilities are generated.
5. Presentation and performance
Once the level of exposure is understood, action is necessary: delete sensitive information, change leaked passwords, and contact platforms to remove unauthorized content, among other measures.
Apply OSINT with a strategic vision
OSINT is often associated with specific investigative tasks, such as "ethical hacking." However, the true power of OSINT lies in its integration into a continuous defense strategy, known as CTEM (Continuous Threat Exposure Management).
In this sense, Kartos allows you to make that leap in quality by offering:
- Daily automation of the OSINT cycle.
- Customized reports for each company.
- Proactive detection of leaks, malicious domains, data leaks, and impersonation.
- Integration with existing cybersecurity team workflows.
With a tool like Kartos, companies can stop being defensive and start playing offense digitally, understanding what sensitive information is being leaked or published without authorization.
Good practices for applying OSINT in teams
In addition to having adequate tools, it is essential to develop operational routines and internal policies that allow you to get the most out of OSINT:
- Train employees about what information they can share on networks.
- Establish periodic controls on the organization's digital footprint.
- Define clear responsibilities within the security team to manage these tasks.
- Combine OSINT with other disciplines, such as threat intelligence, red teaming, or risk management.
The use of OSINT in cybersecurity is not a fad or a mere technical curiosity. It is a real necessity in a context where every leaked or mismanaged piece of data can be a security breach.. Therefore, adopting a proactive approach, with tools like Enthec's Kartos, can mean a considerable advantage for companies that prioritize their digital security.
Cybersecurity is not just about reacting to incidents; it's about anticipating them. And to anticipate, nothing better than seeing what the attackers see.
Do you want to know what information about your company is circulating online before it's too late?
Discover Kartos, our solution that automates and monitors your exposure to digital threats. Start protecting your organization from a professional, real-time OSINT perspective. Contact us.
Enthec, specialists in cyber surveillance, OSINT, and proactive digital exposure management. With solutions like Kartos for businesses and Qondar for individual users, we help prevent rather than cure.
Is your sensitive data circulating on the internet without your knowledge? Here's how to check.
Shopping online, booking a trip, managing your bank account from your mobile phone, or simply signing up for a social network means leaving a trail. The worrying thing is that, often, we are not aware of the extent to which our sensitive data is exposed, or worse still, is already circulating on the network without our knowledge.
In this article, we will discuss how to verify if your sensitive data has been compromised, what types of information are considered critical under the GDPR, and how to protect it with specialized tools, such as Qondar.
First of all, what exactly is sensitive data?
Not all personal data is equally relevant or requires the same level of protection. According to the General Data Protection Regulation (GDPR), sensitive personal data is that which reveals:
- The ethnic or racial origin
- The political opinions
- The religious or philosophical convictions
- The Union membership
- Data genetic or biometric
- Data related to the health
- The sexual life or sexual orientation of a person
In addition to these, sensitive data is also considered to be that which, by its nature, may pose a greater risk if it falls into the wrong hands, such as identity documents, bank accounts, passwords, physical addresses, personal phone numbers, or information about your children.
Knowing what a person's sensitive data is is crucial to understanding why it is so attractive to cybercriminals.
You might be interested→ How to protect your digital identity against major threats.
Why is it so easy for your data to end up in the wrong hands?
In many cases, you're not doing anything wrong. One of the platforms you're registered with simply suffers a breach, or you inadvertently access an unsecured public Wi-Fi network. Even a simple download can open the door for your information to end up in a black market database.
The worrying thing is not just the leak itself, but the time that passes until the user finds. that data may have been circulating on obscure forums for months (or even years) without even knowing.

How do you know if your sensitive personal data is already online?
Digital exposure is more common than it seems
You don't have to be a public figure or a company executive to be a victim. Indiscriminate attacks are the most frequent, and many cybercriminals operate under the logic of “the more, the merrier.”
There are free platforms to check if your email or passwords have been leaked, such as Have I Been Pwned. However, these tools provide limited vision and shallow insight into the problem.
Qondar, your ally for continuous protection
This is where Qondar comes in, a solution developed by Enthec, specializing in cybersecurity and cyber surveillance. Qondar goes a step further than conventional platforms: it doesn't just alert you if your email has been leaked, but also performs a continuous surveillance on the open web, the deep web, and the dark web to detect whether your sensitive data is being traded, shared, or used without your consent.
Qondar is part of a new generation of Continuous Threat Exposure Management (CTEM) tools, a proactive approach that enables you to anticipate potential cyberattacks rather than just react after they occur.
Thanks to its automated intelligence engine, Qondar monitors your fingerprint and alerts you in real-time if any information is compromised, including passwords, card numbers, identification documents, or sensitive personal data.
What can I do if I discover my data has been leaked?
We recommend:
- Cambia tus contraseñas inmediatamente. Start managing passwords for your most sensitive accounts, including email, banking, and social media.
- Activate two-step verification whenever possible.
- Keep a close eye on your bank accounts and digital platforms with increased attention during the following months.
- Contact the affected services to know the extent of the leak.
- Consider using a tool like Qondar to receive early warnings and make timely decisions.
The importance of prevention: reacting is not enough
The reality is apparent: Protecting your sensitive data is not optional; it is necessary. . Doing it just once isn't very useful. Digital exposure is dynamic and constantly changing. Therefore, the approach must be continuous, as proposed by Continuous Threat Exposure Management.
With Qondar, you have a solution that is efficient, automatic, and in real-time, designed for individuals who value their privacy and security in today's digital world.
What sets Qondar apart from other solutions?
- Complete coverage: Tracking multiple layers of the internet, not just the surface.
- Proactive detection: Qondar doesn’t wait for a crisis to act.
- Simple interface: No advanced technical knowledge required.
- Clear and helpful alerts: You will know exactly what information is compromised.
Furthermore, being developed by Enthec, a company with extensive experience in the business field thanks to Kartos (the corporate solution), Qondar benefits from a solid and proven know-how record in the world of cybersecurity.
What if nothing has ever happened to me?
That is precisely the trap. Many leaks do not generate immediate effects. and can take months for someone to use that data against you. A hacked account could be silently used to spy on, send spam to, or even impersonate you on other platforms.
According to a 2022 Norton study,1 in 5 people in Spain have been victims of some cyber fraud,but only half were aware of it at the time it occurred. The other half discovered it late, after the damage had already been done.
Protect yourself now. Because tomorrow could be too late.
If you've made it this far, it's because you know something isn't quite right about how we protect (or don't protect) our information on the Internet. Good intentions are not enough.. Your information circulates, with or without your permission. The question is: do you want to know before it happens or after it happens?
Qondar can help you regain control. Start your digital surveillance today and keep your sensitive data out of the hands of cybercriminals.
Are you unsure whether your sensitive personal data has already been exposed? Find out today with Qondar. Because in the digital world, the best defense is anticipation.
Request more information here.
Ransomhub and the new reputational threat
We live in a time when cyberattacks no longer only seek to steal information or collapse systems, but also directly damage the reputation of organizations.
One of the most recent and worrying examples is Ransomhub. This group is reinventing the way ransomware groups operate, with a strategy that combines blackmail, public extortion, and fear marketing.
Before delving into detail, it's worth briefly discussing Kartos, Enthec's solution for businesses seeking to stay ahead of emerging threats. Kartos isn't an antivirus or a simple perimeter shield. It's a Continuous Threat Exposure Management (CTEM) platform designed to help organizations detect vulnerabilities, track external threats, and make informed decisions before damage is real.
In the current context, with threats like Ransomhub, solutions like Kartos are no longer just an “extra” but an essential asset.
What is Ransomhub?
Ransomhub is a cybercriminal group specializing in ransomware attacks, a type of malware that blocks access to systems or encrypts a company's data until a ransom is paid. What sets Ransomhub apart from other similar groups isn't so much its technology, but its strategic approach: its accurate weapon is the victim's reputation.
Unlike other cybercriminals, who encrypt data and wait for payment, Ransomhub has taken the concept of ransomware to a more psychological and media-driven level.
They publish confidential information, they make public statements, use social networks and specialized forums to publicly humiliate victims and exert pressure not only technically, but socially.
A “brand” of fear
Ransomhub isn't hiding anything. It even has a kind of "portal" where they announce new victims, much like a corporate blog. The aesthetic, language, and strategy seem straight out of a marketing campaign: they create narratives, document attacks, and aim for virality.
Its objective is clear: turn every attack into an example,a warning to other companies. If an organization fails to pay, it not only loses its data but also has its name appear on a public list, alongside leaked files, internal documents, and even private communications.
The damage is not only economic, it is also reputational and, in some cases, irreversible.

Ransomhub malware: how it works and why it's a concern
The RansomHub malware combines classic ransomware elements with new infiltration and manipulation techniques. It usually accesses systems by exploiting known vulnerabilities,often through leaked credentials on the dark web or through social engineering. Once inside, the malware encrypts the data and sends a clear message: either you pay, or everything becomes public.
But, as we said before, what really distinguishes Ransomhub is how it exposes its victims:
- Publication of confidential documents on publicly accessible portals.
- Leveraging social networks and forums to amplify the damage.
- Indirect pressure through contact with customers, suppliers, or the media.
This approach has put many organizations on alert; the damage to the image can be even more costly than the rescue itself, but giving in to Ransomhub's pressure can be just as dangerous.
Are we prepared for this type of threat?
The question is not whether a group like Ransomhub can target a company, but when. . Today's hyperconnectivity and the use of multiple digital tools mean that any organization's exposure surface is constantly growing.
That's why it's essential to adopt cybersecurity strategies that go beyond reactive measures. This is where the CTEM (Continuous Threat Exposure Management) model comes into play, proposing a proactive and continuous approach to identify and mitigate risks before they escalate into real attacks.
How Kartos can help you against threats like Ransomhub
Kartos, Enthec's business solution, is designed specifically for this type of context. Its primary function is to offer an external, real-time view of an organization's cyber exposure status.
This translates into very concrete benefits:
- Early detection of leaked credentials, possible access points, or spoofed domains.
- Threat monitoring on the dark web and on channels commonly used by groups like Ransomhub.
- Automated alerts in the event of suspicious activities or information leaks.
- Clear and easy-to-interpret panels, designed to facilitate decision-making by the security team.
The goal is not to eliminate risk (something impossible), but to minimize exposure and react quickly and strategically to any warning signs.
Why is reputation now the main target?
Companies have invested in firewalls, antivirus software, and internal training, but many still neglect their external digital image. . Today, a poorly managed incident can become more visible and damaging than the technical attack itself.
Groups like Ransomhub have understood this perfectly. They are no longer just looking to make money, but to generate fear. Their power lies in their ability to hurt where it hurts most: the trust that customers and partners have in the company.
What you can do now to protect yourself
Beyond technical solutions, there are several key actions every organization should consider to reduce the impact of these types of threats:
Review and minimize exposure
Conduct regular audits of systems, users, and access points to ensure security and compliance. Review the publicly visible information and identify what an attacker could exploit for infiltration or extortion.
Implement constant external monitoring
Using cybersecurity solutions, such as Kartos enables organizations to stay informed about the outside world. This allows them to monitor what is being said about their company on the dark web, detect leaks early, and take action before they become public headlines.
Prepare a reputational response plan
In addition to the technical plan, it is essential to have a crisis communication strategy:. What is said? How is it said? Who is responsible to the media, clients, or partners? The speed and consistency of the message can make all the difference.
Ransomhub is not just malware; it's a message
When you ask yourself what Ransomhub is, the answer goes beyond malware. It's a new form of extortion, more sophisticated, more public, more dangerous,. and, above all, it's harder to manage if you're not prepared.
It's not enough to protect yourself from the inside. Today, it's essential to stay aware of what happens outside the company,. to consider how an attacker might perceive you, to understand their potential actions if they were to harm you, and to anticipate potential threats. In this sense, Kartos isn't just a security tool. It's a window to the other side of the mirror.
Want to know what attackers know about your business? Contact us and see how you can anticipate threats like Ransomhub before it's too late.
How to detect CVE vulnerabilities on your digital surface without touching your internal network
Detecting a threat before it's exploited is one of the most important priorities for any organization with a digital presence today. But how can you achieve this without compromising your internal network? Is it possible to have real visibility into your vulnerabilities without performing intrusive or invasive scans? The answer is yes, and tools like Kartos by Enthec are making it possible.
Kartos is an advanced solution for Continuous Management of Threat Exposure (CTEM), designed specifically for businesses. It enables you to identify, prioritize, and address digital weaknesses before an attacker can exploit them as an entry point.
Through an external, non-intrusive, and fully automated approach,Kartos continuously scans your digital footprint, including domains, subdomains, exposed applications, cloud assets, public configurations, and other relevant information. All without the need to install agents or access your internal network.
Are you interested in learning how you can reduce your risk of cyberattacks without modifying your current infrastructure? Discover how Kartos can help you take the next step toward a more confident and proactive posture.
What is a CVE, and why should you pay attention to it?
Before getting into the subject, it is essential to understand what a CVE is.. The acronyms correspond to Common Vulnerabilities and Exposureswhich stands for Common Vulnerabilities and Exposures. It's an international standard that classifies and labels known security flaws in software and hardware. Each vulnerability is given a unique identifier, such as CVE-2024-12345, making it easier to track and resolve.
Why are they so relevant to your company? Because when a CVE is published, cybercriminals also become aware of it. Many rely on these lists to find organizations that have not yet patched their systems or that remain publicly exposed.
CVE and cybersecurity are terms that should always be used in conjunction. It's not enough to know them; you have to manage them proactively.
If you'd like to learn more about CVE, we recommend checking out our content: What is a CVE?

How are CVE vulnerabilities detected from the outside?
There is a widespread belief that detecting vulnerabilities requires performing internal scans, installing agents, or accessing the company's network. However, this is no longer true. Thanks to modern approaches such as CTEM, you can map your entire exposure without touching a single line of your private network.
How does the Kartos model work?
At Enthec, we developed Kartos as a solution that simulates the vision of an external attacker. In other words, it analyzes everything exposed on the Internet that forms part of your company's digital footprint, including IP addresses, domains, SSL certificates, web endpoints, public metadata, open configurations, and poorly protected cloud buckets. Based on this information, it detects whether any of these assets are vulnerable to known CVEs.
Correlation of assets and CVEs
Once the exposed digital assets have been identified, Kartos cross-references them with public vulnerability databases (such as NIST, MITRE, ExploitDB, among others) to determine if they are affected by any CVE. This process is automated and ongoing, allowing for:
- Detect new vulnerabilities as they are published
- Find out if any of your assets are affected
- Prioritize actions based on the actual risk level
Advantages of this approach
No intrusions, no friction
One of the most significant benefits is that it does not interfere with your internal operations. . Since it doesn't require network permissions or software installation, implementation is quick and secure. It also reduces IT or technical department resistance, as nothing in the corporate environment is disrupted.
View from the attacker's perspective
A common mistake in cybersecurity is focusing solely on what happens "inside." However, attackers don't start inside your network: they begin outside. Having visibility into how a cyber attacker perceives you allows you to act before he does.
Smart prioritization
Not all CVEs are equally dangerous. Some are theoretical, while others have already been discovered to have known exploits. Kartos not only detects vulnerabilities, but it also identifies the most critical ones, helping you make more efficient and informed decisions.
What role does CVE play in modern cybersecurity?
Business cybersecurity in Spain and around the world is facing a growing problem: the escalation of cyberattacks.. Every year, we learn of new cases that occur worldwide. In this context, reacting is no longer enough; we must anticipate.
That's where the concept of CVEs as a risk indicator comes in.. Knowing which CVEs affect your digital infrastructure is a crucial first step toward developing a robust defense strategy. But just as important is discovering them early and consistently.
In other words, CVE management is the foundation of an active security posture.
The CTEM approach and its application with Kartos
What is CTEM
CTEM, or Continuous Management of Threat Exposure,is an approach that goes beyond one-off audits. It involves continually assessing the attack surface to identify vulnerabilities and remediate them before they can be exploited.
Why Kartos stands out
Compared to other more technical tools or those focused on internal network scans, Kartos adopts a 100% external philosophy, adapted to the real world.. It detects relevant CVEs in your visible assets, alerts you in real time, and provides concrete, actionable recommendations.
Additionally, it's scalable, enabling you to protect everything from startups to large corporations without requiring infrastructure or internal team adjustments.
What if I'm an individual? There's a solution, too.
If you are a self-employed professional or a user concerned about your digital footprint, Enthec has also developed Qondar, a solution designed for individuals. It provides visibility into your personal digital exposure, ideal for executives or professionals at risk of targeted cyberattacks.
CVE vulnerabilities are present in almost every connected infrastructure, and waiting for them to be exploited is a luxury no company can afford. Cybersecurity tools like Kartos enable you to adopt a proactive and practical approach, with agile implementation, and without the need to alter your internal network through perimeter-based cybersecurity.
Detecting CVEs from the outside is not only possible, but is an increasingly recommended practice in the field of cybersecurity.
Request a free Kartos demo today and see for yourself how you can reduce your exposure to threats without changing a single line on your servers. Contact us!
The relevance of cybersecurity in telecommunications
Sending an email, holding a video meeting, or saving files to the cloud are actions we take for granted in our businesses. But behind this apparent simplicity lies a complex network that sustains telecommunications: networks, devices, providers, data…
And in that sea of constant information, cybersecurity has become an absolutely essential element for business continuity.
We're no longer just talking about protecting computers or servers, but the telecommunications infrastructure that shapes our lives. From data centers to employees' smartphones, cybersecurity in telecommunications is a key component of ensuring digital, economic, and social stability.
In an environment such as telecommunications, where the exhibition area is vast and dynamic, a solution such as Kartos is advisable and essential to ensure business continuity and protect reputation and user trust.
Unlike other more reactive approaches, our Kartos solution uses a continuous Threat Exposure Management (CTEM) model.. This means it helps organizations maintain a constant and up-to-date view of all their exposed assets, detect vulnerabilities, and anticipate possible attacks.
Why is cybersecurity so critical in telecommunications?
Telecommunications are the nervous system of our digital society,. and cybersecurity in telecommunications is a structural priority for all sectors.
A highly exposed sector
Telecommunications is one of the world's sectors that is attacked the most. It's no coincidence: Operators manage massive volumes of data,critical network infrastructures, and connections with millions of users. Any security breach can have devastating consequences: service interruptions, theft of sensitive data, espionage, or even attacks on national infrastructure.
Threats are constantly evolving
Cybercriminals never rest. New techniques, exploits, and ways to break into systems are developed daily. From ransomware attacks targeting service providers to signal interception or large-scale identity theft, having an antivirus or firewall is no longer enough.
It is necessary to have tools that proactively analyze and identify weaknesses before they are exploited, and maintain constant surveillance of the digital ecosystem. As we propose with Kartos, continuous threat management makes a substantial difference.
You may be interested in→ 6 online threats that can affect your business.
Towards a more preventive and strategic approach
The traditional security model, based on reacting once an incident occurs, is no longer enough.. In an environment as changing as the digital one, prevention and anticipation are essential.

CTEM: continuous management against threats
The traditional IT security model involved periodically reviewing systems, searching for flaws, and applying patches. However, in today's context, this methodology is insufficient. The key is constant vigilance.
Continuous Threat Exposure Management (CTEM) is a more dynamic and adaptive approach. It allows companies to:
- Know what assets are exposed on the Internet (servers, domains, applications, etc.).
- Detect misconfigurations or vulnerabilities before they are exploited.
- Prioritize what to fix first based on the actual level of risk.
Our tool, Kartos, is explicitly designed to implement this model. Its noninvasive approach allows monitoring without the need to install agents and offers a clear view of any organization's external security posture.
What your company can do now
If you work in a company that relies on digital infrastructure (which is practically all of them), there are some steps you can start considering today:
1. Perform an exposure diagnosis
Do you know how many of your company's assets are visible from the outside? How many might have insecure configurations? Having Kartos allows you to take this photo without affecting your systems.
2. Implement a CTEM strategy
Leave behind ad hoc cybersecurity, surveillance must be continuous and automated.. Threats don't wait for you to audit.
3. Teach your team
No tool can replace the human factor. Make sure your team understands the risks and knows how to respond.
In a world where everything is digital, guaranteeing cybersecurity in telecommunications is not an add-on: it's the core. Exposure to threats is constant, and the consequences of carelessness can be irreversible.
Solutions like the ones we offer with Kartos help companies of all sizes regain control of their digital security. It's not about fear but visibility, strategy, and responsiveness.
Do you want to know how exposed your organization is? Try Kartos and get a clear, actionable view of your external digital security.
Digital consent: Why accepting conditions doesn't guarantee the security of your data
We live connected lives. We browse, download, share, and accept every moment we spend on the internet. And right there, with that quick click of "Accept terms and conditions," lies one of the biggest problems of the digital age: digital consent.
Do we really know what we're agreeing to? Do we understand the implications these seemingly small decisions have on our privacy?
Even though we virtually sign that invisible contract with every app or service we use, that doesn't mean we're truly protected. In fact, it's often just the opposite.
Qondar: The tool that helps you understand and protect your digital footprint
Before we discuss the intricacies of digital consent, it's worth pausing to introduce Qondar, our solution designed for people who want to better understand what happens to their data on the Internet and how to protect their digital footprint.
Qondar focuses on helping you continuously monitor your exposure to online threats, which is known in the cybersecurity world as CTEM (Continuous Threat Exposure Management).
In other words, Qondar gives you a real-time snapshot of what the internet knows about you, so you don't have to rely solely on the privacy promises of the platforms you use.
Want to know what information about you is circulating online? Discover how Qondar can help you regain control of your data.
What is digital consent really?
The digital consent is the authorization we give, usually with a click, for an app, service, or website to use our personal data. This can include everything from our location and browsing habits to our photos, contacts, or messages.
In theory, this consent should be free, informed, specific, and revocable.. In theory, this consent should be free, informed, specific, and revocable. However, in practice, these requirements are rarely met. How many times have you read the terms and conditions before accepting them? That's right, almost never.

The problem: Accepting does not always mean understanding
This is where comes in the concept of Digital informed consent.. Because it is not just about accepting but also doing so with full knowledge of the facts. And that means understanding what data is being collected, for what purpose, for how long, and who else may have access to it.
But the reality is different:
- Many terms are ambiguous or overly technical.
- Consent is presented in very long texts that are almost impossible to read without investing a lot of time.
- You can "accept all" with a single click, but to manage each permission, you'll need to make additional clicks, drill down through menus, read external policies, etc.
This is not accidental; it is called Dark patterns, and they are techniques designed to manipulate you into making decisions that benefit the company, not you.
Why doesn't digital consent guarantee security?
Even if you give your consent, that doesn't mean your data is secure. There are several compelling reasons for this:
1. Non-transparent third parties
The data you share with a platform often doesn't stay there and is shared with third parties:
advertisers, business partners, analytics platforms... And even if you agreed to the original terms of service, that doesn't mean you've approved what these third parties do with your data.
2. Security violations
Data breaches are becoming more frequent. According to the IBM report “Cost of a Data Breach 2024", the average cost of a data breach is $4.88 million,and often, the user doesn't even realize their information has been compromised. Digital consent, no matter how clear, doesn't protect against a cyberattack.
3. Policy changes
Many companies modify their privacy policies over timeand don't always communicate clearly. What you consented to in 2021 may have changed in 2025. And if you don't find out, your data may be being used in ways you never approved.
Digital informed consent is a basis, but not a guarantee
It's not about demonizing digital consent, but understanding it for what it is: a part of the process, not a solution.. Digital informed consent is a step toward transparency, but as long as we continue to grant permission without knowing what it means, we will continue to give up control.
And what can you do as a user?
Here are some practical recommendations:
1. Don't accept for the sake of accepting
Try to take a minute to read the key points before agreeing. If an app asks for access to your microphone or photos for no obvious reason, it's a red flag.
2. Use digital surveillance tools
That's where Qondar excels. With this solution, you can:
- To know what data of yours is publicly exposed.
- Receive alerts if your information appears in suspicious places (forums, dark web, etc.).
- Evaluate your digital exposure level and make informed decisions.
3. Review permissions periodically
On your phone, in your accounts, in your browser... From time to time, review what permissions you've granted and delete any that aren't necessary.
4. Be wary of freebies
When a service is free, the product is often you,. that is, your data. Consider whether it's worth giving up personal information in exchange for functionality you can get elsewhere, more securely.
Digital consent needs to evolve
We are at a time when legislation is advancing more slowly than technology.. Meanwhile, the user remains the weakest party in the agreement.
That is why Enthec is committed to solutions like Qondar, which inform and empower. It's not about viewing the digital environment as a negative space but rather making it fairer, safer, and more humane.
Digital consent should be a free and conscious decision, not a trap camouflaged in small print.
Your data is part of you, your reflection in the digital world, and as such, it deserves to be protected. Accepting terms and conditions should not be an act of faith but a conscious choice.. You need tools that help you see beyond the click to do that.
Start protecting your digital identity today with Qondar. Analyze your exposure and take control of your privacy. Contact us and discover everything you can do.
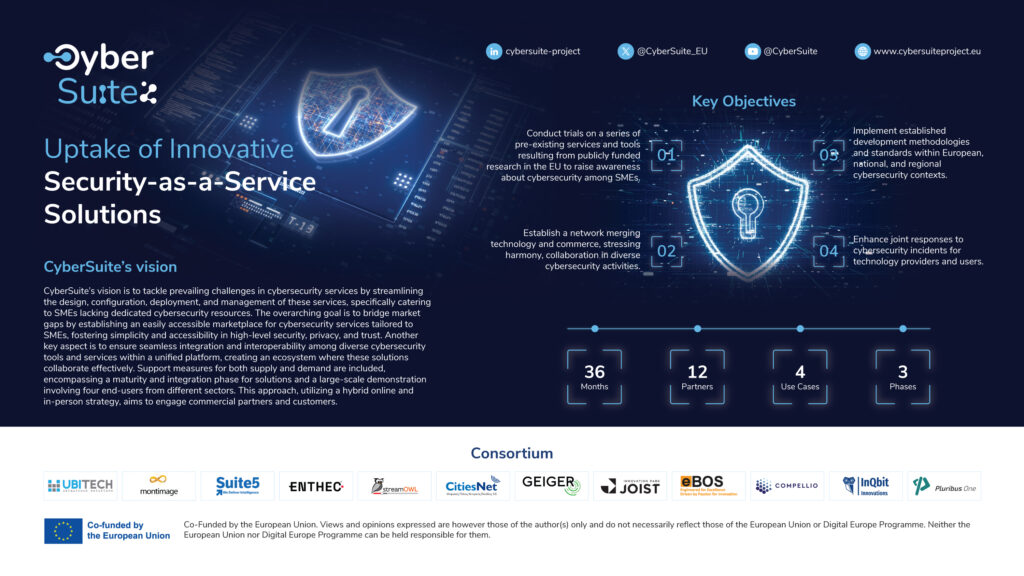
CyberSuite: Strengthening the cybersecurity of European SMEs
The 4th Plenary Meeting of the European Cybersuite Project was recently held in Basel, Switzerland, with Enthec Solutions attending as a member of the Consortium.
In today's digital universe, cybersecurity has become critical, especially for small and medium-sized enterprises (SMEs) who often lack the resources and experience necessary to protect themselves effectively. In this context, CyberSuite, a project funded by the Digital Europe Program, aims to facilitate access to advanced cybersecurity solutions for European SMEs through a Security-as-a-Service.
What is CyberSuite?
CyberSuite, a consortium formed by 12 organizations from 8 European countries, was released on January 1, 2024, and is estimated to be completed by December 2026.. This project seeks to close the gap in the cybersecurity market for SMEs through a unified platform that integrates easily accessible and manageable security tools and services.
Who is part of the consortium?
CyberSuite brings together a strategic combination of industry players:
- UBITECH Limited (coordinator, United Kingdom)
- JOIST Innovation Park (Greece)
- MONTIMAGE EURL (Francia)
- SUITE5 Data Intelligence Solutions Limited (Cyprus)
- ENTHEC Solutions SL (Spain)
- STREAMOWL IKE (Greece)
- Intermunicipal Development Company Digital Cities of Central Greece SA (Greece)
- CYBERGEIGER GmbH (Germany)
- EBOS Technologies Limited (Cyprus)
- Compellio SA (Luxemburg)
- INQBIT Innovations SRL (Romania)
- Pluribus One SRL (Italy)
This diverse group includes specialized technology companies, innovation organizations, and public entities, ensuring a comprehensive and robust approach to digital security challenges in diverse environments.
Key objectives and pillars
CyberSuite is based on six main lines of work:
- Improving the CyberSuite portfolio means enhancing the functionality of tools and services to offer competitive proposals in the market.
- DevSecOps Integration: ensuring that solutions are developed under modern secure and collaborative development practices.
- Demonstrations based on real cases: validating the platform's impact in sectors such as energy, health, mobility, and agri-food.
- CyberSuite Academy: Promoting ongoing training through an online academy that combines technical training with good operational practices.
- Building a market ecosystem: Connecting cybersecurity service providers and consumers to ensure broad adoption
- Dissemination and exploitation: Maximizing impact through communication campaigns, dissemination channels, and early activities to drive adoption.
Benefits for SMEs
The CyberSuite platform offers a security-as-a-service framework adapted to the needs of SMEs:
- Access to integrated solutions without requiring complex architectures.
- Centralized management that reduces the operational load of the equipment.
- Training and awareness through resources from the CyberSuite Academy.
- Interoperability between tools thanks to a common platform prepared to integrate with previous technologies (legacy systems).
- Real use cases, proven in key sectors, which validate the effectiveness and adaptability of CyberSuite solution
European collaborative ecosystem
One of CyberSuite's strengths is its strong commitment to European-wide collaboration. Through its ecosystem:
- It encourages open cooperation between suppliers and SMEs.
- Results from previous EU-funded research are reused, avoiding duplication and accelerating deployments.
- A critical mass adoption is generated that makes investment in cybersecurity more attractive.
- The diversity of the consortium ensures that technological, regulatory, and sector integration aspects are covered.
Expected results
By the end of 2026, CyberSuite is expected to achieve:
- A functional platform that allows SMEs to adopt advanced cybersecurity without needing large infrastructures.
- Certified and market-ready modules, with verifiable levels of maturity.
- Pilots in 4 key sectors: energy, eHealth, transportation, and agri-food.
- More than 200 users trained through the CyberSuite Academy.
- An active market of providers and consumers of security services, generating real impact on the economic fabric.
Why is the CyberSuite project important?
- Because it offers SMEs an accessible alternative to the complexity and cost of traditional cybersecurity.
- Because it creates a European collaborative environment that powers innovative solutions.
- Because it supports the digital sovereignty of the EU and avoids technological dependence on third countries.
- Because it delivers continuing education and tools that reduce long-term cyber risks.
- Because it aligns the EU with its strategic priorities regarding digitalization and technological autonomy.
Looking to the future
CyberSuite seeks to transform the cybersecurity model for European SMEs, from the technical foundation to training, including the development of a dynamic and efficient marketplace. Its collaborative approach, multidisciplinary consortium, and real-user focus make it an exemplary project for driving a more secure, interconnected, and sovereign digital Europe. Together, we are building the future of cybersecurity for SMEs.
5 essential practices for protecting databases with high-value information
Data is one of a company's most valuable assets, and protecting a database is not just a recommendation but a necessity.
Leaks, unauthorized access, and targeted attacks are commonplace, and a compromised database can result in significant financial loss or irreparable damage to a company's reputation.
Whether we're talking about financial information, personal customer data, or intellectual property, the reality is there's no room for error. Databases are the digital heart of many organizations, and understanding how to protect a database effectively has become an essential part of any serious technology strategy.
It's worth considering a tool that can make a difference in protecting a database from external threats: Kartos, developed by Enthec. Kartos is a continuous cyber surveillance tool designed for businesses and is part of the Continuous Threat Exposure Management (CTEM) approach.
Do you want to know how to effectively protect a database? Join us as we explore 5 essential practices for keeping your most valuable digital assets safe.
1. Access control: less is more
One of the basic safety rules is providing the minimum necessary access.. Not all employees or collaborators need access to the entire database. Therefore, it is essential to implement a clear and strict privilege control policy.
How to put it into practice?
- Define user profiles according to responsibilities.
- Use multi-factor authentication (MFA) systems.
- Record and review access periodically.
- Automate the expiration of temporary permits.
Misconfigured access can open a direct door to attackers.. Therefore, it is advisable to audit this aspect regularly and apply the principle of least privilege.

2. Data encryption: an extra layer that makes the difference
Although it sounds technical, data encryption simply converts said data into an unreadable format for those without the proper password. And it's one of the pillars of protecting a database.
Two types of encryption you should consider
- Encryption at rest: Protects stored data, even if the server is physically accessed.
- Encryption in transit: protects information that travels between the database and users or applications.
Both are necessary, especially if you use sensitive or regulated data (such as medical, financial, or personal identifier information).
3. Secure and frequent backups
Nobody wants that day to come… but sometimes it happens: a system failure, a ransomware attack, or an unforeseen catastrophe. And if you don't have a recent backup, the consequences can be devastating.
Good backup practices
- Automate daily or weekly backups, depending on activity level.
- Store copies in separate environments (ideally in the cloud and on-premises).
- Periodically test the restoration processes.
- Make sure your copies are also encrypted and protected.
A well-executed backup is the lifeline that allows you to recover critical information and continue operating without too many setbacks.
4. Active monitoring and incident response
A key aspect of database protection is anticipating incidents and detecting warning signs before it is too late.
Cyberattacks don't always leave visible signs. In fact, attackers often infiltrate for weeks before being detected. That's why continuous monitoring is essential to alert you to unusual behavior.
This is where solutions like Kartos come into play.
Kartos stays ahead of threats by detecting data breaches or vulnerabilities exposed in public and hidden sources on the Internet. With this information, the security team can act proactively, avoiding greater damages.
In addition, an incident response plan, which defines roles, steps to follow, and internal and external communication in case something goes wrong, is highly recommended.
Rapid detection and response can distinguish between a scare and a major crisis.
5. Updates and patches: small gestures, big impact
Many cyberattacks take advantage of known bugs in the software,which could have been avoided with a simple update. However, these tasks are often postponed due to convenience or lack of planning... until it's too late.
Tips to keep everything up to date
- Turn on automatic updates whenever possible.
- Schedule regular reviews of critical patches.
- Prioritize updates to systems that manage sensitive data.
Outdated software is like a door that is not closed correctly: It seems safe, but anyone with bad intentions can get in.
Why is it so important to know how to protect a database?
The answer is clear: because data is the new gold.. Whether you run a small business or a large corporation, risks are present, and cyber criminals are relentless. Furthermore, current legislation (such as the General Data Protection Regulation or GDPR) requires active measures to safeguard the privacy and integrity of information.
By applying these five practices, you'll be taking concrete steps to reduce your risk exposure, comply with regulations, and maintain the trust of your customers and partners.
What if you don't know where to start?
Not all companies have technical teams capable of implementing these measures independently. That's why there are solutions such as Kartos by Enthec, which allows for complete visibility of the exposure risk without the need for a cybersecurity expert.
Kartos detects vulnerabilities in real time, prioritizes threats according to their risk level, and facilitates corrective actions—all from a clear, accessible dashboard designed for informed decision-making.
Knowing how to protect a database is no longer knowledge reserved solely for technical profiles: it is a cross-cutting priority that affects the entire organization, from IT to management. It is a strategic necessity for any company that values its digital assets. With good practices, appropriate tools like Kartos, and a proactive approach, it's possible to drastically reduce risks and anticipate problems before they occur.
Don't wait for a data breach to take action. Your data's security deserves constant attention and professional solutions.
Do you want us to help you protect your most important digital assets? Contact us and start building a solid defense.